
EFF slams HP's printer DRM that forces the use of official ink cartridges
A few days ago, HP upset printer owners by issuing a software update to block the use of third-party cartridges. The beauty of third-party ink cartridges is, of course, that they cost a fraction of official ones, but HP didn’t like the idea of missing out on income and decided to implement DRM to block them.
The company has described the move as a way "to protect HP's innovations and intellectual property" but printer owners see it as little more than a money grab. Digital rights group EFF (Electronic Frontier Foundation) is similarly irked and has written to HP president and CEO Dion Weisler to express its alarm. There is particular concern that "HP abused its security update mechanism to trick its customers".
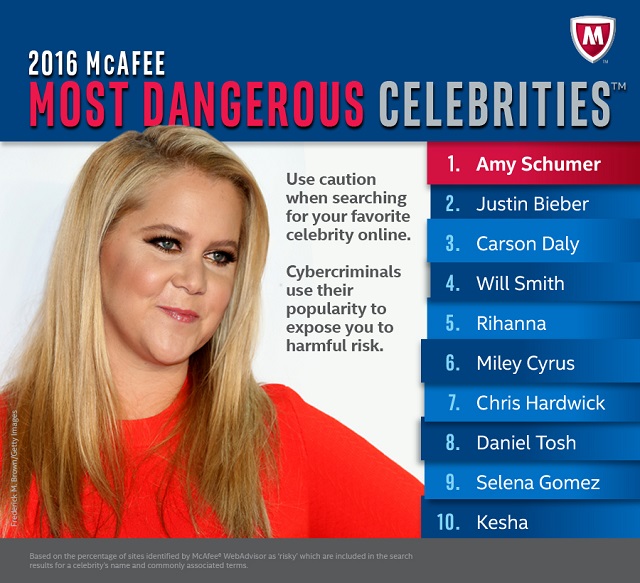
Amy Schumer and Justin Bieber top the 2016 McAfee 'Most Dangerous Celebrities' list
When people think of online malware, they sometimes think infections only come from 'bad' websites, such as pornography and warez. Yeah, those types of sites can definitely house malware, but so can any site. In fact, bad guys will often target users through seemingly wholesome places, where a person may let their guard down.
Today, McAfee announces its annual 'Most Dangerous Celebrities' list. No, the celebrities themselves are not a danger to the public -- as far as I know, at least. Actually, these are people that, when their names are entered as search terms, can cause an increased chance of leading to malware. For 2016, McAfee lists Amy Schumer as the most dangerous in this regard.

Yahoo is still vulnerable
The first thing you should do after getting your home or apartment robbed is, obviously, change the lock. Yahoo doesn’t seem to think so, as the same practices that were in place when it got breached are still being used according to a new report by Venafi.
What’s more, its practices have for years been known as unsecure. Venafi puts it simply: if you’re a Yahoo user, you should be worried about this. Here’s what it did (or, didn’t do): most importantly, 27 percent of certificates on external Yahoo sites haven’t been changed since January 2015.

CipherLoc aims to fix 'broken' encryption
Companies are turning to encryption in order to protect their sensitive data, but many of the systems used can be cumbersome and don't necessarily offer total protection.
CipherLoc Corporation is launching a suite of data security solutions that eliminate the flaws and inadequacies in today’s encryption algorithms, adding an extra layer of protection to existing products, services, and applications.

Updated DRM platform helps protect sensitive enterprise data
Leakage of data, whether due to the action of hackers or simple error by insiders is a major problem for enterprises.
File security specialist FinalCode is launching a new version of its DRM platform to help businesses secure data both inside and outside the organization.
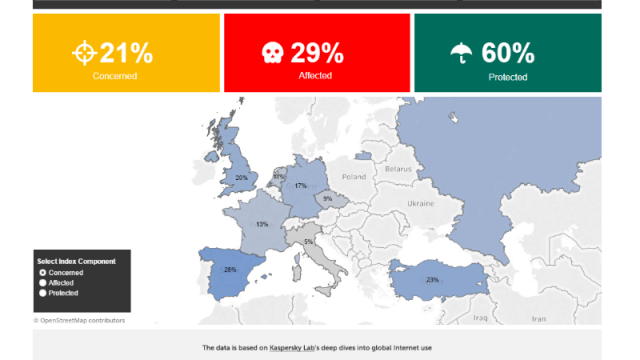
Few users are concerned about their online security
Just 21 percent of Internet users feel threatened by anything online, including malware, viruses, fraud, etc. At the same time, 29 percent have actually fallen victim to cybercriminal schemes, out of whom eight percent have had an account hijacked, and 22 percent have had malware on their devices.
On top of it all, a total of 60 percent of all people online use protection, in form of a cybersecurity solution for all devices accessing the internet. These figures were unveiled by Kaspersky Lab which has, together with B2B International, released a report on the current level of cyberthreats faced by internet users, called Kaspersky Cybersecurity Index 21 – 29 – 60.

