
Mass registration of fake online shops originates from China
A new campaign uses mass registration of fake online shop domains to impersonate legitimate retailers, facilitate financial fraud, and in certain instances, distribute malware through counterfeit checkout systems and redirect payloads.
Identified by the research division of BforeAI, analysis of the campaign’s registration and DNS telemetry indicates a well-structured operation with distinct clusters, primarily originating from Chinese infrastructure providers and utilizing domain privacy services to obscure attribution.

Citizen developers dominate, the rise of AI, code as the new Latin -- development predictions for 2026
Software development, perhaps more than any other area of IT, has seen a major impact from the rise of AI. It’s become easier for anyone to develop apps but that doesn’t come without risks.
Industry experts look ahead to what we can expect to see in the development space, from AI and more, as we head into 2026.

Governing AI where work actually happens [Q&A]
Enterprises are rushing to embrace AI copilots and browser-based assistants, but most struggle with governing how employees actually use them. Sensitive data gets uploaded, prompts leak strategy, and risky extensions run unchecked, all outside the reach of traditional network or app-layer controls.
We spoke to Michael Leland, field CTO at Island, to discuss why the UI surface is becoming the most strategic security layer as SaaS and AI copilots flood enterprise workflows.

Practical quantum, encryption risk and government regulation -- quantum computing predictions for 2026
It’s the time of year again when industry executives like to peer into their crystal balls and try to predict what the future might hold.
We’ll kick off this year’s roundups with a look at quantum, something which has been hovering on the edge a major breakthrough for a few years now but, so far, has always seemed to be just out of reach from a commercial perspective. Is that set to change in 2026?

Chainguard aims to improve stewardship of mature open source projects
What happens to open source projects when they reach maturity? When a project has fulfilled its purpose and become foundational to customer workloads, it no longer requires a roadmap of sweeping changes. What it needs is safe, predictable maintenance after the creators have moved on.
However, it remains essential that stays OSS safe and supported when its maintainers are ready to step away, or the project no longer needs constant upkeep. To address this challenge Chainguard is launching EmeritOSS, a model for supporting mature open source projects and long-term OSS sustainability for the community.

Zencoder aims to end vibe coding and bring engineering discipline
While chat interfaces have popularized AI coding, uncoordinated agents can produce ‘slop’ -- code that looks correct but fails in production or degrades with iteration.
To address this problem Zencoder is introducing its new Zenflow app, a free orchestration platform designed to transition the industry from ‘vibe coding’ to AI-first engineering.

Almost half of Gen Z hide their AI use at work
A new survey shows that nearly half of Gen Z workers (48 percent) quietly keep their AI use under wraps -- roughly in line with the 45 percent of all employees who say the same.
But the research from Slingshot finds that, unlike their older colleagues, Gen Zers (ages 18-28) conceal their AI use because of concerns about being judged (47 percent) or that it will be seen as cutting corners (44 percent).
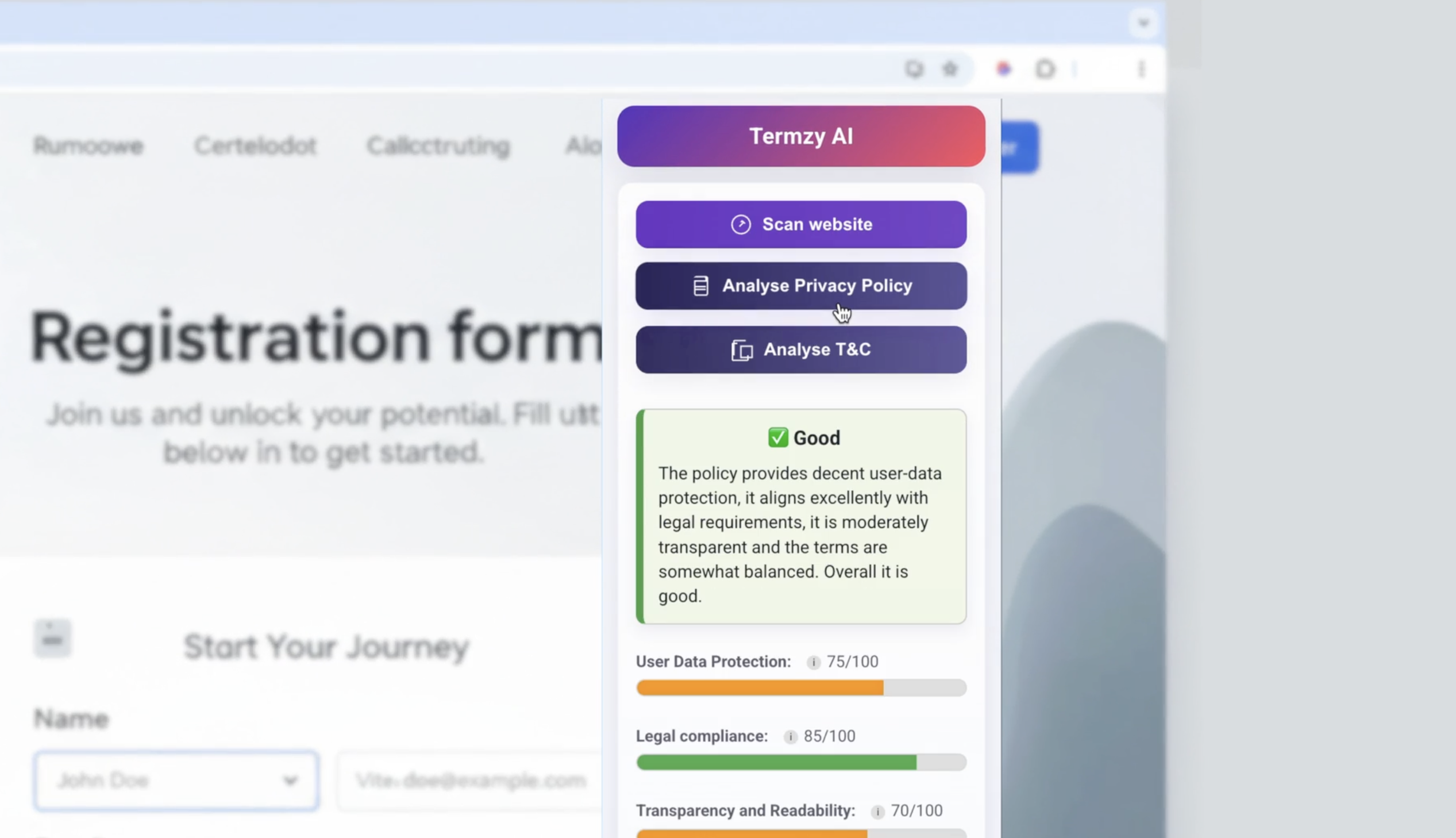
Don’t waste time reading T&Cs -- AI can do it for you
Be honest now, do you really read T&Cs, privacy policies, etc when signing up to a service? Of course you don’t, you just scroll to the bottom and click Accept, trusting that you haven’t just handed over your first born child to a social media mogul.
Step forward Termzy AI, an AI tool that can scan those pesky T&Cs for you and alert you to any problematic things lurking in there that you might be agreeing to.

