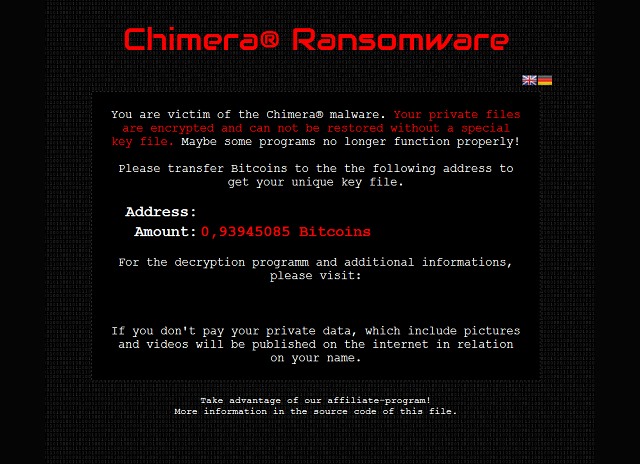
Chimera crypto-ransomware threatens to share your private files online
Crypto-ransomware is one of the latest trends in the world of malware. Encrypting and holding files to ransom provides a way to extort money from victims, but a new example takes things one step further.
Chimera not only locks users out of their files until a ransom is paid, but also threatens to release unencrypted copies of the files online if payment is not made. Security company Trend Micro says this is the first instance of this type of threat. Interestingly, Chimera also seems to be part of an affiliate program.

Microsoft's enterprise security software now offers PUA protection
Microsoft has started to offer potentially unwanted application (PUA) protection in its anti-malware products for enterprise firms.
The news means that businesses will finally have an easy way of removing adware, browser hijackers and any other piece of software that deploys programs without the user’s knowledge or consent.

The threats of November 2015, Linux ransomware leads the way according to new report
November is almost in the books and we're into the holiday season. Unfortunately that means some people would like your money to shop with. November was about ransomware, not just viruses, trojans and malware, or at least that's what a new report has found.
Dr Web states that Linux was at the top of the list in terms of what could go wrong. Linux.encoder.1 ranked as the top threat of the month. This is a derivative of Trojan.encoder.737 which was found in 2014 and has since been changed into this iteration.

BullGuard Internet Security 2016 offers good value for home users [Review]
Recent reports have highlighted that it’s security at the endpoint which often leaves businesses exposed. This applies not just to machines in the office but also to mobile and BYOD devices, so some sort of security solution is essential.
BullGuard has released its latest Internet Security suite this month which is fully Windows 10 compatible and includes a number of things that make it an attractive option for business users. New features like Dropbox compatible backup and storage ensure that business data is properly protected.

Critical Zen Cart vulnerability could spell Black Friday disaster for online shoppers
It's around this time of year, with Black Friday looming and Christmas just around the corner, that online sales boom. Today security firm High-Tech Bridge has issued a warning to retailers and shoppers about a critical vulnerability in the popular Zen Cart shopping management system.
High-Tech Bridge has provided Zen Cart with full details of the security flaw which could allow remote attackers to infiltrate web servers and gain access to customer data. Servers running Zen Cart are also at risk of malware, meaning that hundreds of thousands of ecommerce sites pose a potential danger.

Hilton Hotels answers allegations of card-stealing malware
We heard earlier this week that Hilton Hotels had been hit with malware designed to steal personal data and, even worse, credit card information. The breach affected point-of-sale systems. Sounds familiar? This same sort of beach happened to a number of major targets in 2015, mostly retail chains like Target and Home Depot.
Hilton has now responded to the issue and admits there was a problem. It's advising customers to keep a close eye on transactions on their accounts. Though customers are generally not held responsible for fraudulent charges it's a major hassle to go through.

Adware uses Android's accessibility features to install malware
There’s an adware out there which uses features for the visually impaired to install malicious apps on an Android-powered device. The worst part is that it doesn’t use a vulnerability in the system, but instead abuses a service’s legitimate features.
Researchers from mobile security provider Lookout have spotted the abusers and published a blog post about it.

Banking trojan Dyreza goes after Windows 10, Microsoft Edge users
The Dyreza banking trojan has (unfortunately) been updated, and now can target users sporting Windows 10 and its internet browser, Microsoft Edge.
The new version of the banking trojan was spotted and analyzed by EU-based security firm Heimdal Security, which claims that Dyreza will now also seek and find security products, terminating their underlying OS processes.
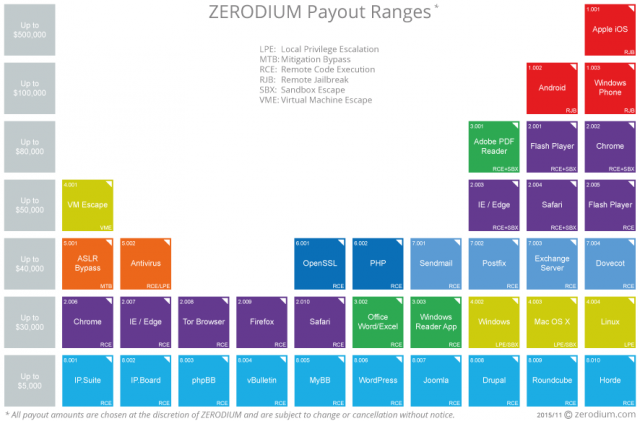
Zerodium reveals price list for zero-day exploits
Exploit acquisition platform Zerodium has just published a price chart for different classes of digital intrusion techniques and software targets that it buys from hackers and later resells in a subscription service to its clients.
This is important as it is the first time someone has publically put a price tag on hacking.

