
Google shows its commitment to Secure by Design
In an ever more interconnected world facing growing numbers of cyberattacks, it's critical to ensure that technology systems are resilient in order to keep people safe.
Google has announced that it's signed up to the CISA's Secure by Design pledge, a voluntary commitment to specific security goals.

Old credentials never die they just present a cloud security risk
Long-lived credentials on major cloud platforms continue to be a huge risk for organizations, according to a new report from Datadog.
Long-lived cloud credentials never expire and frequently get leaked in source code, container images, build logs and application artifacts, making them a major security risk. The report finds that 46 percent of organizations are still using unmanaged users with long-lived credentials.
Manufacturing businesses most likely to be hit by cyberattacks
The manufacturing industry is the most affected by cyber attacks, accounting for over 25 percent of all incidents, across the top 10 industries, of which 45 percent are malware attacks.
According to a new report from security awareness training company KnowBe4 the industry has become increasingly attractive to cybercriminals in recent years due to its interconnected nature, having a low tolerance for downtime, and valuable intellectual property stored in its databases, which could save competitors millions if obtained.

Why it's critical to secure your APIs [Q&A]
APIs are essential to the smooth running of the internet, allowing the seamless transfer of information between applications and services.
Of course all of this happens behind the scenes but that's not to say that APIs should be ‘out of sight out of mind'. We spoke to Mayur Upadhyaya, CEO at APIContext, to learn more about API Security and the importance of APIs in general.

Are we starting to give up on cyber hygiene?
A new survey of over 7,000 individuals suggests a growing wave of pessimism among workers regarding cybersecurity practices.
The study from CybSafe and the National Cybersecurity Alliance shows 53 percent believe staying safe online is possible, down by five percent from last year, while only 60 percent think online safety is worth the effort, marking a nine percent drop.

Cyber resilience vs. cybersecurity: Which is more critical?
Today, it’s not ‘if’ but ‘when’ any organization will be compromised. So, while it’s essential to strengthen cybersecurity across the entire organization, it’s also imperative to plan for a significant cyber-attack and the worst-case scenario. No business can be 100 percent secure but they can be resilient. Resilience is about continuing to thrive amidst adversity. This is why cyber resilience can be more important than cybersecurity. Every organization can take positive actions to improve their cyber resilience today, ensuring they can continue to win even if they are affected by an incident. They can start by having the right mindset and instilling a culture of cyber security and cyber resilience.
Strong cyber resilience will enable an organization to continue to operate key business processes, even when they are under attack. This means keeping people safe, guaranteeing data security, and protecting their reputation with their customers, partners, suppliers, industry and government regulators and other key stakeholders. Having a strong cyber resilience will save stress, time and money -- it will give you a return on your investment -- and you’ll be better prepared for uncertainty in the future.

Cyberrisk quantification and how to measure it [Q&A]
Enterprises face an increasing range of cybersecurity risk, but quantifying and managing those risks can be a difficult task.
Recent Gartner research shows that more companies are trying to roll out cyber risk quantification (CRQ) in order to get a greater understanding of their risk profile.

