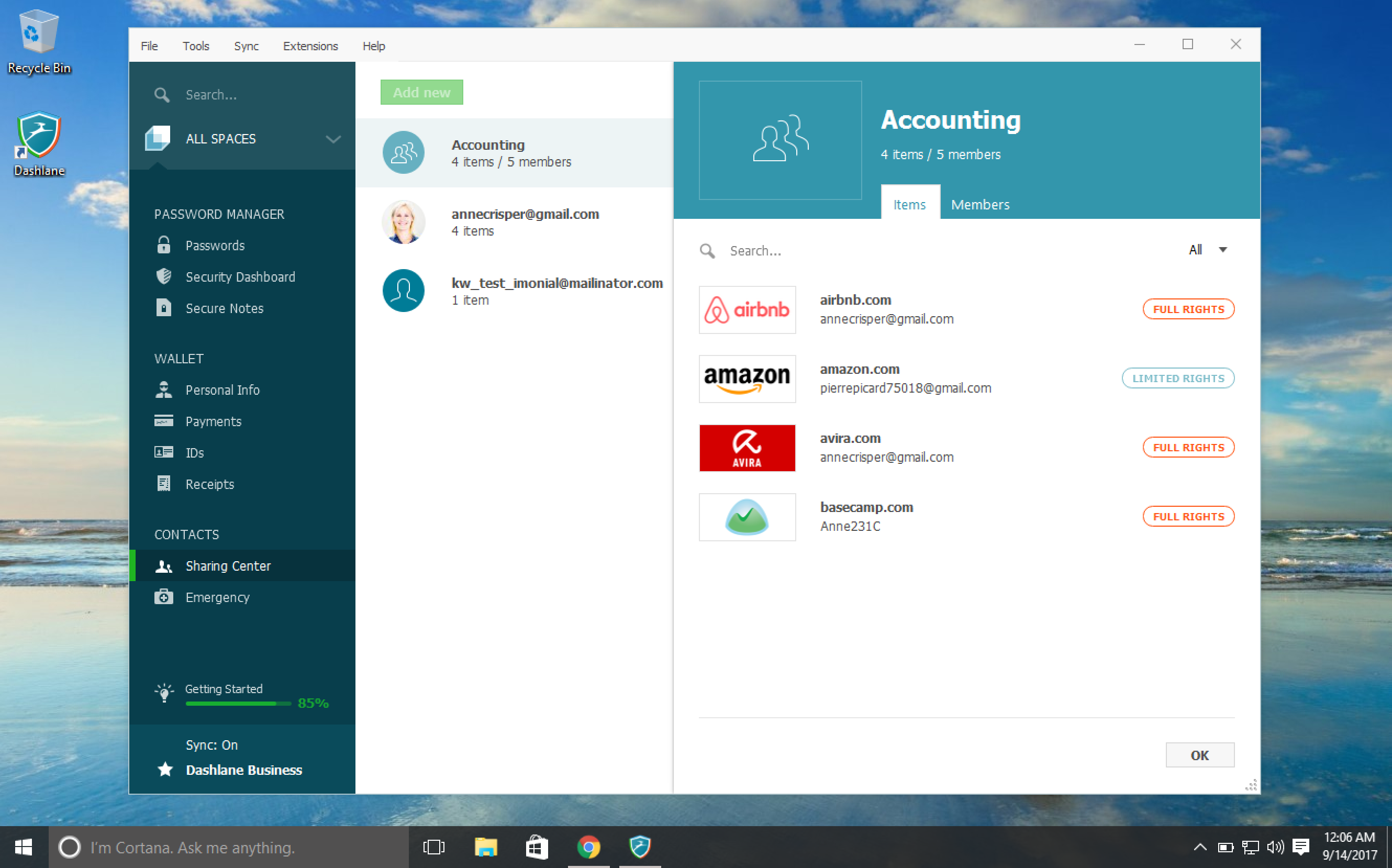
New enterprise password management tool eases administrator workload
Effective password management is essential in helping to control data breaches, but employees often use the same passwords for both work and personal use, leaving corporate data potentially exposed.
Password management company Dashlane is launching its new Dashlane Business 2.0 enterprise password solution.

Office workers fall victim to phishing attacks despite training
Despite training and other efforts to combat the problem, phishing is still proving a remarkably effective tactic for cyber criminals according to a new report.
The study by cloud business applications company Intermedia shows that while 70 percent of office workers say that their organization regularly communicates with employees about cyber threats as a means of prevention, there are significant gaps between confidence and effectiveness.

Businesses having difficulties filling specialized IT positions
With most organizations now increasingly using a wide variety of software and IT tools to maximize their potential, keeping track of all your various services has never been more important.
This importance has been highlighted by new research from CA Technologies showing that those organizations that are able to adopt modern software development practices are seeing overwhelmingly more benefits than those who don't.