Microsoft takes security to the Edge with Windows Defender Application Guard
With many cyber attacks now initiated through the browser, endpoint security is something all businesses need to take seriously.
Among today's announcements at Ignite, Microsoft trailed security enhancements across a range of its products, including the Edge browser. Windows Defender Application Guard will be available to Windows 10 Enterprise users from next year and aims to make Edge the most secure business browser.

Russian hacker collective targets over 85 leading US companies
A group of hackers speaking Russian and using Russian servers are out hunting for American companies' user credentials, an exclusive story published on The Epoch Times claims.
This group, allegedly not tied to any government and basically operating on its own, is targeting "at least" 85 companies, including Amazon, American Airlines, AT&T, Best Buy, Wells Fargo, DropBox, Dunking Donuts, Ebay, GoDaddy, Uber, Match.com, McDonald’s, Office Depot, PayPal, Pizza Hut, Steam, and Apple Pay.

Hackers compromise nearly 16,000 WordPress websites
According to security researcher Daniel Cid, at least 15,769 WordPress websites have been compromised this year by cyber-attackers who were able to evade Google's Safe Browsing checks.
WordPress is the most popular content management system in the world, used by consumers and businesses to create and publish blogs. To conduct the research needed for the second 2016 Sucuri report on compromised web properties, 21,821 sites were studied with the majority of them using WordPress to manage and publish their content. The report also found that 3099 Joomla! sites were hacked during that time as well.

When is stupidity fraud?
Next month I return from my first—and hopefully last—summer sabbatical. I resume writing with a question for you: "When is stupidity fraud?" I ask because someone is using my gmail address to sign up for a humungous number of newsletters and websites. At first, I presumed someone trolled me. But that no longer appears to be the case. This guy, presumably living in North Carolina, either uses my address randomly to hide his identity, or he mistypes one that is similar. Given many of the services are for an unidentified widower looking for love, I assume the latter.
Behind my question are real concerns about identity and privacy that do not just apply to me. The email address gives me the ability to change the passwords and even cancel accounts—both of which I have done, treating his misuse of my email address as identity theft and violations of my privacy; after years of careful cultivation that reduced spam, crap is on the rise as this misuse spreads my gmail identity across dating and discount sites and sex webcams. Who knows on what mailing lists it will appear next.

Pippa Middleton is the latest celebrity to suffer an iCloud account hack
There have been numerous cases of iCloud accounts being hacked over the years, but it's the celebrity ones that hit the headlines. Well, that and things like the Fappening. The latest celebrity account to fall victim to hackers is Pippa Middleton, sister of British royal Kate Middleton, the Duchess of Cambridge.
A reported 3,000 images have been stolen from Pippa's account, and these are said to include photographs of Kate and her children. Leaked images also show photos from private parties, and shots of wedding dresses.

Most employees don't want to share passwords
For many people, both business owners and employees, remote working is the future of business. It’s at the very heart of business transformation, together with cloud computing, automation and artificial intelligence. However, a new poll by OneLogin seems to suggest that certain workers aren’t really fond of the idea of remote working.
Half of full-time workers believe employees below mid-manager level shouldn’t be allowed remote access to the corporate network. This remote access refers to both work-owned devices (47 percent) and private devices (54 percent).

Knowing your unknowns
On a daily basis, the news is filled with stories about things that "should never have happened". Last weekend’s headline, "Improvised Explosive Device Explodes in New York City’s Chelsea Neighborhood", is one tragic example. No one could have anticipated the attack, but through the use of cameras placed throughout the area, law enforcement was able to identify a suspect and track his movements within hours.
In the real world, no one can know every single threat that could exist in the future, or when it might happen. You can make educated guesses with the right intelligence and data, but you can’t predict with certainty. This is why New York, London, and other metropolitan areas have installed surveillance cameras. They’ve done this so that if a situation does unfold, they can quickly triage and provide authorities with immediate and accurate information to inform response and investigation.

Leaked credentials affect the largest 1,000 organizations worldwide
Data breaches have become the norm in recent years with 2014 earning the nickname the "year of the data breach" and 2015 being known as the "year of the breach". So far in 2016, even more data breaches have been made public, including LinkedIn, MySpace and Dropbox and we will likely see more before the year comes to a close.
For companies, being the victim of a breach is unnerving enough, but there also implications to their reputation, brand and finances. However, breaches also have an indirect impact on organizations and some end up facing the "collateral damage" of such an attack for some time after the initial breach.

Healthcare, Telecommunications, Retail and Transportation: How do they stack up on security awareness?
Breaches and attacks have run rampant through most major industries, and organizations are beginning to realize the importance of employee and stakeholder security awareness. Healthcare and retail have been in the brightest spotlights with the rise in ransomware and credit card data breaches in the last couple of years, but they are not the only ones facing this challenge. Wombat Security's Beyond the Phish report found that telecommunications and transportation industries also struggle with a wide range of security issues.
Ultimately, an organization can improve its defenses by elevating the level of security best practices across its employees and addressing the biggest offending categories of awareness.