Cyberwarfare incidents reported by almost half of UK firms

New research shows that 49 percent of UK businesses have reported cyberwarfare incidents to the authorities.
The report from Armis also shows 52 percent of UK IT leaders believe the government can't defend its citizens and enterprises against an act of cyberwarfare.
Ransomware, meet DRaaS: The future of disaster mitigation

Picture this: It’s 2031, and you’re chief information security officer (CISO) at a Fortune 500 company. Alongside many other innovative and emerging threats, you’re constantly battling AI-empowered bad actors. In fact, you spend the majority of your working hours combating emerging forms of ransomware. These dangerous incursions occur once every two seconds -- more than 43,000 attacks every day -- and all organizations are extremely vulnerable.
Although harsh, this scenario may soon become a reality. Threat actors are learning to use more refined tactics to infiltrate valuable consumer data, and it’s paying dividends. In 2023 alone, ransomware attacks increased by 68 percent.
Get 'Modern DevOps Practices -- Second Edition' (worth $39.99) for FREE

DevOps and the cloud have changed how we look at software development and operations like never before, leading to the rapid growth of various DevOps tools, techniques, and practices.
This updated edition of Modern DevOps Practices helps you pick up the right tools by providing you with everything you need to get started with your DevOps journey. The book begins by introducing you to modern cloud-native architecture, and then teaches you about the architectural concepts needed to implement the modern way of application development.
Number of ransomware victims up 20 percent in first quarter of 2024

A new report shows a 20 percent year-on-year increase in the number of ransomware victims, along with major shifts in the behavioral patterns of ransomware groups.
The Q1 2024 ransomware report, from the GuidePoint Security Research and Intelligence Team (GRIT), finds the number of active ransomware groups more than doubled, increasing 55 percent from 29 distinct groups in Q1 2023 to 45 distinct groups in Q1 2024.
Low-code tools boost developer productivity

Over 90 percent of respondents to a new survey say that low-code tools have boosted developer productivity in their organizations. 43.5 percent of developers are saving up to 50 percent of their time when they use low-code tools on a project.
The 2024 Reveal Biggest Software Development Challenges survey, finds that 28.2 percent of software developers' time is dedicated to coding, compared with 43.4 percent of their time the previous year.
Cisco warns of serious CLI command injection vulnerability in its Integrated Management Controller

A serious security vulnerability exists in Cisco Integrated Management Controller (IMC) which can be used by an attacker to elevate privileges to root.
The company has issued a warning about the vulnerability and acknowledged the availability of proof-of-concept exploit code for it. The high severity warning is accompanied by the release of patches, as well as a note that there is no workaround other than a software update.
The next Bitcoin halving is imminent and price volatility is likely

For only the fourth time, there is a Bitcoin Halving on the horizon. Occurring -- roughly -- every fours years, the first took place in November of 2012, the second in July of 2016, and the third in May of 2020. The next is due on April 19 or 20.
The exact date and time is not known as a halving takes place every 210,000 blocks, and it is a mechanism designed to make Bitcoins rare. But just what does it mean in practice for both miners and investors? While it is hard to predict precisely what will happen, market volatility is likely to be the order of the day.
The stunning Windows 13 -- yes, 13! -- is the Microsoft operating system we want
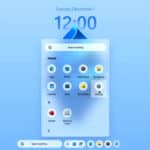
Microsoft plans to phase out support for Windows 10 soon (unless you pay, of course), leaving users with the option to either upgrade to Windows 11 or wait for the anticipated successor, likely to be Windows 12.
Although Microsoft hasn't officially announced that next-gen operating system yet, it has dropped plenty of hints, and there’s a good chance it will come jam-packed with AI functionality, as that is clearly where the operating system -- and the company -- is headed.
Microsoft tries to calm fears after Edge update also appeared to install Copilot in Windows Server

Microsoft caused concern when it released an update to its Edge browser. Despite having decided not to add its AI-powered assistant Copilot to Windows Server 2025 because of complaints from admins, users were upset to find that Copilot suddenly appeared in the list of installed apps for Windows Server 2022.
What's going on? Nothing sinister, insists Microsoft. The company has scrabbled to calm the fears of administrators saying that while a package called "Microsoft chat provider for Copilot in Windows" may well show up, Copilot has not actually been installed and it is not collecting any data.
MenteeBot is an AI-powered humanoid robot coming to your home and workplace in 2025

Mentee Robotics has pulled back the curtain on MenteeBot, a personalized humanoid robot that fully integrates AI across all operational aspects.
Founded in 2022 by AI experts, Mentee Robotics has been working quietly behind the scenes for the past two years. The company’s prototype humanoid robot represents a full end-to-end operation cycle, from verbal command recognition to complex task fulfillment. This includes advanced feats such as navigation, locomotion, scene understanding, object detection, localization, and natural language understanding.
CISOs not changing priorities in response to AI threats

A new report by ClubCISO in collaboration with Telstra Purple finds that despite significant concerns around the impact of AI cyberattacks, many organizations have not seen their priorities or investment plans change.
Of CISOs surveyed 63 percent rate the severity of the threat posed to their businesses by AI cyber-attacks as critical or high, with 63 percent also suggesting that AI cyberattacks will be extremely damaging to businesses.
80 percent of companies don't have sufficient cyber insurance

According to a new report, 80 percent of insured companies that have suffered a data breach didn't have sufficient coverage for the incident.
The study, from cybersecurity optimization platform CYE, finds the average coverage gap is 350 percent, which means that more than 75 percent of the incident was not covered.
Get 'Windows Server 2022 & PowerShell All-in-One For Dummies' (worth $30) for FREE

Looking for a little help installing, configuring, securing, or running a network running Windows Server 2022? Windows Server 2022 & PowerShell All-in-One For Dummies delivers a thorough guide to network administration in a single, convenient book.
Whether you need to start from scratch and install a new server or want to jump right into a more advanced topic like managing security or working in Windows PowerShell, you'll find what you need right here.
Cybercriminals take aim at ERP apps

Many enterprises rely on some sort of ERP application for their business operations and decision making. The vast majority of large organizations use ERP applications from leading vendors like SAP and Oracle.
New research from threat data and intelligence leader Flashpoint and ERP cybersecurity and compliance leader Onapsis reveals evidence that SAP business-critical applications are increasingly in the sights of and valuable for cybercriminals.
Google Drive finally gets dark mode on the web
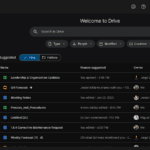
It has been an extraordinarily long time coming, but Google has finally decided to flip the switch on dark mode for Drive on the web.
Much like AI is at the moment, the spread of a dark mode option for apps and websites was something of a cultural and technological phenomenon a few years ago. Quite why it has taken Google such a long time to jump back on this particular bandwagon is anybody's guess, but dark mode will be welcomed by Google Drive users none the less. Here's what you need to know.
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.




