
9 low-cost, high-tech ways to secure your home
Technology is ever the equalizer, and this is increasingly true in the realm of home security. For most people, home security means a few good deadbolts and possibly some bars on the window. Whole-home, monitored, wired security systems that cost upwards of $50 a month (not to mention long-term contracts and multiple up-charges for installation and additional features) are an expensive option if all you want to know is if someone is in your backyard or trying to open your front door.
Today, thanks to wireless technology, there are multiple lower-priced options for home monitoring systems, including complete DIY systems that you can install and monitor yourself. However, these still start at around $200. What if you just want some basic, high-tech security that won’t break the bank? Here is a round-up of nine low-cost, high-tech ways you can protect your home, based on your specific security needs, all for under $100.

Karmen ransomware gives cyber criminals a user-friendly attack tool
Researchers at threat intelligence specialist Recorded Future have uncovered a new strain of ransomware called Karmen that’s designed for use by people with limited technical expertise.
The ransomware-as-service has been developed by Russian and German hackers and is notable for its user-friendly approach. It comes equipped with a dashboard that allows the tracking of computers infected with the virus, including the status of any ransom that’s been paid.

Almost half of UK business hit by cyber crime
UK-based businesses of all sizes are being urged to protect themselves against cyber crime after new government statistics showed nearly half of all UK businesses suffered a cyber breach or attack in the past year.
The Cyber Security Breaches Survey 2017 reveals nearly seven out of 10 large businesses identified a breach or attack, with the average cost to large businesses of all breaches over the period being £20,000 and in some cases reaching millions.
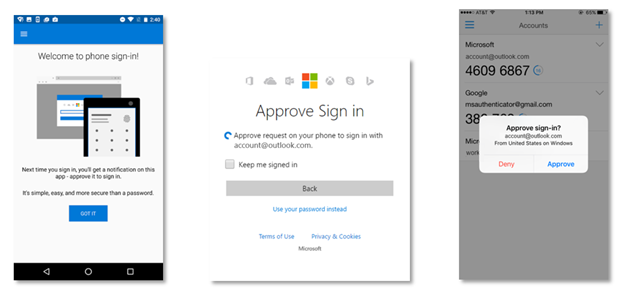
Microsoft Authenticator app gets phone sign in
Microsoft is making it easier than ever to sign into a Microsoft account, adding a new authentication option in the Microsoft Authenticator app that lets you approve the sign in attempt using just your Android smartphone or iPhone.
Here's how it works. When you enter your Microsoft account handle you will get a prompt from Microsoft Authenticator to approve or deny the attempt. To take advantage of this option, you need to add your Microsoft account to the app or, if you already did so, turn on the "Enable phone sign-in" option.

Lloyds Bank offers Windows Hello facial and fingerprint recognition
Lloyds Bank customers will soon be able to log into their accounts through fingerprint scanners and facial recognition technology, rather than typing in passwords. According to the bank, it has teamed up with Microsoft to bring the Windows 10 authentication technology to its customers.
The biometric authentication technology, which Microsoft named Windows Hello, uses a combination of infrared technology and advanced software to identify the user in various lighting conditions. It was also emphasized that fraudsters can’t bypass the security measure by using a photograph.

Over 70 percent of companies using AWS have serious security misconfigurations
A high percentage of companies using AWS cloud services have at least one critical security misconfiguration according to a new survey.
Cloud security company Threat Stack has analyzed more than 200 companies using AWS and found a number of well-documented security misconfigurations.

A fifth of UK firms hit by cyber-attacks, putting private data at risk
UK companies are ill-equipped to deal with cyber-attacks, a report by the British Chambers of Commerce (BCC) says. Nearly one in five smaller companies (18 percent) have fallen prey to cybercrime, and the figures are even worse for larger firms.
When looking at companies with more than 100 employees, the number that have been hit by cyber-attacks jumps to a staggering 42 percent. More than three quarters of the firms surveyed by the BCC did not have anti-hacking security measures in place, and most relied on third-party firms to clean up after an attack rather than having in-house solutions.

8 things businesses can do to lower cyber attack risks
Hardly a day goes by without some media coverage that is focused on cyber. Whether is it sensationalist headlines announcing the most recent cyber-attack that has left some unfortunate company red faced and bereft, the outcome of yet another survey generally conducted by an entity selling cyber related goods or services, or the announcement of new regulation and legislation. A front page headline of CITY AM screams CYBER CRIME WIPES £42BN OFF SHARES -- surely there cannot be a board director left who can deny awareness that cyber-crime poses a threat to his or her business.
Having engaged in the cyber debate for more than a decade, it seems we can at last all agree that the foundation stone is now well in place with widespread, if not universal, acceptance that cyber-crime and cyber risk are real and now an ever present challenge to businesses.