Ransomware still a major threat despite disruption to RaaS groups
Ransomware remains a formidable threat facing organizations, with 49 active groups impacting more than 1,000 publicly posted victims in the third quarter 2024, according to a new report.
The report from GuidePoint Security's Research and Intelligence Team (GRIT) shows threat actors are increasingly leveraging legitimate services and platforms to deliver targeted phishing messages. While the abuse of trusted notification services is not a new approach to delivering malware, the research team has recently observed novel -- and progressively sophisticated -- delivery techniques.
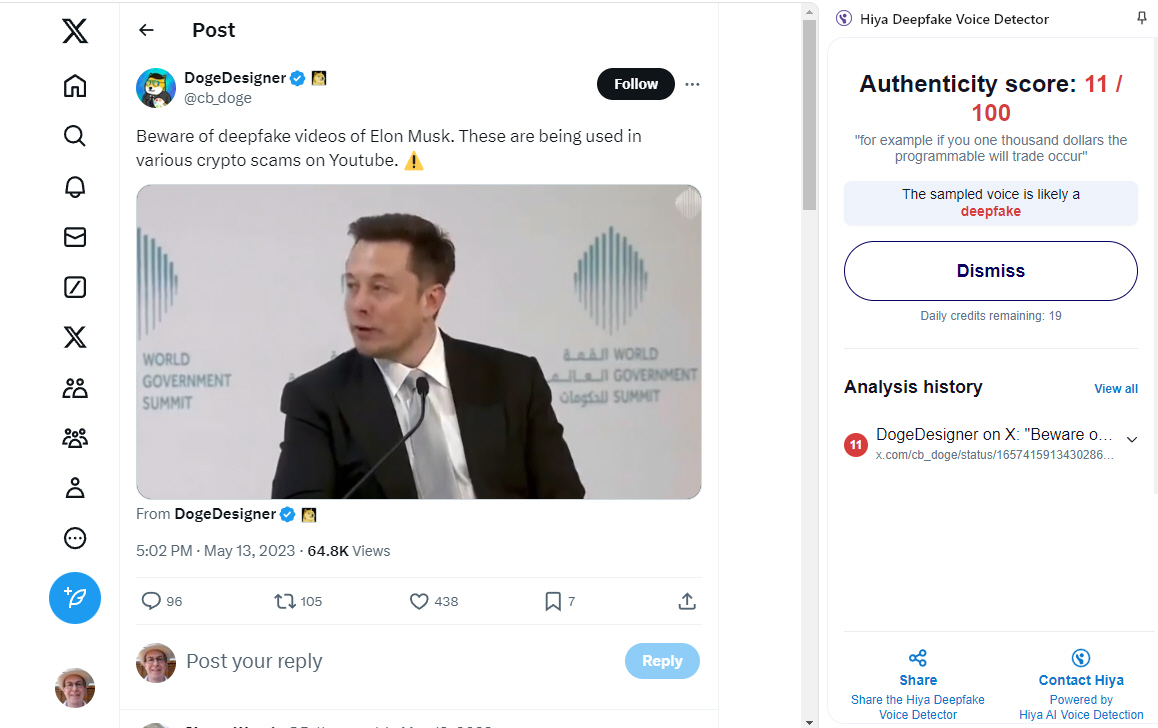
New Chrome extension helps spot deepfakes
Deepfakes are becoming more of a problem and particularly around election times they can seek to influence voters views. They're also getting better so it can be hard to know if what you're watching or hearing is real or fake.
To combat this issue voice security company Hiya has launched a new plugin for the Chrome browser designed to identify video and audio deepfakes with up to 99 percent accuracy, by simply analyzing a few seconds of audio/voice.

Business overconfident and underprepared for cyber threats
A new report from digital transformation consultancy Gemserv, based on a survey of CISOs at 200 large UK and EU enterprises, finds most believe boards are overconfident of their understanding of cybersecurity issues, and are failing to provide CISOs with the support they need to properly protect the organization.
According to the findings, 88 percent of CISOs think the threat landscape is becoming more complex, with 37 percent not confident they have the resources they need. 44 percent struggle to recruit and retain the skilled people they need, amid a 3.2m 'workforce gap' for IT talent.

AI outpaces ability to secure data
The rush to embrace AI, especially generative AI and large language models, has outpaced most organizations' ability to keep their data safe and effectively enforce security protocols according to a new report.
The study from Swimlane shows 74 percent of cybersecurity decision-makers are aware of sensitive data being input into public AI models despite 70 percent having established protocols in place.

Over 80 percent of hackers believe the AI threat landscape is moving too fast to secure
A new report from Bugcrowd finds 82 percent of ethical hackers and researchers on the platform believe that the AI threat landscape is evolving too fast to adequately secure.
Based on responses from 1,300 users of the platform, the report also finds that 71 percent say AI adds value to hacking, compared to only 21 percent in 2023. In addition, hackers are increasingly using generative AI solutions, with 77 percent now reporting the adoption of such tools -- a 13 percent increase from 2023.

CISOs concerned about attackers using AI
Data from a recent survey conducted by RSA Conference shows that 72 percent of Fortune 1000 CISOs say they have already seen threat actors using generative AI against their organization.
AI-generated phishing emails are the top threat, with 70 percent of CISOs reporting that they've observed highly tailored phishing emails targeting their business Other top GenAI threats include vishing (37 percent), automated hacking (22 percent), deepfakes (21 percent) and misinformation (17 percent).

Dark web activity targets US election
A new report from Fortinet shows a range of activity around the upcoming US election including phishing scams aimed at voters and malicious domain registrations impersonating candidates.
Threat actors are selling affordable phishing kits on the dark net designed to target voters and donors by impersonating the presidential candidates and their campaigns.

A quarter of cybersecurity leaders are ready to quit
A new survey finds that 24 percent of CISOs or IT security decision makers (ITS DMs) are actively looking to leave their position.
The research, commissioned by BlackFog, finds that a further 54 percent, while not actively looking to quit, are open to new opportunities.