Government organizations are major target of Q3 cyber attacks
PandaLabs, the malware research arm of Panda Security has released its latest quarterly security report revealing a wave of cyberattacks where the security and information of various governments has been compromised.
The company has detected a growing interest between countries in compromising the security and information of different governments. With that in mind, one of the most important attacks during this period was against the Hacking Team, which controls a multitude of cyberespionage and cyberattack tools for various governments around the world.
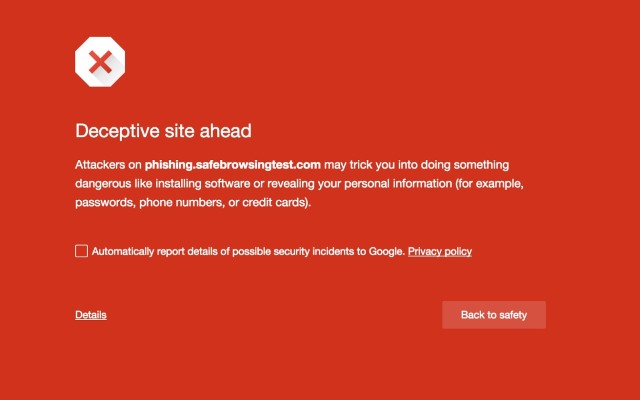
Google extends Chrome's Safe Browsing protection to fight social engineering
Online attacks take a number of forms, and phishing is one of the more recent problems. Chrome has long featured Safe Browsing to notify people when they visit potentially dangerous websites, and today Google announces that the feature is growing to include social engineering.
Google describes social engineering as being a much broader category than traditional phishing. Typical examples include sites that trick visitors into imparting passwords or credit card details, and those which purport to be an official website when they are in fact malicious. The Safe Browsing expansion offers protection against a range of social engineering attacks that Google provides examples of.

InstaAgent app steals usernames and passwords from Instagram users
An app that enables iPhone users to keep an eye on who has been looking at their Instagram account has been pulled from the App Store after it was found to be stealing usernames and passwords.
Apple took the decision to kill "Who Viewed Your Profile -- InstaAgent" when the app was found scraping login details and sending them back to the developer's server. This in itself is worrying for users, but it gets worse: the usernames and passwords were sent in unencrypted format.

Linux users targeted by new Linux.Encoder.1 encryption ransomware
Extortion is just the latest in a series of weapons being used to terrorize computer users and technology companies. One of the most recent victims was ProtonMail which found itself the subject of a DDoS attack and a ransom demand -- and despite paying up, the attacks continued. But individual users also have their feet held in the fire by ransomware.
It's something that mobile users have become familiar with. Android users have been hit by malware that encrypts the contents of their phones and renders it inaccessible until a ransom is paid. It's a problem that has also affected Windows users, and the latest target is Linux. Web servers powered by Linux are being targeted by the Linux.Encoder.1 crypto-ransomware.

ProtonMail sets a dangerous precedent and opens itself up to further attacks by paying ransom
In the world of malware, one of the most recent trends is ransomware -- malicious software that either blocks access to a computer until a fee is paid, or files are encrypted until a ransom is put forward. As with ransomware and kidnapping, a ransom is often demanded by hackers and instigators of DDoS attacks.
This is precisely what happened to 'secure' email provider ProtonMail the other day when it found its datacenter inundated with traffic. At the time, the company asked for donations to cover the costs of the "quite expensive solutions" needed to fight back against "the sophistication of this attack". But rather than fighting back, ProtonMail decided to pay the ransom instead. This could prove to be a terrible mistake.

Shuanet, ShiftyBug and Shedun malware could auto-root your Android
Rooting a phone is something that many people decide to do to allow them to do things and use apps that would not otherwise be possible. If you make the choice, you are in control. But security researchers at Lookout have discovered a new form of malware disguised as apps from the likes of Facebook and Twitter.
While some of the apps are partially functional, the malware has a nasty payload: it could be quietly rooting your phone in the background. Lookout has identified three families of malware -- Shuanet, ShiftyBug, and Shedun -- that can be found in more than 20,000 apps in Google Play. Once installed, the malware is almost impossible to remove.