Forget about Fake Cell Towers and Spying Threats: Android 16 Introduces New Security Features

Mobile security enhancements have become an essential part of OS developments. To make mobile security better, Google has announced that Android 16 will include a feature that detects and warns users about fake or insecure cell towers and an often-overlooked threat that can be used to spy on individuals or steal sensitive data.
This new feature is part of strategic efforts by Google to strengthen privacy protections within its mobile ecosystem. As detailed in recent reports from Android Authority, the upcoming version of Android will notify users when their devices connect to suspicious mobile networks, particularly those attempting to gather identifying information or lacking encryption.
16 Billion Passwords Exposed: Major Leak Hits Apple, Facebook and Google Users

The largest password leaks are now recorded. 16 billion login credentials, including usernames and passwords, have been exposed online. The leak impacts Apple, Facebook, Google accounts, and some other platforms that people use daily.
The breach, uncovered by researchers at Cybernews, is believed to be the work of multiple infostealer malware groups operating globally. Their investigation, ongoing since early this year, identified 30 separate datasets, each containing millions of stolen records. Many of these datasets were previously unknown, adding to the severity of this discovery.
Microsoft super-charges Windows Update so it can keep all of your apps up to date

Microsoft has launched a preview version of the Windows Update orchestration platform. This is an update to Windows Update itself which opens it up for use by third-party developers.
This means that Windows Update could soon be able to update not only Windows, but also drivers, and third-party apps. So broad is the scope of what Microsoft is working on that it feels as though Windows Update will soon be a misnomer, and a rebranding may be in order.
Microsoft releases Defender update to improve the security of your Windows installation images

Having Windows installation images is handy; they can be used to reinstall your operating system, but they are also useful when creating virtual machines. Microsoft is concerned about their safety, however.
Pointing to "a Microsoft Defender protection gap" that exists in the first hours of a freshly installed copy of Windows, the company highlights installation images that contain outdated antimalware software binaries. The solution to this problem? An update to Microsoft Defender for these images.
DDoS and IP transit: Why integration is the smart choice for modern connectivity

As Distributed Denial of Service (DDoS) attacks grow in both frequency and sophistication, organizations are being forced to re-evaluate their defensive strategies. Gone are the days when a standalone DDoS mitigation service tacked onto your infrastructure was enough for peace of mind.
The current threat landscape demands faster response times, simplified operations, and coordinated protection. A rising trend is the integration of DDoS mitigation directly with IP transit from a single provider.
Windows 11 hacked multiple times by security researchers at Pwn2Own Berlin 2025

As part of its Zero Day Initiative (ZDI), Trend Micro is holding its first Pwn2Own event in Berlin. The three day event sees security researchers testing and breaching the security of various systems, including Windows 11 and Linux.
With big money on offer, there is a great incentive for researchers to unearth vulnerabilities and show how they can be exploited. And this is precisely what happened with Widows 11; the operating system was pwned multiple times on the first day of the event, and there will be many more attempts made before it is over.
Microsoft will support Office on Windows 10 until 2028 -- but not the operating system
It has been difficult to escape the fact Microsoft is ending support for Windows 10 later this year -- on October 14 to be precise. The company has made much of issuing reminders about this date as well as endlessly pestering people to upgrade to Windows 11.
But it was not just Windows 10 that was to lose support in October. Microsoft had also said that Office (or Microsoft 365) on Windows 10 would not be supported from the same date. Now the company has had a change of heart, and will provide support for much longer than it previously announced.
Active Directory recovery: Rebuilding the forest from root to tip

After 25 years, Active Directory remains a stalwart of IT infrastructure. Supporting access for an estimated 610 million employees, it enables seamless, secure connectivity to the networks that power daily business operations worldwide. Favored by nearly 90 percent of Global Fortune 1000 companies, according to Frost & Sullivan, Active Directory has long been the primary mechanism for enabling staff to connect, collaborate, and work efficiently.
Despite the rise of cloud-based alternatives, Active Directory's scalability, compatibility, and established integration with Windows environments has ensured its continuing appeal for hybrid and on-premise infrastructures. Its unrivaled scalability and powerful centralized control make it the go-to solution for managing users, devices, and policies at scale.
Google is using machine learning to help Android users avoid unwanted and dangerous notifications

