
New ransomware targets Office 365 users
A new zero-day malware has been discovered in Australia that affects all of Microsoft’s Office 365 products including Word, Excel, PowerPoint and Outlook.
The malware was discovered by the cyber security company Check Point and comes in the form of an invoice sent by email. The attack is designed to catch unsuspecting victims according to security analyst Raymond Schippers who said: "The email sent to Office 365 users via Outlook gives the appearance of an invoice in the form of an Office document. When they go to open it, a message will appear telling people the document was created with a previous version of the software, so they will need to click something to enable the content".

Chrome flaw makes it possible to copy DRM video streams such as Netflix
Security researchers from Ben-Gurion University Cyber Security Research Center (CSRC) have unearthed a vulnerability in Google Chrome that can be exploited to make copies of DRM-protected video streams. The problem affects all Chromium-based browsers, and makes it possible to circumvent Widevine encryption technology Google uses to secure streams.
Widevine has been used in Chrome for a while, after Google acquired it back in 2010. It has been used to prevent piracy of premium YouTube channels, and is also used to protect Amazon Prime and Netflix streams. Google was informed about the problem back in May, but is yet to issue a patch.

Apple is leaving the iOS 10 kernel unencrypted... to increase security
Each new version of iOS is eagerly awaited, and at its Worldwide Developer Conference (WWDC) Apple unveiled a preview of iOS 10. Much has been made of the new features, but developers probing the operating system are making a surprising discovery. The kernel of iOS 10 is unencrypted.
In the current climate of security-awareness, this might seem like something of an unusual decision. But Apple says that the change has been made to improve performance, and it could even help to increase security.

Think twice before accepting LinkedIn invitations from strangers
Have you ever wondered if someone on LinkedIn is not really who they say they are? I’m not being paranoid here, this is a legitimate question.
If your answer is "No", you’re not alone. A vast majority of people never wonder if there are fake accounts requesting to connect on the professional social network, and almost a quarter accept requests from people they don’t really know.

90 percent of Android devices vulnerable to Godless malware
When we take a look at the Android distribution updates that Google posts every month one thing seems to never change, and that is the overwhelming number of devices that run an outdated version of the operating system. As of early-June 2016, nearly 90 percent of the handsets with Google Play access are rocking Lollipop, Jelly Bean or another old distribution. Meanwhile, Marshmallow powers only 10.1 percent of Android devices.
And, as Trend Micro security researchers point out, that can be a serious problem in terms of security as there is a new family of malware, known as Godless, that affects "virtually any Android device running on Android 5.1 (Lollipop) or earlier". Using Google's figures, that's 89.9 percent of the Android handsets in use. What's really worrying is that this malware is actually linked to apps available in major app stores, like Google's Play, and it has already made 850,000 victims across the globe.

Crypto-ransomware attacks increase five fold
Ransomware has become a big problem in recent years, particularly crypto-ransomware, which encrypts data on users' systems. New research by Kaspersky Lab looking at how it’s evolved over the last two years points to just how big.
Among the findings are that the number of users attacked with crypto-ransomware rose 5.5 times, from 131,111 in 2014-2015 to 718,536 in 2015-2016. The total number of users encountering any type of ransomware between April 2015 and March 2016 also increased by 17.7 percent compared to the period April 2014 to March 2015.

Microsoft launches data protection tool for enterprises
As businesses rely more on mobile and cloud systems, greater emphasis is placed on protecting their information while retaining the productivity benefits.
Microsoft is launching a new service to help businesses guard their data as it travels between devices and servers. Azure Information Protection builds on both the existing Microsoft Azure Rights Management (Azure RMS) and the company's acquisition last year of information protection business Secure Islands.

DoD's Hack the Pentagon will include more systems and networks
In an effort to find more security flaws in its defense systems, the US Department of Defense (DoD) has decided to expand its Hack the Pentagon program to include more of its systems and networks.
The program pays hackers to find and report the vulnerabilities in exchange for payment from the US government. So far the program has proven to be quite effective with the the first bug in the DoD’s systems and networks being discovered a mere 13 minutes after its launch.

Lookout uses network layer security to expand mobile protection
The shift towards a mobile and cloud focused workplace has brought a great deal of flexibility but it's also added new risks. How do you protect data when employees can access it at any time and from any device?
Lookout, a specialist in securing mobility, has expanded expanded Mobile Threat Protection with the introduction of Network Protection, an automatic on-device analysis of network connections to defend against man-in-the-middle attacks and ensure information is being securely transmitted.

SMBs lack the resources to combat ransomware
Owners of small and medium businesses in the US recognize the potential of ransoware to disrupt their operations, but 84 percent say they wouldn't pay cyber criminals in the event of an attack.
Yet the survey by data security company IDT911 also shows that company assets and business operations are left highly vulnerable as nearly 75 percent don't have cyber insurance, or are unsure if their policy includes cyber protection.
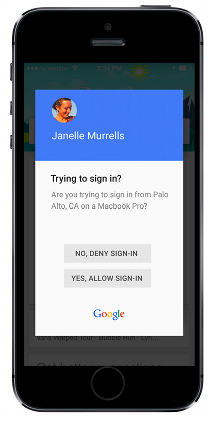
Google prompt makes two factor authentication less of a hassle
Two factor authentication is one of the most convenient options for securing a user account, which is why you will find this feature available in many of the top cloud services. It can be argued though that it can be made even easier to deal with, specifically in cases when users frequently need to access their accounts from new devices.
The problem there is that, the way that it is typically implemented, users usually have to get a verification code via SMS or retrieve it from a dedicated app to finish the authentication process, which is something that many folks may find very annoying over time. So, to make the whole process easy for its users, Google is now rolling out a new option for two-factor authentication, known as Google prompt.

UK government wants to fine companies for data breaches
Even though the TalkTalk hack happened last October, it’s still sending ripples through the cyber-security world. The Department for Culture, Media and Sport has given a number of recommendations, following the breach.
Among the recommendations is the idea of fining companies that fail on cyber-security, as well as the idea of linking the CEO’s pay to effective cyber-security.

USB devices still represent a major security threat for enterprises
With the increasing move to the cloud, it may seem that USB storage devices are becoming obsolete. However, research by endpoint protection company CoSoSys suggests that USB still has a place.
The survey of 2016 Infosecurity Europe visitors looks at the use of USB storage devices in the enterprise and the policies governing them.

Warning! GoToMyPC hit by password hackers
By their very nature, remote access tools represent something of a security risk. It's only a couple of weeks since TeamViewer users complained about account hijacking, and now GoToMyPC has been hit by hackers.
The service has been hit by what is being described as a "very sophisticated password attack", and the company is advising all users to reset their passwords. Details are a little thin on the ground at the moment as an investigation is currently underway, but users are warned to monitor their account and change their passwords.

Acer store hacked and customer credit card data stolen
The internet seems to be a series of high-profile attacks stealing all sorts of data. We've seen this event carried out across websites and retail locations, Login information, passwords, credit cards, it's all fair game to those who wish to do harm.
The latest is with the Acer store, which is claiming the credit card information, user names and passwords for some 34,500 users has been stolen. The company has sent out emails to customers to notify of the breach.