
Anonymous hacks the European Space Agency
The European Space Agency (ESA) has been hacked by Anonymous, and the names and login credentials of some of its employees have been posted online, the media reported on Monday.
The data released into the wild includes full names, email contact details, clear text passwords, office addresses, phone and fax contact details of those registered on the ESA database. The information contains 52 names, email addresses and passwords of 52 internal ESA users.

The traditional password won't exist in 10 years
Security professionals are increasingly moving beyond passwords towards alternative authentication methods according to a new survey.
The study by Wakefield Research for two-factor authentication specialist SecureAuth reveals that businesses across the US are increasing their security budgets and that 91 percent of cyber security professionals agree that the traditional password won't exist in ten years.

The top cyber-security trends of 2015
As 2015 draws to an end, we can look back on a year that has seen cyber security rapidly ascend the corporate, journalist and consumer agendas.
The cost of the average corporate data breach continued to rise, and with hacks on firms such as Car Phone Warehouse, Talk Talk, Ashley Madison and even the Internal Revenue Services in the USA, the last twelve months have seen a marked escalation in Black Hat activity.

Addressing new challenges in enterprise mobile management [Q&A]
Although many enterprises are keen to deploy mobile apps for their workforce and to support BYOD and extended working, they've often been held back by traditional app distribution options. Historically this has required IT organizations to bring devices under management -- for corporate owner, corporate liable, and BYOD devices -- which can put a brake on enterprise mobile app deployments.
To find out how new approaches can allow data to be secured at the app level, we spoke to Mark Lorion, Chief Product and Marketing Officer at mobile app management and security company, Apperian.

2016 set to be the year of malware targeting Macs and iOS
Security has long been an issue for Windows users. The sheer number of devices running Microsoft's operating system makes it a prime target for malware and virus attacks. More recently, Apple's computers have increased in popularity and security firm FireEye says that the company will find itself in the crosshairs in 2016.
It's not just Macs and MacBooks that are predicted to become more frequent targets, iOS is also expected to come under attack. FireEye warns that weaknesses have been found in Apple's walled garden, and this could spell danger for users. Symantec is issuing similar warnings, citing Apple's ever-growing user base as the reason.

Data security is key for customer retention
Nearly two-thirds (64 percent) of consumers worldwide say they are unlikely to shop or do business again with a company that had experienced a breach where financial information was stolen, and almost half (49 percent) had the same opinion when it came to data breaches where personal information was stolen.
This is according to a recent global survey by Gemalto, titled Broken Trust: 'Tis the Season to Be Wary, which surveyed 5,750 consumers in Australia, Brazil, France, Germany, Japan, United Kingdom and United States.
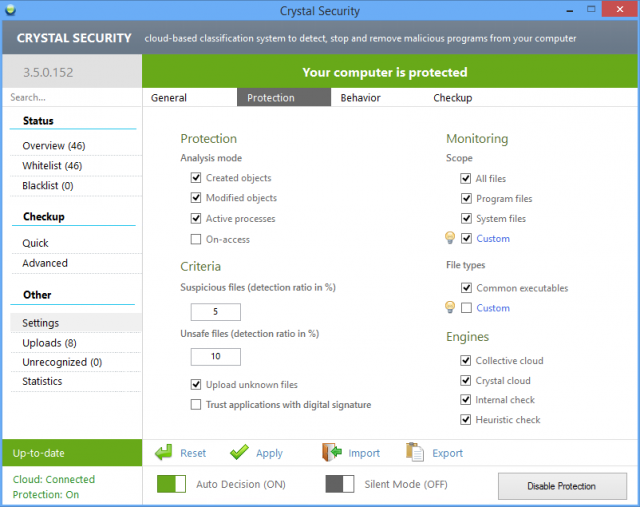
Crystal Security is a compact cloud-based malware detector
Install any anti-malware with real-time protection and you’re generally weighing down your system with services, drivers, DLLs, background processes and more.
Crystal Security does things differently, its tiny download unpacking to a single 830KB executable which runs happily on Windows XP and later.

Xbox Live certificate keys exposed according to Microsoft
A lot of Xbox customers shill out the extra money for a Live account to improve the gaming experience. With the vast amount of Xbox consoles out there, that is quite a few customers. Now Microsoft is acknowledging that the keys for some of those faithful users have been exposed.
Before you panic, this doesn't necessarily mean you've been hacked, but the possibility is there. In a new security bulletin the company claims that the SSL/TLS digital certificate keys for xboxlive.com were exposed and that this could be used by hackers for man-in-the-middle attacks.

