
O2 customer information available for sale on the dark web
O2 customer data has been found available for sale on the dark web, most likely as a result of a hack that occurred several years ago.
The gaming website XSplit was hacked three years ago and those responsible for the hack were able to obtain usernames and passwords from the site. Through the process of credential stuffing, in which account credentials acquired through a hack are tested on multiple websites, the hackers were able to gain access and log into O2 accounts.

The easy way to become a cyber criminal
You might think that becoming a cyber criminal required some hard work and dedication to your task, maybe even some form of apprenticeship where you learn the craft at the side of a more experienced hacker.
But new research has identified a one-stop, outsourced online shop, providing hosting, design and payment solutions for cyber criminals looking for a low-cost of entry method to sell their ill-gotten assets.

DDoS attacks increase by over 80 percent
In the second quarter of this year DDoS attacks increased by 83 percent to more than 182,900, according to the latest threat report from security solutions company Nexusguard.
The report shows that Russia has become the number one victim country. Starlink -- a Russian ISP supporting small, medium and large enterprises -- received more than 40 percent of the DDoS attacks measured over a two-day period. This targeted DNS attack also pushed the mean average DDoS duration to hours instead of minutes, as measured in the previous quarter.

Zero-day flaw leaves LastPass vulnerable to attack [UPDATE: it's fixed]
A Google Project Zero hacker has discovered a zero-day vulnerability in the password manager LastPass that could lead to accounts being completely compromised.
The security flaw can be triggered by visiting a malicious website, and it has been confirmed to be an issue by white hat security researcher Tavis Ormandy. He has filed a full report to LastPass with a view to getting the vulnerability patched.

Every piece of sensitive data could have 1,000 unnecessary copies
Data risk reduction specialist Identity Finder has rebranded itself as Spirion and has released the results of long-term sensitive data audits at three of its largest enterprise sites.
During the audits, the company discovered that if left unchecked, every legitimate piece of sensitive data will create up to 1,000 unnecessary copies.

Aegis Secure Key 3.0 [Review]
There are a number of secure flash drives on the market, but most of them rely on a software lock that requires you to enter a PIN on the computer after you've plugged in the drive. Apricorn takes a different approach with its Secure Key which has a keypad on the device itself, allowing you to lock and unlock it independently.
At 95.5 mm it's about half as long again as a normal flash drive and fits snugly into an aluminum slip case so you can't accidentally press buttons in your pocket. The keys are small but have a positive click action so you know they've been pressed. It comes formatted for NTFS ready for use on Windows systems and you can reformat it for Macs.

Future ransomware will be scary-dangerous
Here is a scary prospect. Ransomware that hides in a corporate network, analyzing it and multiplying itself until it is found on every machine in an organization. Only after it has contaminated every machine in a network will it activate, in a coordinated attack, bringing an entire company’s business to a screeching halt, until a large sum of money is paid to the attacker.
Such an idea is not yet reality, but it’s not far from it, either. Cisco’s Midyear Cybersecurity Report says it is only a matter before we hit this milestone, mostly because ransomware has become the most lucrative malware type in history.

SafeDNS uses machine learning to detect malicious internet resources
However careful you are online it's always possible to get caught out by a maliciously coded website or advert that leads to malware ending up on your machine.
Online safety service SafeDNS is launching a new system for detecting malicious internet resources, which it claims blocks close to 100 percent of them for better online protection.

Your wireless keyboard could be secretly leaking unencrypted data to hackers
Researchers at security firm Bastille warn that many wireless keyboards can be very easily intercepted so hackers can see exactly what is being typed. With a very simple dongle called Keysniffer, it is possible to snoop on usernames, passwords and anything else that is being typed from up to 250 feet away.
In all, Bastille found that eight manufacturers produce keyboards -- meaning there are millions in use -- which use unencrypted radio communication to transmit easily captured clear text. The problem affects non-Bluetooth devices from the likes of Anker, Hewlett-Packard, Kensington and Toshiba.

