83 percent of IT and engineering professionals bypass security controls

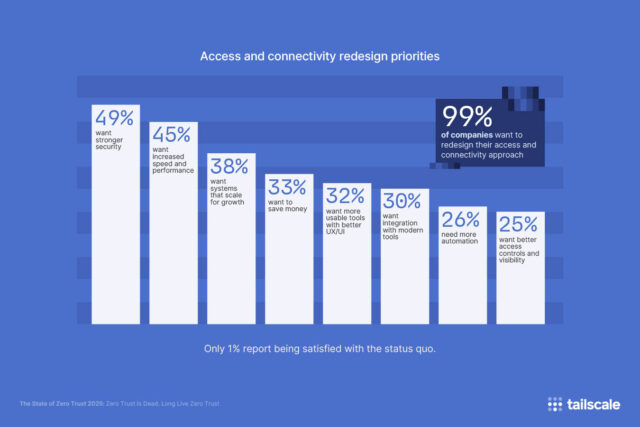
A new survey of 1,000 IT, security, and engineering professionals across North America uncovers a fractured landscape of legacy VPNs, slow manual processes, and overlapping tools -- with 99 percent of respondents saying they'd like to redesign their company’s access and networking setup from the ground up.
The study from Tailscale also shows that 83 percent of IT and engineering professionals admit to bypassing security controls in order to get their work done. Also worrying is that 68 percent say they have retained access to internal systems after leaving a previous employer, revealing critical gaps in offboarding and identity lifecycle management.
More than two-thirds of engineers say IT and security policies actively block or misunderstand their workflows. At companies heavily reliant on VPNs, employees are nearly twice as likely to report broken access or security workarounds compared to those using more modern tools.
“Security and productivity shouldn’t be at odds,” says Avery Pennarun, CEO of Tailscale. “When developers, engineers, and IT all say the current system is broken -- and worse, start working around it -- that’s a sign the tools need to change, not the people. Zero Trust can solve this, but only if it’s actually implemented as a strategy, not just used as a buzzword.”
But although many organizations claim to be on a Zero Trust journey, the report reveals that most haven’t got there yet. Just 29 percent use identity-based access as their primary model, and 68 percent still manage access controls manually, introducing delays and risk. Many companies are juggling too many point solutions, for example 92 percent use multiple tools for network security, and nearly one-third use four or more.
There are some encouraging signs of progress, however. Nearly half of companies say they are actively trying to consolidate their toolsets, and early adopters are moving to identity-first architectures and just-in-time access models that offer better security and a smoother user experience. AI and automation are also emerging as key enablers of adaptive policy -- not just detecting threats, but adjusting access dynamically in response to context.
The full report is available from the Tailscale site.
Image credit: olly18/depositphotos.com
