How shadow IT threatens the enterprise and what to do about it

Increasing adoption of BYOD and use of mobile devices means that employees have the ability to access business data from anywhere. However, this can come into conflict with company security policy.
Policies are often seen as too invasive, hard to understand and not always in tune with how employees work. This can lead to workers finding their own alternative solutions. Companies need to come up with strategies that safeguard data in use, in transit and at rest to let employees focus on their work.
Business technology specialist Citrix has produced an infographic looking at the rise of shadow IT and how businesses can get to grips with it.
Among the findings are that 36 percent of employees often ignore company security policies because they’re too strict. Less than half of employees say they've been trained in ways to stay secure at work and less than two-thirds say they know what to do if they suspect a security breach. Productivity Apps like Mail are among the top items blacklisted by IT, revealing employee tendencies to bring in personal apps used outside work.
Enterprises can tackle the problem by implementing best practices such as controlling access to sensitive data, educating users in the potential risks, and using technologies like containerization and virtualization to protect data both in transit and at rest.
You can see the full infographic below or read more by visiting the Citrix blog.
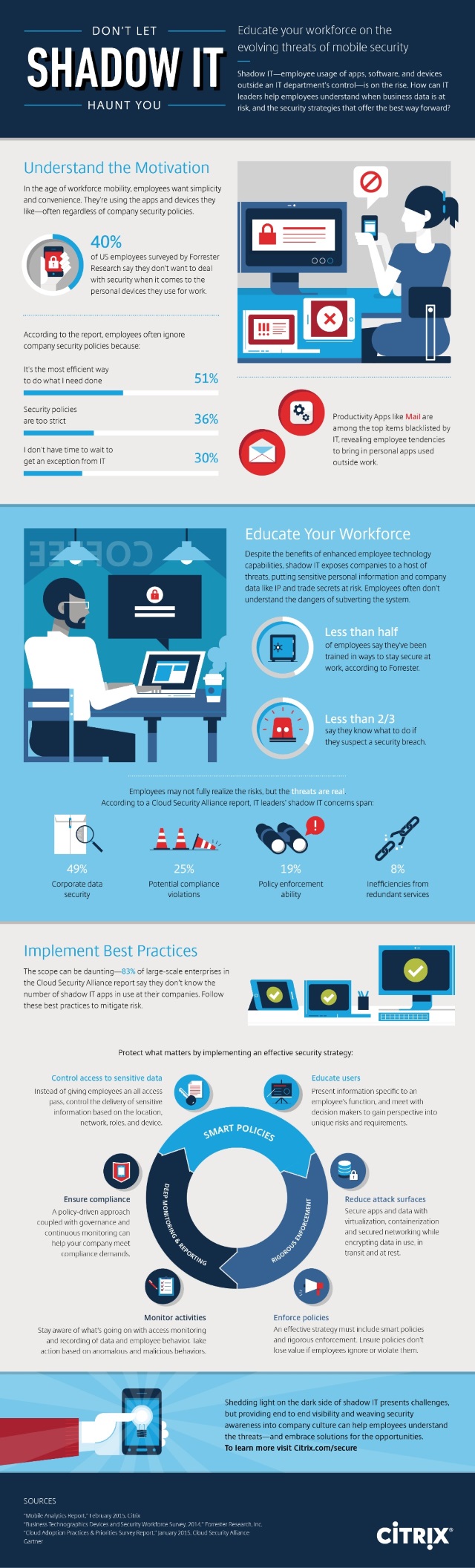
Photo Credit: Hans-Joachim Roy/Shutterstock