
How to prepare for the new PCI DSS 4.0 requirements [Q&A]
The Payment Card Industry Data Security Standard (PCI DSS) turns 20 next year and has remained largely unchanged during that time. But version 4.0, due to become mandatory from April 2024, will bring the standard bang up-to-date and usher in a number of big changes.
We spoke to Phil Robinson, principal consultant and QSA at Prism Infosec, to explore what's changing and how organizations can prepare to meet the new requirements.

Unlocking business potential through outcome-based security [Q&A]
Traditionally, organizations have focused on measuring the results of their cyber security strategies in terms of threat events or security incidents to determine how effective their security controls are.
However, in today's fast-paced world, the real game-changer is aligning security outcomes with business objectives and this is where 'outcome-based security' plays a huge role. It's a shift in focus for organizations, but one which can empower security teams to add even greater value to the strategic goals of the business.

What enterprises need to know about cybersecurity compliance [Q&A]
Just as cybersecurity threats are constantly evolving, so are the compliance regulations that organizations must follow. And as these regulations tighten so the risks of non-compliance become higher.
Cam Roberson, VP at Beachhead Solutions, a provider of cloud-managed PC and mobile device encryption, security, and data access control, sat down with us to discuss what enterprises need to know about the current state of cybersecurity compliance.

Why cyber risk assessment is critical to staying ahead of threats [Q&A]
The cybersecurity landscape is changing all the time and security teams are constantly searching for anything that can give them an edge in defending their systems.
We spoke to Rajeev Gupta, co-founder and chief product officer at insurance specialist Cowbell Cyber, about cyber risk assessment and how it can help businesses understand their level of risk and improve it to stay ahead of bad actors and threats like phishing attempts.

Improving data analysis with AI [Q&A]
Generative AI is making its presence felt in more and more areas, but there are well-founded concerns about the accuracy of information that it provides.
Is it possible to provide the convenience of a large language model AI system, with the logic and accuracy of advanced analytics? Arina Curtis, CEO and co-founder of DataGPT, thinks so. We spoke to her to find out more.

Improving visibility into end-user computing [Q&A]
In the wake of the coronavirus pandemic we've seen greater focus on workplace flexibility with many employees being in the office for fewer days each week.
But to make this work, enterprises must be able to track the state of their end-user computing to understand their access, performance and user satisfaction.

The ERP challenges that are keeping security teams up at night [Q&A]
Data is the lifeblood of modern business and enterprise resource planning (ERP) systems are where it's likely to live. ERP software integrates data and business functions across departments like finance, manufacturing, marketing, sales and more, and of course this makes it an attractive target for cyber criminals.
So what threats do ERP systems face and what can enterprises do to defend against them? We spoke to Kellie Synder, CCO of Onapsis, to find out.

How AI is changing the way developers work [Q&A]
The fear of software developers losing their jobs to AI is a concern for many people in the industry, but are these fears really justified?
Mike Loukides, VP of emerging tech content at O'Reilly Media, believes that AI can enhance the developer role rather than replace it. We spoke to him to find out how, with the right tools and training, the endpoint of this AI revolution won't lead to unemployment, but rather to better software.

How AI is changing the telecoms industry [Q&A]
The transition to cloud and SaaS use, along with the recent move towards remote and hybrid working, has placed increased pressure on the telecoms industry. At the same time, it has unlocked a significant opportunity for telcos, as remote work has placed a premium on services like fiber and broadband.
Increased data volumes place additional demands on infrastructure and drives up costs. We talked to Anthony Behan, managing director for communications, media and entertainment at Cloudera to discuss these developments and how artificial intelligence is helping telcos to adapt.

