
Why identity security could be the Achilles heel of your business [Q&A]
Most successful cyberattacks rely on compromised identity or social engineering. Yet this can be a major blindspot for enterprises with basic awareness of the problem lacking and a growing number of personal devices used for work.
We spoke to Jim Taylor, chief product officer of identity platform RSA, -- which recently published a report on the issue -- to learn more about the problem and how it can be addressed.

Breaking the cybersecurity automation logjam won’t break the bank
Right now, to boost efficiency and achieve economies of scale, businesses want to automate as much as possible. In back office processes, approaches like Robotic Process Automation (RPA), for example, are now increasingly standard and are expected to be a $20bn-plus market by 2030. In parallel, enterprises are looking to ChatGPT and Generative AI to help them speed up everything from creating marketing brochures to drug discovery.
However, where automation is trailing behind is in how organizations go about optimizing cybersecurity. Given that attacks tend to occur at scale, or involve complexity beyond even the smartest average security professional to cope with, this core area of vulnerability should be precisely where the CISO and the SOC (security operations center) seek assistance from automation.
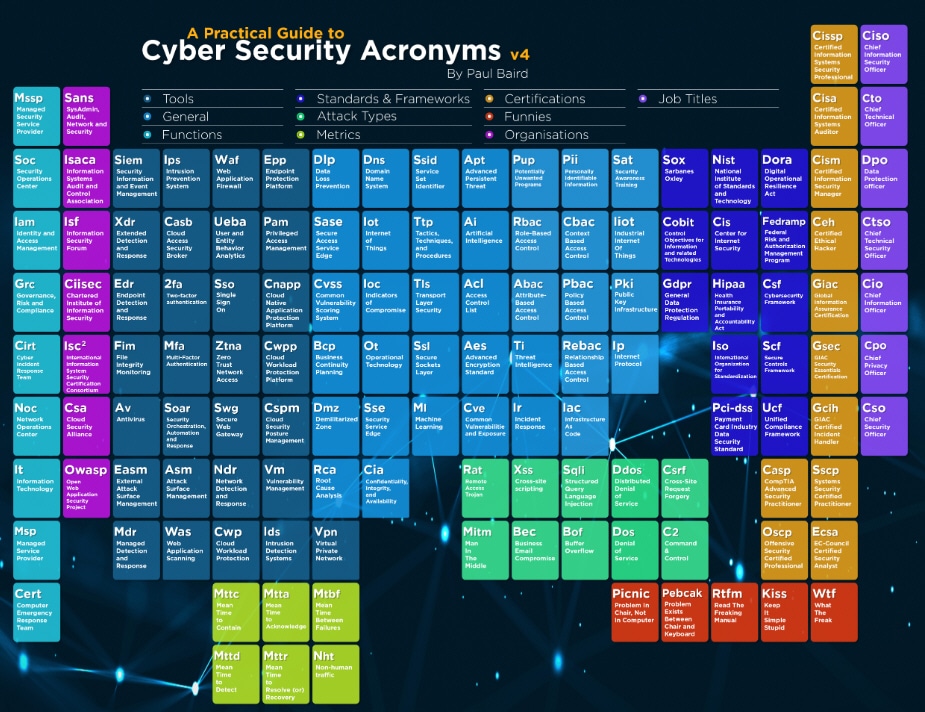
Making cybersecurity elementary [Q&A]
There are so many terms and acronyms used in the cybersecurity sector that it can be a little overwhelming at times, even for people who work in the industry.
Paul Baird, director of cyber security operations and engineering at Advanced Software and fellow at the Chartered Institute of Information Security (CIISec) has produced a round up of all the terms that you might ever need to know in the security space in a format based on the periodic table of elements.

Demand for cyber insurance increases as attacks get more sophisticated
A new report shows that as the severity and sophistication of cyberattacks has increased along with the financial consequences, many companies have been prompted to invest in or review their cybersecurity insurance.
The study of over 600 IT security professionals, conducted by the Ponemon Institute for Recast Software, shows 41 percent say their organization has experienced an increase in the number of cybersecurity incidents in 2023, 61 percent say the total cost of these attacks had averaged $21 million, and 75 percent say their cybersecurity exposure would increase or at best stay the same in the coming year.