Windows 10: Security features for the enterprise
The introduction of mobile into the workplace has destroyed previous enterprise security models, introducing a modern operating system (OS) architecture that puts the employee in the driver’s seat.
At the same time, breaches targeting traditional Windows operating systems are at an all-time high, with over 1 billion records compromised in the last two years.
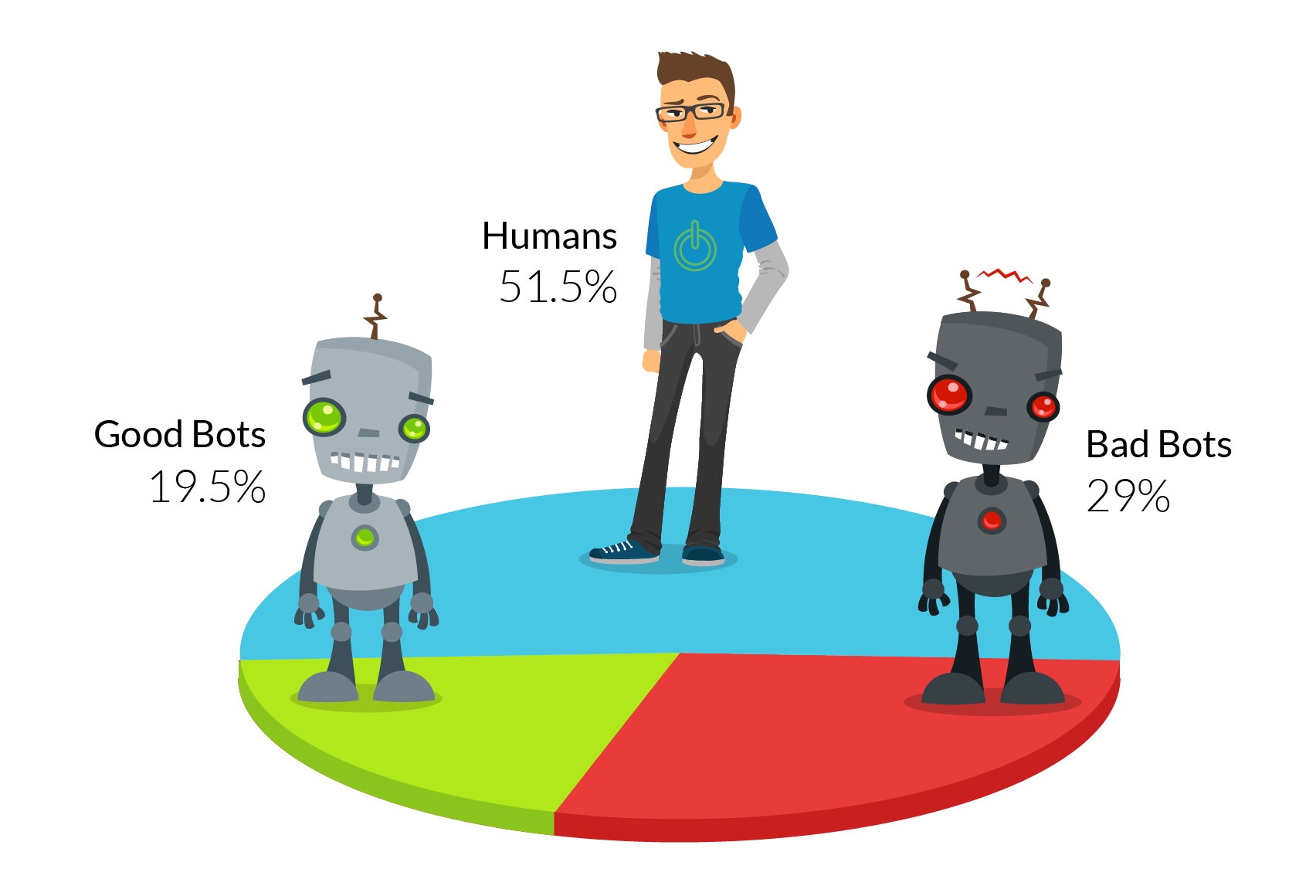
Humans reclaim the web from the bots
For the first time in five years, humans were the ones responsible for the majority (51.5 percent) of all online traffic, up from just 38.5 percent in 2013.
This is according to the latest Imperva Incapsula Bot Traffic Report which shows that good bot traffic decreased, from 31 percent in 2013 to 19.5 percent in 2015, while bad bot traffic remained static, at around 30 percent.

[Updated] Webhost Easily hit by malware attack
UK webhosting company Easily has emailed its customers to inform them that it has fallen victim to a malware attack. COO Edwina McDowall says that the assailant is, as yet, unknown but steps have been taken to eliminate the malware.
The company warns that all customers should change their passwords as a precautionary measure, but seeks to assure people that credit card details have not been compromised.

Retail data breaches threaten customer loyalty
A high percentage of Americans would change their shopping habits if their favorite retailer was hit by a data breach according to a new study.
Data security specialist Vormetric commissioned the survey over 1000 US adults from Wakefield Research which found that for 85 percent of respondents the significant personal consequences that can result from a breach would cause them to find a new place to shop.

EU signs its first cyber-security rules
European legislators have reached an important agreement, as they sign first cyber-security rules for the Union.
The rules, comprised in the Network and Information Security Directive have, among other things, asked tech giants such as Google and Amazon to be more open and transparent about their security, as that will help protect EU’s essential infrastructure, such as air and road traffic control systems and the electricity grid, from cyberattacks.

Connected toys and the IoT could be the next weapons of mass surveillance
Just a few days ago, we heard about the potential for the web-enabled Hello Barbie to provide hackers with personal data. Numerous vulnerabilities open up the potential for data to be stolen, but this could be the start of a worrying trend. If you thought the surveillance activities of the NSA and GCHQ are disturbing, things could be about to get much worse.
There is a movement underway that sees every conceivable device being transformed into a connected device. This is more than just the Internet of Things -- security experts are warning that not only could any devices connected to the internet (including web-enabled toys) could be used to spy on users, placing children at risk.

All businesses share the same cloud security concerns
All organizations have the same key concerns regarding the security of their data in the cloud, according to a new report.
The study by security-as-a-service specialist CloudLock reveals that every organization shares five primary cloud cyber security concerns, regardless of industry. These are: account compromise, cloud malware, excessive data exposure, over-exposed personally identifiable information (PII) and payment card industry (PCI) data, and collaboration.