
Open source security plan aims to deliver on development, patching and more
White House officials, The Linux Foundation, OpenSSF and 37 private sector tech companies have announced a 10-point open source and software supply chain mobilization plan and $150 million of funding over two years.
At a summit meeting yesterday several participating organizations came together to collectively pledge an initial tranche of funding towards implementation of the plan. Those companies are Amazon, Ericsson, Google, Intel, Microsoft, and VMWare, pledging over $30M.

Emotet rockets to the top of the malware charts in Q1
The latest Threat Insights Report from HP Wolf Security shows a 27-fold increase in detections resulting from Emotet malicious spam campaigns in the first quarter of 2022.
Based on findings from millions of endpoints running HP Wolf Security, this makes Emotet the most seen malware family in the period accounting for nine percent of all malware captured.

The challenge of guarding against supply chain attacks [Q&A]
In recent years we've seen a trend towards attacks targeting the software supply chain rather than being directly against businesses.
Attacks can include poisoning the software components, stealing secrets to compromise an account, or modifying code repositories to allow for exploits.
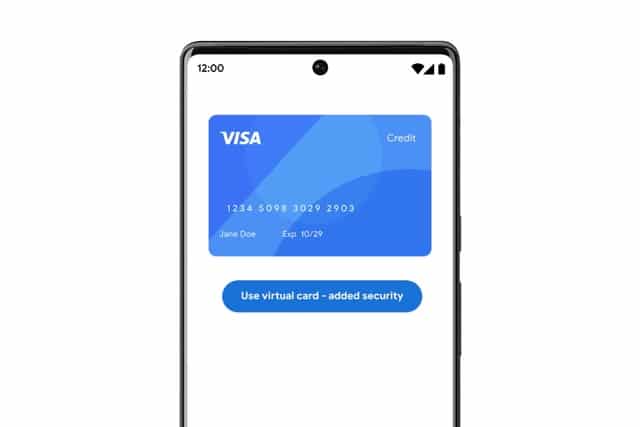
Google is bringing secure virtual credit cards to Chrome
Making payments online is fraught with potential dangers, and there is risk involved with making purchases with your credit card. To help offer a level of protection, many companies -- including the likes of Revolut -- enable their customers to create virtual, disposable credit cards.
Inspired by this, Google is building the same functionality into Chrome. The company announced the upcoming payment security feature at Google I/O, saying that there will be support for autofilling details to help speed up transactions.

Five years on from WannaCry -- what have we learned?
Today marks the fifth anniversary of the notorious WannaCry ransomware attack which hit a number of large organizations around the world and was many people's first encounter with ransomware.
Five years on then, what have we learned from the attack and what long-term effect has it had on the industry?

LinkedIn targeted in 52 percent of global phishing attacks
New analysis by AtlasVPN of primary data from Check Point shows business social network LinkedIn was related to over 52 percent of all phishing scams globally in the first quarter of 2022.
This is the first time that a social media network has been seen in campaigns much more often than any tech giant brand name like Apple, Google and Microsoft.

New start-up aims to boost personal cybersecurity for business execs
Enterprises are able to put considerable resources into securing their networks, which has led hackers to target executives via their personal accounts on social media and elsewhere outside the organization.
A survey by Influential Executive shows that in 2020, 94 percent of Fortune 500 CEOs were on LinkedIn and 62 percent on Facebook, YouTube, or Twitter, up from 39 percent five years before.

NewProfilePic -- From Russia with security risks [Updated]
The NewProfilePic app has been taking Facebook by storm in recent days, allowing users to upload a photograph and have it turned into a piece of digital artwork.
However, it's sparked concern in the cybersecurity community because it collects data and sends it to Russia. Linerock Investments, the company behind the app, is based in Moscow alongside Russia's defense ministry.

Old botnets make a comeback
Several older botnets have seen a resurgence in activity in the first quarter of 2022, including Mirai, STRRAT and Emotet, according to the latest threat report from Nuspire.
Mirai, known for co-opting IoT devices to launch DDoS attacks and first seen in 2016, showed a spike in activity in February of this year. This corresponded with the discovery of Spring4Shell, a zero-day attack on popular Java web application framework, Spring Core. The attack allows for unauthenticated remote code execution, and data show Mirai exploited this vulnerability to its botnet.

Staff at Fortune 1000 enterprises put their employers at risk
A new report has identified over 687 million exposed credentials and PII tied to Fortune 1000 employees, a 26 percent increase over last year's analysis.
The study from SpyCloud, based on its database of over 200 billion recaptured assets, also shows a 64 percent password reuse rate, widespread use of easy-to-guess passwords, and a spike in malware-infected devices.

Majority of Americans fear some form of cyberwarfare
The war in Ukraine has highlighted the role that the cyber world has to play in modern conflict and a new survey from NordVPN finds that 93 percent of Americans believe that another country could launch cyberwarfare against the US.
What's more, of over 1,000 consumers surveyed only 19 percent feel 100 percent confident in the government's ability to protect them, despite the fact that 70 percent rank the US as the most secure country for cyber war attacks.

The CSO's new seat at the executive table and how to use it [Q&A]
With the changes to working patterns brought about by the pandemic and increasing levels of cyberattacks, the role of the Chief Security Officer (CSO) in businesses has become more challenging.
These things have also led to a boost in the status of CSOs within their organizations. We spoke to Chaim Mazal, CISO and SVP of engineering for Apple device management platform Kandji to find out more about how things have changed and how CSOs can make the most of their new influence to drive security strategy.

Countering the risk of ransomware with operational continuity
In recent years, organizations all over the world have been hit by increasingly sophisticated ransomware attacks. For some, the impact is so severe that normal business operations experience major disruption with a knock-on effect on customers and revenue. For others, the impact can last weeks or even months as they seek to restore IT services and access to vital data.
Since the start of last year, for example, organizations across a huge range of sectors -- from oil and gas to food -- have seen their services impacted by ransomware. KP Snacks suffered an incident that brought its supply chain to a halt, with the company unable to process orders and dispatch products. And most recently of all, The Works, a retailer with over 500 stores across the UK, was forced to close some outlets after an employee reportedly fell victim to a phishing email that introduced ransomware to their infrastructure.

Microsoft 365 targeted as businesses struggle to block email threats
A new study commissioned by email security company Cyren from Osterman Research seeks to understand how businesses using Microsoft 365 for email are being impacted by email-borne security threats, such as phishing, business email compromise (BEC), and ransomware attacks.
It shows security team managers are most concerned that current email security solutions do not block serious inbound threats -- particularly ransomware. Fewer than half of organizations surveyed rank their currently deployed email security solutions as effective.

Organizations not equipped to handle increasing third-party risks
A new study into third-party risk management shows that 45 percent of organizations experienced a third-party security incident in the last year.
But the report from Prevalent also also reveals that eight percent of companies don't have a third-party incident response program in place, while 23 percent take a passive approach to third-party incident response.