Interest in AI and security surges among developers
The latest Technology Trends Report from O'Reilly shows interest in generative AI among developers has surged.
The report looks at the most popular technology topics consumed by the 2.8 million users on O'Reilly’s online learning platform and finds that topic engagement in GPTs has grown 2,600 percent year-on-year.

2023 marked an 80 percent increase in ransomware activity
The latest annual report from the GuidePoint Research and Intelligence Team (GRIT) observed 63 distinct ransomware groups using encryption, data exfiltration, data extortion, and other novel tactics to compromise and publicly post 4,519 victims across all 30 of GRIT's tracked industries, and in 120 countries, across 2023.
Most impacts affected a limited subset of industries. 62 percent of all observed victims belong to one of the top ten most-impacted industries, with manufacturing and technology remaining the two most-impacted.

Majority of companies not prepared for insider threats
An overwhelming majority of global organizations admit they are ill-prepared to handle the steady increase in insider threat activity, according to new research conducted by Cybersecurity Insiders and announced today by Securonix.
While 76 percent of organizations have detected increased insider threat activity over the past five years, less than 30 percent believe they are equipped with the right tools to handle them.

Bugcrowd sees 30 percent increase in web vulnerability submissions
Crowdsourced security platform Bugcrowd’s latest Vulnerability Trends Report finds that the hacker community recorded a 30 percent increase in web vulnerability submissions on the platform compared to 2022.
In addition it has recorded an 18 percent increase in API submissions, a 21 percent increase in Android submissions, and a 17 percent increase in iOS submissions.

New unified SASE gateway boosts performance for enterprises
Secure Access Service Edge (SASE) technology has become increasingly popular as it combines the delivery of wide area networks and security controls in a single platform.
As enterprises look to support new digital requirements including accelerated cloud adoption, edge computing, increased use of collaboration tools, and a hybrid workforce SASE is likely to become still more popular. Versa Networks is launching a new line of Unified SASE gateways delivering 100+ Gbps throughput to meet the growing demand for increased convergence of networking and security.

Organizations face devastating financial consequences from cyberattacks
A new report from Barracuda Networks and the Ponemon Institute looks at 'cybernomics' -- the financial forces that are driving cyberattacks.
Based on a survey of over 1,900 IT security practitioners it finds the average annual cost to respond to compromises is a startling $5.34 million.

Verified randomness -- what is it and why does it matter? [Q&A]
Much of the online world relies on things being random. Gamers trust that their players re-spawn at completely random locations, similarly, gamblers trust that online slot machines are giving them random outcomes.
Ensuring things are properly random is also important for things like decentralized finance and blockchain transactions. But how can you be sure that something is properly random?

New resource helps enterprises prepare for post-quantum security
Cybersecurity company Thales is launching a first-of-its-kind Post Quantum Cryptography (PQC) Starter Kit in collaboration with Quantinuum, aimed at supporting enterprises in their transition to a post-quantum era and helping them understand the implications that quantum computing will have on the security of their infrastructure.
While 73 percent of organizations recognize quantum computing poses a threat to traditional cryptography, 61 percent have yet to define a strategy for a post-quantum world.

How your voice could be used by phone scammers
We've all become used to scam phone calls of various kinds, but it seems AI is allowing them to become more sophisticated.
According to NordVPN, scammers are now able to create realistic voice clones from samples collected online and use them to extort money and data from victims' friends, relatives, or colleagues.

Winter is coming and so are the hackers
A survey from Defcon 17 back in 2009 revealed that 81 percent of hackers are more likely to be active in winter.
It's easy to understand why this might be, with the holiday period bringing a spike in online trading as well as businesses closing down or operating on skeleton staffs.

81 percent of security pros say phishing is the top threat
A new study finds that that most organizations anticipate phishing (81 percent), malware and ransomware (76 percent), and accidental data loss (63 percent) will be the top security risks over the next six months, followed by social engineering (55 percent) and third-party risks (52 percent).
The report from Fortra looks at the challenges security professionals have faced over the past year, as well as what they plan to focus on next as they continue to embrace digital transformation, new hybrid infrastructures and a challenging security landscape.