
How 'fake' video downloads can install malware
It’s been a common Windows malware trick for years: you download some dubious video, it claims it won’t play unless you install a "codec", but the file you’re offered is a Trojan or virus. Oops.
You might think you’d never be caught out by something so obvious, but it only takes a moment, you’re not paying attention, and -- too late.

Smart TVs pose huge security risks
Over the past few years we have seen everyday items such as refrigerators, lighting and heating systems and even kettles all of a sudden becoming "smart". In fact there are now more smart items on the planet than smart humans, or in fact any type of humans, with an estimated 13.4 billion devices currently connected to the Internet. This is not necessarily a problem -- until, of course, hackers start exploiting these devices to gain access to your home or work networks.
Most people would never even suspect that their television set could be hacked, yet this is happening, in research labs at least, with greater frequency. In one recent example, security company Avast demonstrated a hack of a Vizio Smart TV enabling root access to the TV’s underlying Linux operating system. Last year I also found that this flaw involving a maliciously crafted SSID value could be exploited with a USB device. After exploiting this flaw, the attacker has access to everything connected to the home network of their victim. Avast also demonstrated what a man-in-the-middle (MITM) attacker (such as an intrusive government or ISP) could learn by monitoring network traffic from the TV set.

These are the worst passwords of 2015 -- are yours on the list? If so, change them now!
While it is easy to put someone down for engaging in poor security practices, remember -- not everyone grew up with computers. In other words, for some people, modern technology and security are foreign concepts. With that said, people of all ages -- old, young, and in-between -- are guilty of doing stupid things, such as using poor passwords.
Speaking of passwords, many sites mandate specific requirements, such as using a mix of capital and lowercase letters, numbers, and special characters, arguably minimizing the possibility of very weak passwords, such as "password". Sadly, people are still using poor passwords, and today, SplashData shares its list of the worst passwords of 2015. If any of your passwords are on the list, you should change them immediately, and probably go to bed without supper -- shame on you!

Linux vulnerability puts millions of people at risk -- Android users should panic
There are so many reasons to use a Linux-based operating system. Most often, people tell me that they switched because of a dissatisfaction with Microsoft's Windows. The second most common reason people tell me that they use Linux is for security -- a lack of malware. While operating systems such as Ubuntu, Fedora and Debian are rock solid, no operating system is impervious to viruses or trojans. The moment you feel 100 percent safe, you have effectively let your guard down.
While Linux-based operating systems are arguably more secure than Windows, every so often a vulnerability pops up to bring users down to Earth. Today, a rather nasty such vulnerability rocks the Linux community, as millions are at risk. And yes, this includes the oft-denounced Android.
Internet of Things' rising popularity will increase security risks, business costs
We all know that the Internet of Things is growing, and more and more firms are using the new technology to take their businesses to the next level, but just how big is IoT now, and how much will it grow?
Gartner has given a few interesting predictions, including one which says that more than half of all new business processes and systems will use some form of IoT by 2020.

France joins the Netherlands in saying no to cryptographic backdoors
Secure communications exist for many reasons, including free speech from behind the borders of certain nations, to business secrets being discussed. These days it's under attack from several sectors, including law enforcement agencies investigating crimes and those who claim to need info for catching terrorists -- something we've recently found can be futile in some cases.
Just the other day we heard that the state of New York is looking to legislate backdoors into mobile devices, a law that seems unlikely to pass, given the amount of opposition and evidence against it being effective to anyone but the hackers, who are likely to be quick to find these openings.

BlackBerry denies existence of security backdoors and blames 'cracked' encryption on user error
BlackBerry has spoken out to deny claims that its encryption has been cracked by groups associated with the police in the Netherlands. The company has long-prided itself on the level of security it offers, but that security has been called into question recently.
Reports circulated that Mexican drug lord El Chapo was able to be found partly because of his decision to use a BlackBerry (specifically a BlackBerry Z30, fact fans) to arrange interviews with actor Sean Penn. Coming after claims by the Netherlands Forensic Institute (NFI) that it had been able to decrypt hundreds of encrypted emails on a BlackBerry handset, the Canadian company felt compelled to respond -- by blaming user error.
Cyber attacks on industrial Internet of Things are on the rise
The United States government has revealed that it has detected a rise in cyber criminal attacks on industrial control systems.
The concern is that with leading manufactures and grid power producers’ early adoption of the industrial internet of things -- and Industry 4.0 which are commercial and industry versions of the Internet of Things -- sufficient safeguards have not been put in place to protect them from the internet.