Why identity security could be the Achilles heel of your business [Q&A]
Most successful cyberattacks rely on compromised identity or social engineering. Yet this can be a major blindspot for enterprises with basic awareness of the problem lacking and a growing number of personal devices used for work.
We spoke to Jim Taylor, chief product officer of identity platform RSA, -- which recently published a report on the issue -- to learn more about the problem and how it can be addressed.
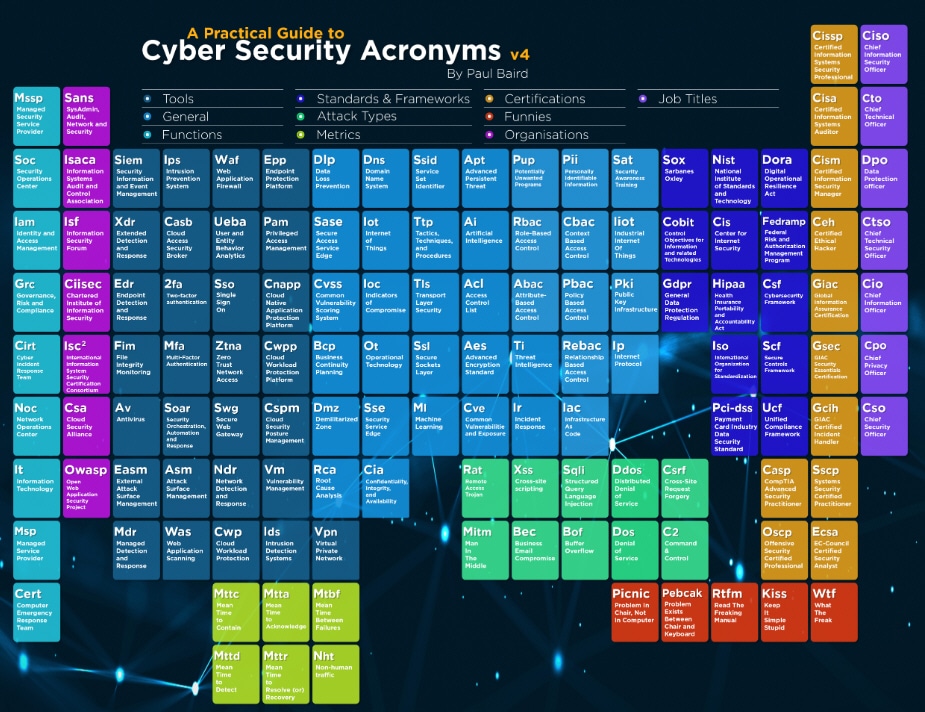
Making cybersecurity elementary [Q&A]
There are so many terms and acronyms used in the cybersecurity sector that it can be a little overwhelming at times, even for people who work in the industry.
Paul Baird, director of cyber security operations and engineering at Advanced Software and fellow at the Chartered Institute of Information Security (CIISec) has produced a round up of all the terms that you might ever need to know in the security space in a format based on the periodic table of elements.

Verified randomness -- what is it and why does it matter? [Q&A]
Much of the online world relies on things being random. Gamers trust that their players re-spawn at completely random locations, similarly, gamblers trust that online slot machines are giving them random outcomes.
Ensuring things are properly random is also important for things like decentralized finance and blockchain transactions. But how can you be sure that something is properly random?

How to reduce generative AI's risks to data [Q&A]
Generative AI models like ChatGPT are creating a lot of enthusiasm for what they can do for businesses, but they are generating just as much fear over what can go wrong with the data they handle. There is a lack of trust between large companies that have the data and the AI startups that want to use them.
What can we expect to see in the near future? We spoke with Katy Salamati, senior manager of the advanced analytics lifecycle at SAS, to find out.

How 5G is set to transform the way businesses connect [Q&A]
The rollout of 5G will speed up mobile communications and also enable more computing tasks to be carried out at the edge.
For businesses it presents the opportunity for a greater understanding of customer patterns and infrastructure needs. We spoke to Chris Gehlen, CEO and co-founder of SaaS/NaaS cloud platform Neutroon, to learn more.

What is a vCISO and why would you want to hire one? [Q&A]
As the profile of cybersecurity has increased within enterprises, so has the challenge of finding people to fill senior roles and then hanging on to them.
Recent research suggests that CISOs don't stay in the job for more than three years on average. One answer is to use a virtual CISO (vCISO) to advise on current issues and relieve the strain on the in-house team.