
Could the Internet of Things spark a data security epidemic?
Internet of Things this, Internet of Things that -- it’s all anyone can talk about these days. And rightfully so, when you consider the development and adoption of IoT products are driven by multiple factors, including an increase in broadband penetration worldwide, the development of wireless communication technologies, advances in 'smart' device capabilities and an increased demand for personalized, omnichannel customer experiences.
But transitioning to an IoT-dominated world is a delicate balancing act. On the one hand, you have businesses benefiting in many ways. For instance, connected devices allow them to better understand their customers’ needs and preferences by analyzing their behavioral patterns. For consumers, on the other hand, it’s all about personalization, personalization, personalization -- getting from point A to point B faster than ever before -- in a more relevant and personal way. Furthermore, most conversations around data protection solely focus on elaborate 'hacks', when in reality, the most immediate and grave security threats aren’t always sophisticated or complicated. It’s time that we flip the IoT conversation on its head to focus on the increasingly common data vulnerabilities and less complicated security threats -- of which, consumers are lacking awareness.

BlackBerry's privacy stance is yet another reason to avoid the company
We are living in a post NSA-world (and I am a post-NSA girl...) and privacy is in the public consciousness more than ever before. After the government surveillance revelations that came courtesy of Eddy Snowden, most tech companies have been trying to stress to customers and clients just how willing they are to stand up for privacy.
But not BlackBerry. Company CEO John Chen has used a blog post to lash out at his contemporaries for supporting strong encryption. He makes a thinly-veiled reference to Apple, accusing that an unwillingness to comply with law enforcement requests put us all in a "dark place". Chen says that "our privacy commitment does not extend to criminals", seemingly failing to recognize that privacy is very much an all-or-nothing concept.

Security researcher finds 685TB of unprotected MongoDB data
There is roughly 685TB of private data from MongoDB instances sitting online, without any protection, researchers have uncovered.
Following the recent discovery by security researcher Chris Vickery, who saw the data of more than 13 million MacKeeper users exposed, another researcher ventured even deeper and found even more unprotected data.
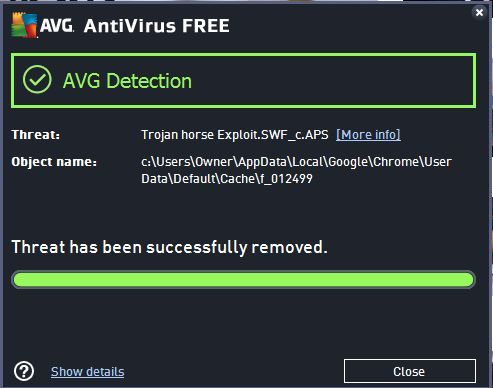
AVG update to fix false Trojan warning
Anti-virus giant AVG sparked fear among internet users on Thursday after its popular security scanner falsely identified websites as infected with a malicious Trojan horse application.
Visitors to popular websites, such as Mirror.co.uk and Twitch.tv, were greeted with a warning that AVG had detected a threat called "Trojan horse Exploit.SWF_c.AP", with the recommendation to remove it. Once removed, the warning pop-up window would reappear multiple times.

FreeSmartSoft products still hiding an uninstallable 'back door'
It’s three weeks since we exposed freeware developer FreeSmartSoft for including an uninstallable adware-serving back door in some of its products.
The company had released some updated versions since then, so we checked out a copy of the popular FSS Google Book Downloader to see if any lessons had been learned.

Most Android devices run an outdated OS version
More than 80 percent of Android devices are running an outdated version of the operating system. Those are the results of an inquiry among users of G DATA security solutions for Android.
G DATA believes the lag in the adoption of new versions lies in the long delays before manufacturers roll out updates to their devices, as well as the fact that some devices simply don’t support the latest version of Android.

P2P file sharing and its impact on business
When you think of peer-to-peer file sharing you probably bring to mind services like Kazaa and Limewire that were among the early sites allowing users to share media, or of more recent operations like Pirate Bay.
But while it's easy to think of P2P in terms of individuals downloading music or movies, a new report from security rating company BitSight reveals that it’s a problem for businesses too.

The bible is dangerous for you and your phone
For the religiously-inclined the appeal of installing an electronic bible on a phone is (somewhat) understandable. But as well as providing a biblical fix when out and about, apps of a religious bent could also harbor a worrying payload.
The Threat Insight team from Proofpoint looked at thousands of iOS and Android apps, and found that a disturbing percentage of seemingly innocent apps pose a threat to users. Apps were found to include secret tracking components, as well as data-stealing elements and the ability to make unauthorized calls. The figures make for frightening reading.

13 million MacKeeper accounts leak online
The anti-virus software for Apple’s OS X, MacKeeper, kept the user data of more than 13 million of its customers online without much protection, and someone eventually stumbled upon it.
Yes, stumbled is the perfect word in this instance, as the data was accessed through an IP address, no username or password required.

Hillstone adds extra security layer for AWS customers
When moving applications to the cloud it's easy to fall into the trap of believing that security can safely be left to the provider.
For Amazon Web Services customers there's now an extra layer of security on offer from Hillstone Networks. Hillstone CloudEdge is deployed as an Amazon Virtual Private Cloud (Amazon VPC) gateway to provide an additional layer of security protection.

New breach detection solution alerts enterprises to insider threats
For enterprises and government departments the biggest threats can often come from within the organization rather than outside it.
Detecting these insider threats can be difficult which is why security company Eastwind Breach Detection is launching a new platform that uses rich data, behavioral analytics, and threat intelligence to pinpoint anomalous behaviors even before they're classified as breaches.

BUFFERZONE launches advanced threat protection for Windows 10
Employee use of email and web browsers is still one of the most common ways that businesses suffer from cyber attacks, which underlines the need for effective protection.
Endpoint security specialist BUFFERZONE is announcing its product's support for Windows 10 to protect organizations upgrading to the latest OS from advanced threats, zero-day attacks, drive-by downloads and phishing scams.
No, the UK government doesn't have Twitter accounts supporting ISIS
ISIS has been in the news for some time now, and events like the recent terror attacks in Paris keep pushing the group into the public consciousness. Governments may be waging war on ISIS on the ground, but on the web it is the likes of Anonymous and vigilante hackers who have taken it upon themselves to curtail terrorist propaganda.
In the latest twist in the tail, hacker group VandaSec traced the IP addresses relating to some ISIS Twitter accounts to the UK government -- the Department of Work and Pensions specifically. Given that the accounts have been used not only to spread ISIS propaganda, but also to recruit members, does the UK government have a dirty little secret? As you might expect, it's not quite that simple.

The biggest data breaches of 2015
10Fold recently evaluated the seven largest breaches this year and found that hackers had absconded with more than 193.4 million personal records. To get to this figure, the agency reviewed 720 data breaches that occurred throughout the year. To narrow the list to a more manageable size, the team made five million the barrier to entry.
10Fold selected these data breaches based on independent research and review of third-party resources such as ID Theft Resource Center and Information is Beautiful.

New endpoint protection offers government users security for the public cloud
Use of the public cloud is on the increase but in some sectors such as government agencies is being held back by security concerns.
Data protection specialist Druva is announcing that it's launching a new endpoint solution that is Federal Information Processing Standards (FIPS) compliant.