BT will open cybersecurity center in Australia
BT is set to launch its first cybersecurity R&D center outside of the UK with the opening of a new hub in Sydney.
The office will focus on developing security services than can be deployed both locally and across the world, with BT saying this will include areas such as cyber security, machine learning, data science analytics and visualization, big data engineering, cloud computing, and data networking, as well as "the full life cycle of software engineering."
Twitter proves better than the Dark Web for assessing vulnerability risk
The latest report from risk management and cyber security company Nopsec looks at the use of social media in risk analysis.
Twitter in particular seems to be becoming the go-to resource for security researchers and attackers looking to disseminate proof-of-concept exploits.

Microsoft adds Confidential Compute to Azure cloud platform
Microsoft has revealed a major new addition to its Azure cloud platform, aimed at keeping user data safe.
The feature, called Confidential Compute, will make sure the data is being encrypted even when it’s being computed on in-memory. So far, it’s been encrypted while stored or while in transit on a network.

Avast opens up about CCleaner hack and outlines how it will protect users
When news broke yesterday that CCleaner had been hacked and a dangerously modified version had been available to download for a number of weeks, there were understandable concerns from the program's large userbase. And the concern is well-placed -- some 2.27 million machines are thought to have installed the infected software.
Avast now has something of a PR nightmare on its hands as it tries to rebuild the trust of its users. To this end, company CEO Vince Steckler and CTO Ondřej Vlček have written an article clarifying what happened with CCleaner, and give some details about how they plan to protect their customers -- as well as "correct[ing] some misleading information that is currently circulating."

Mobile network flaws could open Bitcoin wallets to hackers
An architecture flaw in mobile networks could allow hackers to intercept SMS one-time passwords and access Bitcoin wallets.
The vulnerability uncovered by enterprise security specialist Positive Technologies means that with just a person's first name, last name, and phone number, researchers were able learn the email address linked to the wallet, obtain control over it, and gain access to the wallet itself including withdrawing funds.

Majority of enterprise cloud services still not ready for GDPR
With the EU's General Data Protection Regulation set to come into force in May next year, companies are rushing to ensure that their systems will comply with its rules.
Yet a new report from cloud security company Netskope finds that almost three-quarters of cloud services still lack key capabilities needed to ensure compliance with the GDPR regulations.

First half of 2017 sees more mobile vulnerabilities than for the whole of 2016
A new report into mobile threats reveals that in the first half of 2017, there were more common vulnerabilities and exposures (CVEs) registered for Android and iOS than in all of 2016.
The study by mobile threat defense company Zimperium, based on data from its z3a app analysis tool, also shows that many devices aren't running the latest operating systems, leaving them vulnerable.

Security warning: Hackers compromised CCleaner and installed a backdoor
Users of cleanup, privacy and optimization tool CCleaner are being warned to update their software after it emerged the tool was compromised by hackers. Security researchers at Cisco Talos say that there are a "vast number of machines at risk."
CCleaner is produced by Piriform, now a subsidiary of security firm Avast, making the compromise not only serious, but also embarrassing. With 2 billion downloads -- a number that's rising at a rate of 5 million per week -- the software was targeted by hackers who added a backdoor that could be used to download malware, ransomware and keyloggers. The problem is being compared to the NotPetya ransomware threat.

Public cloud security is a concern for most IT pros in UK
An overwhelming majority of the UK’s IT professionals (90 percent) have their worries when it comes to securing the public cloud, according to a new study.
Research by Bitdefender found that 90 per cent of British professionals had concerns around the security of public cloud. A fifth (20 per cent) also said that their business doesn’t have security measures set up for sensitive data outside the company infrastructure.

VMware announces AppDefense security solution
VMware has revealed how it wants to help businesses across the world keep their data secure.
At the company’s VMworld Europe 2017 event in Barcelona earlier this week, CEO Pat Gelsinger outlined the company’s new security strategy, including how its new AppDefense tool can help enterprises of all sizes stay safe online.

Peering into the future of enterprise security
How many desktops do you have out there that are still not on Microsoft Windows 10? Given the security vulnerabilities associated with earlier versions of Windows, the simple answer for most executives is too many. With new attacks like WannaCry and NotPetya appearing far too frequently, your IT teams are probably hard at work on a migration plan to move your older desktop systems to the more secure Windows 10 OS. In my company’s recent survey of nearly 500 IT professionals, nearly 80 percent of the respondents indicated that the enhanced security features of Windows 10 were the primary reason they were eager to migrate.
Still, migration takes time, and though it is comforting to know that more and more systems may be migrated over to Windows 10 each day, the lingering awareness of how many systems have yet to be migrated is reason for concern. It’s hard to be fully comfortable when you know how much of your organization is missing out on the security improvements of the new OS.

OurMine leaks 3TB of Vevo data after hacking video streaming service
Infamous hacker group OurMine has struck video streaming service Vevo. The group breached Vevo late on Thursday, gaining access to, and leaking, more than 3 terabytes of internal videos and documents.
OurMine -- more recently involved in HBO hacks and Game of Thrones leaks -- managed to get hold of office documents, videos and promotional materials. While many of the files and documents are fairly innocuous, at least some of them would be considered "sensitive" in nature.