Notifications are part and parcel of life, being both useful and interesting. But they can also be problematic. Google is aware that the notifications generated by websites can be “spammy or even deceptive”.
The worst offenders can attempt to trick people into sharing personal information or downloading dangerous software. Google is using machine learning to fight back, launching warnings about warnings of unwanted notifications.
Microsoft now has AI agents that can change Windows 11 settings -- should we be delighted or terrified?
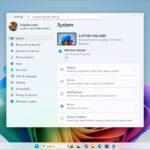
Artificial intelligence is now all but unavoidable, and Microsoft is taking every opportunity to crowbar more AI features into Windows 11. Copilot+ PCs are a big part of the company’s AI vision and now powerful new AI agents have been unveiled.
Described as being part of a “new generation of Windows experiences”, Microsoft has revealed new agents that use on-device AI to interpret natural language input to help a user find and change system settings. What could possibly go wrong?
Microsoft sees the future as passwordless; all new accounts will be password-free

It is a year since Microsoft embraced passkeys for user accounts, and now the company is taking things further. With passkeys having been conceived as a replacement for passwords, any newly created Microsoft account will be passwordless.
This is not just a change that is about improving security (passwords having been shown time and time again to be highly fallible), but also user experience. The passkey-by-default approach now being adopted is part of a streamlining of UX for sign-ins.
These are the cybersecurity firms Microsoft rates highest in 2025
Microsoft has announced the winners of its 2025 Security Excellence Awards. The event, held in San Francisco during the lead-up to the RSA Conference, is like the Oscars, but for infosec, and celebrates partner organizations and individuals for their contributions to cybersecurity.
The awards panel considered partner nominations across eight main categories, selecting five finalists in each based on technical execution and impact. Winners were picked through a combined voting process involving Microsoft and its Intelligent Security Association (MISA) members.
Microsoft will start charging for Windows Server hotpatch updates in two months

The arrival of hotpatch updates for Windows Server 2025 heralded a new era of keeping systems up-to-date and secure while keeping downtime to an absolute minimum. By eliminating the need for restarts after certain updates, systems can be patched while they are being used.
Hotpatching for Windows Server 2025 has been available in preview for a number of months now. It has been completely free of charge, but this is due to come to an end. Anyone who has fallen in love with the new approach will have to pay if they want to continue using it.
Kali Linux users warned that updates are likely to fail for a few days

Showing that it is not just Windows 11 that has issues with updates, Offensive Security has issued a warning that Kali Linux updates are likely to fail “in the coming days”.
The Linux distro has proved an important tool in penetration testing, acting as a valuable security tool for many users. The team behind Kali Linux says that “pretty much every Kali system out there will fail to update”, and it bears full responsibility: “This is not only you, this is for everyone, and this is entirely our fault”. But there is a solution.
From compliance to culture: Making security part of our daily routines

Every organization, sooner or later, writes itself a policy. It gets stapled into onboarding packs and waved about during training, and then quietly forgotten. It’s not that people mean to ignore it. It’s just that rules don’t always make themselves felt when the Wi-Fi’s down or the finance team’s in a rush. But culture -- that’s different. Culture settles into the way people think and work and react. It turns guidelines into instincts. That’s when you know security has taken root.
Understanding this shift often begins with a question: what, exactly, are we securing -- and how do we keep track of it all? Which is where you'll find DSPM explained in any sensible conversation. Data Security Posture Management (DSPM) refers to the ongoing process of identifying, monitoring, and reducing risks across sensitive data. It’s less about locking everything up and more about seeing clearly -- knowing where the data is, who can access it, and what it’s doing. The benefit isn’t just technical; it’s cultural.
Recent Headlines
Most Commented Stories
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.