
IT pros have bad security habits
Double standards, double standards everywhere. Our IT bosses might force us to change our passwords every so often, but they rarely change their own credentials, even though theirs offer administrative privileges.
Those are the results of a new survey conducted by cyber security vendor Lieberman Software. The company had asked 200 IT professionals at RSA Conference 2016 about their password changing habits.
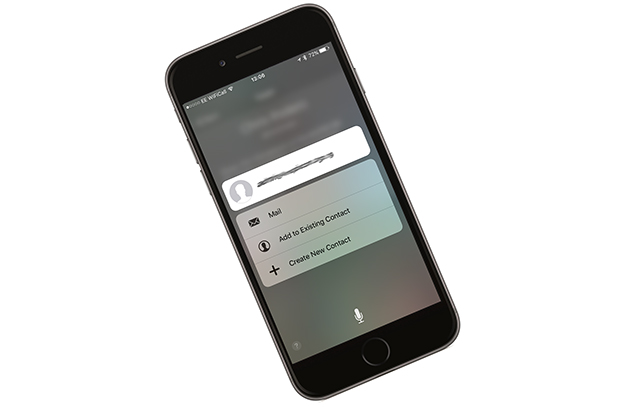
iPhone 6s security flaw lets anyone bypass the passcode and access contacts and photos
It might have taken the FBI quite some time to find a way to unlock a shooter's iPhone 5C, but it turns out to be trivially easy to access contacts and photos stored on the company’s newest flagship, the iPhone 6s.
The trick makes use of Siri and Twitter, and as the owner of a 6s I’ve been able to test this method myself, and can confirm not only that it works, but it’s very simple to implement.

Mossack Fonseca hack exposes shady financial practices of world's rich and famous
One of the largest data breaches in history has resulted in the leak of eleven million confidential documents -- around 2.6TB of data -- from financial firm Mossack Fonseca, one of the most secretive companies in the world.
According to the BBC, the leaked documents reveal how "Mossack Fonseca has helped clients launder money, dodge sanctions and evade tax". The client list features some of the world’s richest and most influential people -- including 12 current or former heads of state -- and their irrepressible greed has now been laid out for all to see. The data shows how thousands of off-shore shell companies have been created in order to hide money from the tax man and also reveals "a suspected billion-dollar money laundering ring involving close associates of Russian President Vladimir Putin".

The threat of ransomware is so great, the US and Canada issue joint security alert
Malware is far from being a new problem, but the inexorable rise of ransomware has taken many by surprise. There have been a number of very high profile instances of ransomware such as PETYA, and the threat is perceived as being so high that the US and Canada have taken the unusual step of issuing a joint security alert.
The likes of TeslaCrypt 4 feature 'unbreakable encryption' and use scare-tactics to encourage victims to part with their money. This is what has prompted the joint alert from the US Department of Homeland Security and the Canadian Cyber Incident Response Centre which warns about "destructive ransomware variants such as Locky and Samas". Interestingly, the advisory actively discourages victims from bowing to ransom demands.

93% of UK mobile users have their location tracked every day
Awareness of the privacy issues involved in using various devices and software has grown dramatically in recent years -- there can be few readers who do not know about the telemetry and privacy concerns surround Windows 10, for instance. But a new campaign by privacy-focused advocacy group Krowdthink aims to raise aware of the privacy implication of owning a mobile phone in the UK.
The 'Opt me out of Location' campaign aims to highlight the fact that nearly every single mobile phone owner in the UK (93 percent) has unwittingly signed up for a contract that permits their location to be tracked. More than this, the data collected allows providers to build up highly detailed customer profiles which Krowdthink warns leaves millions of users just one serious data breach away from having private data exposed to and abused by criminals.

Biometric Authentication: Making mobile devices and apps safer
According to comScore, from September 2010 to September 2014, smartphone usage increased by 394 percent, while tablet usage rose by an astronomical 1,721 percent in the United States. So it’s certainly no surprise that mobile payments are predicted to skyrocket over the next five years. mobilThis shows that the global mobile payment volume in 2015 was 450 billion U.S. dollars, and projects that number to surpass 1 trillion U.S. dollars in 2019.
With the growing interest in and use of mobile devices and payments, users are rightfully concerned with cybersecurity threats. To combat these threats, there has been a surge in using biometric technologies for user authentication.