Europol's No More Ransom website helps ransomware victims unlock their files
To help curb the global rise of ransomware, the European police agency Europol has decided to launch a new initiative and website to put victims of an attack in touch with the police.
The initiative will be called "No More Ransom" and will be coordinated by Europol, but will also be receiving help from the Dutch national police, Intel Security and Kaspersky Lab.

88 percent of all ransomware is detected in the healthcare industry
According to the findings of a new report, companies in the healthcare industry have the most ransomware present, accounting for 88 percent of all detections in the second quarter of this year.
The report from managed security provider Solutionary shows other affected industries include education (six percent) and finance (four percent), with eight other industries combining for less than two percent of detections.

SentinelOne offers customers a $1 million ransomware guarantee
Ransomware is one of the biggest threats that companies face and it can have severe consequences if important files are corrupted or lost.
Endpoint security specialist SentinelOne is underlining its confidence in its product by launching a threat protection guarantee to provide customers with financial protection in the event of ransomware attacks on their networks.
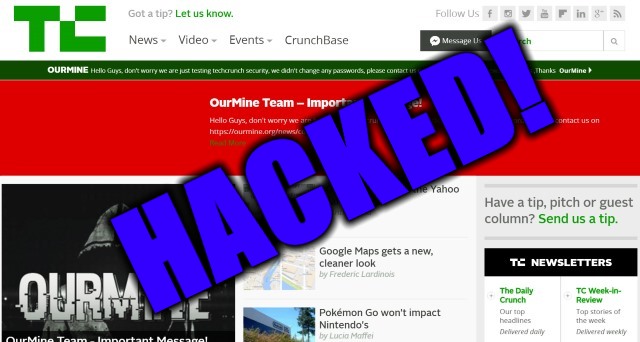
TechCrunch hacked by OurMine
The TechCrunch website was today hit by a hacker group going by the name of OurMine. The group describes itself as "an elite hacker group known for many hacks showing vulnerabilities in major systems".
The hack was -- on the face of it, at least -- not particularly malicious, and came across as almost polite. Rather than completely defacing the site, OurMine chose instead to simply post a news story to indicate that the CMS had been breached.
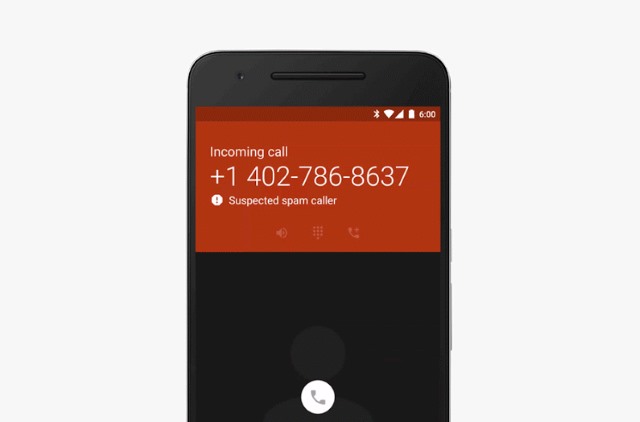
Spam call protection arrives in the Google Phone app for Android
We're used to the idea of filtering spam emails from our inbox these days, but there is also the problem of spam phone calls. These are not just a nuisance, but may also be the start of scams. Google is pushing out an update to its Phone app that helps to keep you protected.
It's a simple idea. Whenever a suspicious call comes through, a warning is displayed on screen to let you know that you might want to either ignore the call, or take care if you answer.

Hackers steal 1.6 million Clash of Kings forum accounts
The official forum for the popular mobile game Clash of Kings is the latest to fall victim to a cyberattack after a hacker broke through its defenses and managed to obtain the user data of around 1.6 million accounts.
The hack occurred on July 14 and the security breach was made known to the website LeakedSource.com by a hacker who wished to remain anonymous. The database of user account details taken from the forum contained the usernames, email addresses, IP addresses, device identifiers in addition to Facebook data and access tokens from those who signed in using their social accounts.