Executive ego and the Sony Pictures network hack
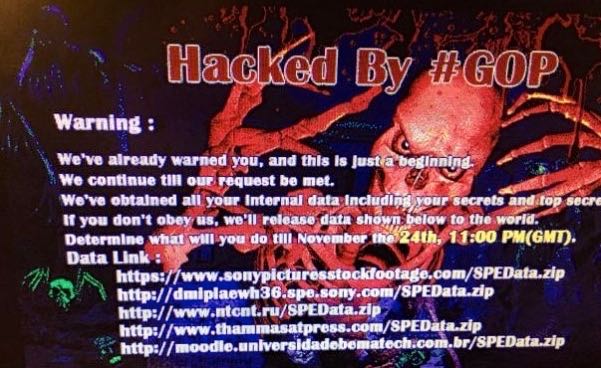
Readers have been asking me to write about the recent network hack at Sony Pictures Entertainment. If you run a company like Sony Pictures it has to be tough to see your company secrets stolen all at once -- salaries, scripts, and Social Security numbers all revealed along with a pre-release HD copy of Annie, not to mention an entire database of unhappy Sony employees who want to work anywhere Adam Sandler doesn’t. But frankly my dear I don’t give a damn about any of that so let’s cut to the heart of this problem which really comes down to executive privilege.
Sony was hacked because some president or vice-president or division head or maybe an honest-to-God movie star didn’t want something stupid like network security to interfere with their Facebook/YouTube/porn/whatever workplace obsession. Security at Sony Pictures wasn’t breached, it was abandoned, and this recent hack is the perfectly logical result.
"I used to run IT for Sony Pictures Digital Entertainment", confirmed a guy named Lionel Felix in a recent blog comment, "and (I) know that there were a number of simple vectors for this kind of attack there. They ran IT there like a big small office with lots of very high-maintenance execs who refused to follow any security protocols. I’m surprised it took this long for this to happen".
High-maintenance execs are everywhere these days. At the same time average workers regularly go for years without a raise, we seem to live in the Age of High Maintenance Execs.
I wrote a column not on ago advising that entire corporate networks should be disconnected from the Internet for security reasons. If you want to post on Facebook or email your mother, do it on your smartphone using cellular, not corporate, data minutes. Yet somehow on network after network, these simple measures aren’t taken.
Let me get excruciatingly specific: in the case of nearly all the recent high profile corporate data breaches in the USA, the primary ISP involved was AT&T. This is not an indictment of AT&T at all, just the opposite. As far as I can tell AT&T did nothing wrong. But in every case I’ve looked at, AT&T customers effectively sabotaged their own security.
AT&T is the only ISP I know of that segregates its Multi-Protocol Label Switching (MPLS) private networks from Internet access. The client has to very specifically bridge the two to get to the Internet and they do it all the time. For AT&T this is an immutable law -- no private MPLS service has connectivity to the Internet. If you want Internet you order a second pipe. Yet Home Depot, JP Morgan, and Target all use the AT&T MPLS service so they specifically allowed their private networks to be bridged to the public network.
The bad guys were kept out until that happened.
This behavior goes against every classic IT rule of thumb except one. IT rule #1 is Hell no we can’t do that. There’s a long tradition of saying No in IT, yet here it didn’t happen. Rule #2 is we’ll need a lot more money and bandwidth to do that. Given AT&T’s position on the matter it should have been easy to score the required second pipe for Internet traffic, yet somehow it didn’t happen. Only Rule #3 -- Thank you sir, may I have another -- seems to have held, and therein lies the basic problem that IT can no longer stand up to executive management’s need for Twitter.
From where I sit it looks like the 500 million US financial records lost to hackers over the past 12 months come down mainly to executive ego. All these companies opened a door to the Internet so employees could do banking, listen to Internet radio, check their Gmail, and all allowed their businesses to be robbed in the process.
So get a 4G phone and leave the corporate network alone. If you must offer Internet, BYOD over a guest network connected locally via DSL.
You can build an IP-to-IP network with low-cost Internet. The difference is that you remove the default route to the Internet and remove NAT’ing for Internet access. Simply allow static routes that connect only to other office routes. Even if bad guys attack the network public IP address the router cannot reply because the route is not in the route table. Without NAT no user in the RFC 1918 IP subnets can access anything anyway. All traffic is routed over the encrypted VPN tunnels. Internet is at the hub points -- it is there that you decide if you want to open your network to the world. I vote no.
Yet these companies didn’t take the relatively simple steps needed to secure their data. Your company probably hasn’t, either.
Now folks at Google and Yahoo and other outfits that actually require the Internet to do business might see this somewhat differently. For that matter, I like paying my electric bill online and I’m sure the power company doesn’t mind getting money that way. So it’s not entirely simple. But what we’ve done is assume VPNs or https can handle everything when that’s just not true.
We need better rules about how to segregate traffic and design safer networks. And even faced with executive tantrums, IT has to be (re)empowered to just say no.