AI and automation feed rise in holiday scams
The holiday season has long been a peak time for scammers as much as it has for retailers. But new research from Check Point Software reveals how AI and automation are fueling the biggest surge in holiday scams ever recorded.
The study shows over 33,500 Christmas-themed phishing emails flagged in just 14 days and over 10,000 fake social media advertisements being created daily. This is coupled with fake retail sites and social media giveaways surging around the globe.

Why silos restrict scale -- and what to do about it [Q&A]
Silos, you might think, are bit of a niche issue. They arise when old practices become entrenched, or when tools are only used by one part of the organization.
But Shannon Mason, chief strategy officer of Tempo Software, argues silos are actually a major roadblock to growth, agility, and strategic alignment. We spoke to her to find out about the hidden cost of silos and the concrete steps teams can take to break them down.

Financial sector hit hard by breaches but ransomware seeks targets elsewhere
The banking, financial services and insurance (BFSI) sector has been the most targeted in 2025 accounting for 17.8 percent of all incidents (172 incidents out of 966) tracked in Cyble’s latest North American Threat Landscape Report.
The report describes a mature leak economy where a small cluster of prolific actors generate many listings, supported by a large ‘long tail’ of smaller sellers -- meaning BFSI data can be sourced by both major brokers and many opportunists.

Over a third of US adults now use AI every day
ChatGPT burst onto the scene just three years ago, but a new survey reveals that 34 percent of US adults now use AI platforms daily, and nearly half say they’re using them more than they were a year ago.
The survey, of over 1,000 from US adults, from Tinuiti shows that Gen Z and millennials are leading the AI charge. 67 percent of both groups use AI at least weekly. Platforms like ChatGPT, Google Gemini, Character AI, and Sora are carving out generational niches.

One in 25 digital identity checks flagged as fraudulent
Regulatory tightening across the EU and UK, including the EU’s new anti-money laundering package and platform-economy rules, as well as emerging age-assurance requirements around online safety, have pushed organizations to formalize identity checks at scale.
But identity verification provider Veriff has published its 2026 Identity Fraud Report, showing that 4.18 percent of all digital identity checks processed through its platform in 2025 were flagged as fraudulent – the equivalent of one in every 25 verification attempts across its global dataset.

How self-governing identity infrastructure can streamline policy enforcement [Q&A]
Managing identity is one of the more challenging cybersecurity tasks and can soak up a good deal of time and resources.
We spoke to Raz Rotenberg, co-founder and CEO of Fabrix Security, to discuss the rise of self-governing IAM systems that don’t just enforce policy -- but continuously adapt, reason, and remediate access in real time.

AI use grows in the workplace but organizations struggle to secure the human element
A new report reveals that security leaders are facing increased pressure in managing behavioral cybersecurity risk as the workforce transforms to include AI.
The study from KnowBe4, of 700 cybersecurity leaders and 3,500 employees, finds incidents relating to the human element surged by 90 percent in the past year. Examples of ways these incidents can occur include social engineering attacks such as phishing or business email compromise (BEC), risky or malicious behavior and human error.