KeySteal: huge macOS vulnerability can be exploited to reveal keychain passwords
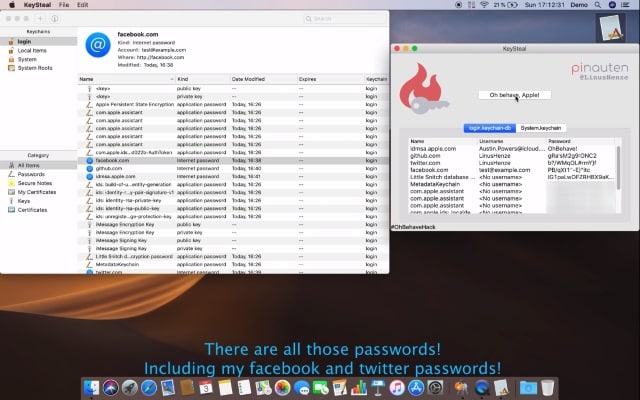
A disgruntled security researcher has revealed a one-click exploit that takes advantage of a macOS vulnerability to reveal all of the passwords stored in a Mac's keychain.
Linus Henze developed an exploit tool called KeySteal that uses a 0-day bug to extract keychain passwords on macOS Mojave and older. He stresses that neither root access nor administrator privileges are required, and no password prompts are generated by the tool. Henze is not going to help Apple to fix the problem because the company does not offer a bug bounty program for macOS.
See also:
- Cisco joins Apple in calling for a US version of GDPR data protection and privacy laws
- Apple apologizes for privacy-invading FaceTime bug, promises delayed software update
- Massive FaceTime privacy bug lets people eavesdrop on audio and video calls before they've been answered -- and Apple doesn't have a fix yet
Henze is a familiar name, and he is responsible for previously revealing iOS vulnerabilities. As noted by 9to5Mac he "has a track record of credibility".
The exploit he has created is such that it does not matter if System Integrity Protection is enabled, or Access Control Lists are set up. It is capable of extracting passwords from the Login and System, but not the iCloud Keychain.
Henze posted a video of the tool he has created to YouTube, of which he says:
I'll show you a 0day exploit that allows me to extract all your (local) keychain passwords on macOS Mojave (and lower versions). Without root or administrator privileges and without password prompts of course.
This is not the first time. You might remember KeychainStealer from @patrickwardle, released 2017 for macOS High Sierra, which can also steal all your keychain passwords. While the vulnerability he used is already patched, the one I found still works, even in macOS Mojave.
He adds:
I won't release this. The reason is simple: Apple still has no bug bounty program (for macOS), so blame them.
Check out the video below to see the exploit in action:
Apple is yet to comment.