How to stay safe using public Wi-Fi hotspots
One of the most convenient things about connecting to the Internet through your computer, tablet, or smartphone is being able to tap into public Wi-Fi from pretty much anywhere. These days, there are hotspots available all across the country, so you’re practically never without Internet access. However, it’s a smart move to be cautious when it comes to connecting to public Wi-Fi.
When you’re tapping in to an unfamiliar hotspot, you could potentially be putting your personal data -- and the security of things like your bank accounts, your passwords, and your identity -- at risk. Even if a public WiFi hotspot looks secure, you might still miss the small red flags that signal trouble. Let’s take a look at how public WiFi works to connect you to the Internet, some risks that come with it, and how to ensure you’re keeping your data safe while you’re on a hotspot.

Consumers would trust PIN authentication for online transactions
Nine in ten (90 percent) of frequent online shoppers are confident that PIN is a good authentication method for mobile commerce transactions. Those are the results of a recent survey by myPINpad, provider of multi-factor authentication technology for touchscreen devices.
Following the survey, the company has released a new report, entitled PIN: From Brick to Click, which takes a closer look at the PIN, and if consumers are ready to use it on their smart devices the same way they use it, for example, at ATM machines.

How UK tech companies could comply with Snoopers Charter
It would be hugely ironic if the UK government’s plans to help it seize back control of the digital age actually pushed technology firms even further down the path of encryption.
The second version of the Investigatory Powers Bill -- or Snoopers Charter, as it has been colloquially dubbed -- was published by the Home Office on March 1. This came in light of criticism of the first version -- published in December -- from three parliamentary joint committees: the Science and Technology Committee, the Intelligence and Security Committee, and the Joint Committee for the bill itself -- which made some 86 recommendations alone.

The right PC can improve job satisfaction
Do you want satisfied workers? Give them a well-designed PC, a good and secure mobile device, and let them work when they want to, where they want to. Those are, in a nutshell, the results of a new research by Redshift Research, which had polled 1,016 people, across France, Germany, the UK, Italy, Netherlands, Spain and Switzerland.
For 90 percent of IT decision makers, device security is a current concern, because in the last 12 months, a quarter of Europe’s businesses have been breached. That has resulted in less than a third (32 percent) being completely confident in the level of security offered by their current devices.

LookingGlass releases new threat intelligence platform
Using threat intelligence helps enterprises to improve decision making when it comes to managing security incidents and enforcing policy.
Threat defense specialist LookingGlass Cyber Solutions is looking to improve the way analysts and security operators interpret threats targeting their organizations with the launch of its new ScoutPrime threat intelligence management platform.

Mozilla brings better security to Firefox for iOS
Security has been in the news since Edward Snowden; before actually, just not as prominently. Now, in recent weeks, the headlines have focused on Apple over its iPhone dispute with the FBI, a saga that seems to have come to an end recently.
That is not, however, the only security that needs to be part of our daily lives. Web browsers represent yet another problem and most are working to add layers of protection for customers.

FBI issues warning over MSIL/Samas ransomware
The FBI has began seeking the assistance of companies in the US to streamline its investigation on an increasing ransomware threat in the country.
The FBI is looking into a strain of ransomware called MSIL/Samas, which has been encrypting data across entire networks rather than single computers, Reuters reports. The ransomware infects machines before encrypting data and asking for money in return of the access.

New program ensures enterprises are prepared for cyber attacks
If a data breach happens customers expect a fast and reassuring reaction from the company affected. It's therefore crucial for businesses to have an incident response plan, but often those plans are only tested when a breach occurs.
According to an upcoming survey from customer security company AllClear ID the two most common challenges during a breach response are people related, with 66 percent citing internal politics and 60 percent "too many cooks in the kitchen".
The changing role of the firewall in network security
The firewall is still at the center of most network security strategies, but it needs to evolve as cloud technology, software defined networks and next generation firewalls take hold.
This is among the conclusions of the latest State of the Firewall Report from network security specialist FireMon, which finds that 91 percent of IT security professionals believe firewalls are still as critical or more critical than ever to their security architecture.