Secure your Twitter account with two-factor authentication
There are not many well-known online services that don't offer two-factor authentication (2FA) nowadays, but Twitter is very late to the party. Well, that might not be strictly true. Twitter recently added support for third-party authenticator apps, but failed to make any sort of song and dance about it.
The change means that it's now possible to make use of the likes of Google Authenticator and Authy with Twitter -- but you'd be forgiven for not having found the option by accident already.

'Here be dragons': Look past FUD to see the real security threats
It shouldn’t come as a surprise that cybercrime is big business, and is growing at an exponential rate. In 2015, UK insurer Lloyd’s of London estimated the cybercrime market at $400 Billion. Today, just two years later, the World Economic Forum estimates that same market to currently be $3 trillion. And the prediction from Cybersecurity Ventures is that it will cost the world in excess of $6 trillion annually by 2021.
The "darknet" -- the part of the Internet that most people have never seen and which lies beyond normal web browsers -- is protected by layers of anonymity, and has become a haven for criminal commerce. Its inaccessibility lends it a certain mystique, but that aura of mystery breeds misunderstanding. At the edge of the unknown, understanding tends to be a scarce commodity and is often replaced with fear, uncertainty, and doubt -- a trio so intertwined they’re better known simply as "FUD."

Twistlock delivers enhanced security and compliance for container environments
In recent years containerization has seen increased popularity thanks to its ability to deliver an agile, flexible environment in which software can be reliably moved from development to testing to live, or from in-house to the cloud.
But the use of containers also throws up new challenges, particularly when it comes to keeping data secure. Container security specialist Twistlock is using this week's DockerCon to launch an updated product with new features, improved performance and a revised user interface.

Microsoft already fixed the 'Shadow Brokers' exploits on supported versions of Windows
Say what you want about Microsoft, but the company stays on top of security. Yeah, it may issue more patches and fixes for Windows compared to some other operating systems, but that doesn't necessarily mean the OS is less secure -- it could mean that the company is simply more proactive and transparent than others. Quite frankly, I'd rather get many patches than be lulled into a false sense of security.
When hacking group "Shadow Brokers" started leaking NSA-discovered exploits, many people were understandably worried. While the leaks would enable operating system makers to issue patches -- thereby making the OS more secure -- it also meant that before the fixes were issued, many computers would be at an increased risk. Luckily, when it comes to the recently leaked Windows exploits, Microsoft was already prepared -- currently supported versions of the operating system are not impacted.

UK businesses face nearly 500 attacks a day
OK, so, Beaming says UK businesses suffered, on average, 43,000 cyber-attacks in the first quarter of 2017 -- each. If this number sounds way too big, then it would be even more interesting to hear that this is actually seven per= cent lower than what was going on in the same period last year.
Breaking the numbers down, Beaming says each business gets attacked 474 times per day. Almost all of these attacks, 92 percent of them, are targeting Internet of things devices, such as networked security cameras or building control systems, as these IoT devices can be controlled remotely, over the internet.

[Updated] Microsoft transparency report reveals first National Security Letter and shows doubling of FISA orders
Microsoft has published its latest transparency report and, for the first time, disclosed the contents of a National Security Letter it received. In addition to the debut appearance of such a letter in the report, Microsoft also reveals that in the reported period in 2016 the number of FISA orders more than doubled compared to the previous period.
As with previous reports, Microsoft is not permitted -- for reasons best known to the US government -- to reveal precise numbers when talking about the number of official requests for data it has received. As such, we know that in the most recent reporting period, it received between 1,000 and 1,499 FISA orders, up from 0-499.

US extreme vetting rules for tourists could put business data at risk
New legislation being considered by the Trump administration suggests that UK citizens traveling to the United States would have to hand over personal information such as passwords to their social media accounts and access to the contacts in their mobile phone or risk being denied entry to the country.
This comes just weeks after another travel-based regulation that banned certain electronic devices from some countries in North Africa and the Middle East bound for either the US or UK. At the same time, the upcoming GDPR is putting huge pressure on organizations to secure their data. How do these new travel regulations impact organizations trying to secure their sensitive data?