Social engineering tops the hacking pops

Hackers are constantly seeking new ways to attack systems and gain insider access to data. A new survey from IT security company Balabit reveals the 10 most popular hacking methods to help companies understand how to protect themselves.
The survey of almost 500 IT security practitioners reveals that social engineering is the most popular means of attack. Hackers aim to get a 'low level' insider user account by means of phishing and escalate its privileges.
"Traditional access control tools and anti-malware solutions are necessary, but these only protect companies’ sensitive assets while hackers are outside of the network," says Zoltán Györkő, CEO at Balabit. "Once they manage to break into the system, even gaining a low level access, they can easily escalate their rights and gain privileged or root access in the corporate network. Once it happens, the enemy is inside and poses a much higher risk as they seem to be one of us".
Compromised accounts, such as those with weak passwords, is the second most popular route. If users have the same password on work and personal accounts the attacker only needs to discover one, from a social network account say, to open up corporate systems.
Third place is taken by web-based attacks such as SQL injections. The quality of code in many applications is still questionable from a security point of view, and there are many automated scanners from which attackers can easily detect vulnerable applications.
"The highest risk to corporations is when outside attackers gain insider access, as they can stay undetected within the network for months," says Györkő. "Balabit aims to support organizations to know their enemy by knowing who is behind their user accounts, and determining whether it is a legitimate user or a masked hacker. This should be the fundamental priority in every kind of organization's IT security strategy".
You can see the full top 10 in the infographic below.
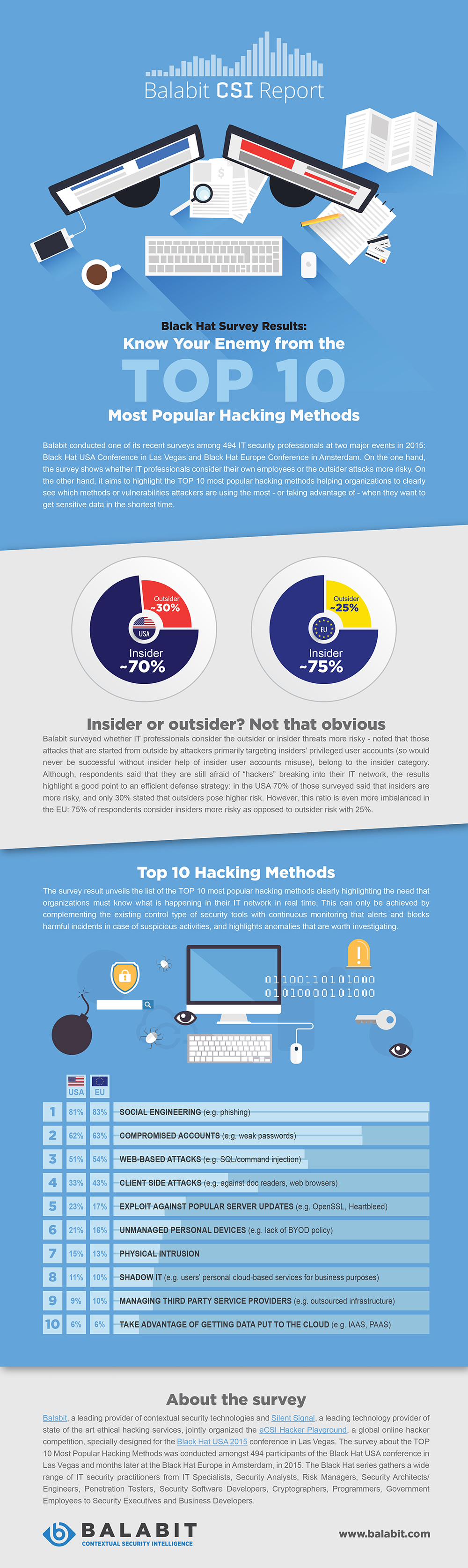
Photo Credit: igor.stevanovic/Shutterstock