LastPass has serious flaw called 'LostPass' -- your passwords and more are at risk
Remembering passwords is difficult nowadays. Between all of the crazy site-mandated requirements and the directive of never reusing the same password on multiple sites, the human brain is outmatched. It is for this reason that I, and many others, swear by password managers. Not only do they securely store login credentials, but can generate ultra-secure passwords too.
While there are many companies that offer such solutions, I stick with LastPass. Why? Linux. Yes, LastPass is one of the only solutions that works with all major operating systems, including Linux distributions. By default, many users of Ubuntu, Fedora, Chrome OS, and more, choose LastPass because there aren't many other options. Sadly, today, it is revealed that this password manager is at risk of a nasty phishing vulnerability. The author, Sean Cassidy, has published details about what he has dubbed 'LostPass'.

New York is trying to force backdoors into phones with legislation
Cryptography has become popular in the post-Edward Snowden era. Everyone seems to be worried about being spied upon and is looking for ways to avoid it. While the majority of users likely have nothing to hide, it's still a creepy feeling to know that someone can, and possibly is, checking what you say and do.
There has been a lot of talk about adding backdoors, mostly from those who want to spy and those who simply don't understand the technology. The latest of this is currently taking place in New York.

ISIS has its own secure messaging system -- this illustrates the futility of communication surveillance
Moves by governments to monitor web-based communication with a view to thwarting terrorism is utterly, utterly futile. Just like the NSA's dragnet-style dredging for intelligence, mass communication surveillance does little to home in on target -- the ones that government should be concerned about are the very ones who know who to evade detection.
This is something that was perfectly demonstrated this week when it became apparent that ISIS has developed its own secure messaging system. No longer reliant on the likes of WhatsApp, ISIS is using a custom-built, Android-based encrypted messaging tool that is incredibly difficult -- if not impossible -- for the FBI and NSA to monitor.

Error 404: Security insights found
This year has been another brutal one for breaches and data loss, with 400 new threats emerging every minute by some reports. Most security administrators and architects have been shoring up defenses inside networks in order to better detect places of compromise and attacker movement. Many organizations recognize that one of the fastest ways to beef up detection capabilities is to add context-based network analytics like those provided by Security Information and Event Management (SIEM) systems and NetFlow security analyzers.
Adoption has been brisk, the SIEM market is one of the strongest with a forecasted growth of 12 percent annually reaching $4.54 billion by 2019. And recently, Cisco further highlighted the importance of network telemetry to security with the acquisition of NetFlow analysis veteran Lancope for $453 million.

Security vulnerabilities, exploits are on the rise
It’s been a busy year for security firms everywhere -- cyber-attacks, malware, ransomware and other malicious online behavior reached new heights in 2015.
Those are the results of a report by Bromium, a company which deals in threat isolation in service of data breach prevention. Its report, entitled Endpoint Exploitation Trends 2015 analyzed the security risks of popular websites and software.

Your smart doorbell may let in unwanted visitors
It seems everything can be put online these days -- lights, window shades, door locks, refrigerators, crock pots, you name it. One popular item being advertised vigorously in the US is the smart doorbell. It's a nice idea as it allows the user to see who's at the door without opening it. You can even talk to visitors and all of this is done from an app on the smartphone, even if you aren't actually home.
But, as we've seen with other IoT devices, this isn't always safe. These days even your daughter's Barbie doll has security concerns.
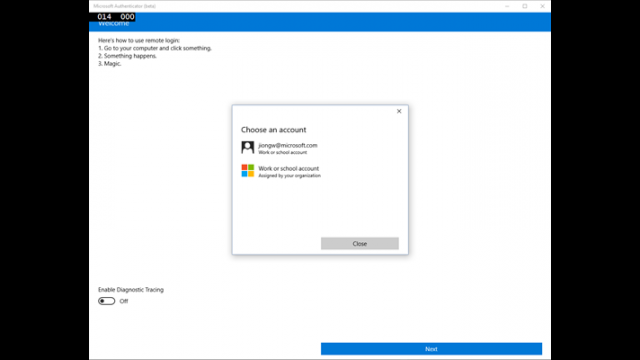
Microsoft will let you unlock your Windows 10 PC with an app
Microsoft plans to give Windows 10 users another option to speed up the process of unlocking their PCs. The software giant has introduced an app that enables remote authentication using a Windows 10 Mobile device.
Called Microsoft Authenticator, the app is currently undergoing internal testing and it seems to be designed with enterprise users in mind. Microsoft likely wants to make it easier to deal with complex passwords, which are recommended for meeting certain security guidelines.