Fake pirated software hides dropper-as-a-service

Researchers at SophosLabs have uncovered malware being distributed by a network of websites acting as a 'dropper as a service', serving up a variety of other nasty packages.
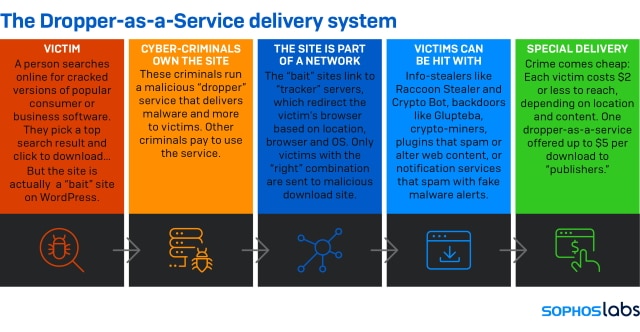
These droppers for hire are delivering bundles of malicious and unwanted content to targets looking for cracked versions of popular business and consumer applications.
The bait sites link to tracker servers, which redirect the victim's browser based on location, browser and OS. Only victims with the 'right' combination are sent to the malicious download site. Victims can be hit with info-stealers like Raccoon Stealer and Crypto Bot, backdoors like Glupteba, crypto-miners, plugins that spam or alter web content, or notification services that spam with fake malware alerts.
It's easy to see the attraction for cybercriminals as each victim is costing $2 or less to reach, depending on location and content. One dropper-as-a-service offers up to $5 per download to 'publishers'.
Sean Gallagher, senior threat researcher at Sophos, says:
Paid download and dropper services have been around for a long time, but they continue to evolve and thrive and make money for the operators behind them. Our research suggests that this success is due in part to the fact that underground demand for account access credentials remains high, and these paid-for services enable less-skilled cybercriminals to implement bulk credential theft and cryptocurrency fraud at minimal cost.
The dropper-as-a-service operators have also adapted to maximize their profits by bundling a range of malicious or unwanted content in each dropper, hitting victims with a raft of toxic applications in a single download.
You might think that people looking for cracked software deserve all they get, but the existence of the DaaS business model means it's likely to be employed elsewhere too. To defend against it Sophos recommends reviewing security software, settings and policies to ensure you can detect and block malicious and unwanted downloads.
More detail about the attacks can be found on the Sophos site.
Image credit: efks/depositphotos.com
