
Maximizing AI ROI In healthcare by establishing an automation-first mindset [Q&A]
AI use cases in healthcare continue to expand, and organizations are identifying opportunities to leverage automation technologies to improve existing workflows.
However, after years of implementing new tooling and expanding tech stacks for better efficiency and backend processes, most organizations are left with disparate systems and datasets that make AI initiatives difficult to put into practice. IT teams are now forced to work backwards, embarking on time and resource consuming efforts to determine how automation can work within the parameters of these fragmented processes.
Google is enhancing Gmail with new organizational labels
For anyone embedded in the Google ecosystem, Gmail is indispensable. The search giant’s email tool has an extraordinarily large userbase, and Google continues to find new ways to make it more useful. The focus of so much of the company’s efforts have been AI-related in recent times, so it is refreshing to see that other options have not been completely abandoned.
With email communication now the default for pretty much everything, it is little wonder that inboxes are chaotic explosions. And it is with a simple change that Google is looking to make it easier to manage your emails with as little effort as possible.

Microsoft adds new screen recording capabilities to Sysinternals ZoomIt
Microsoft’s suite of Sysinternal tools is an interesting collection. While not as exciting – or as frequently updated – as PowerToys, it is home to a number of incredibly useful utilities, especially for power users and system administrators.
But there are also instances of crossover, and the screen recording tool ZoomIt is a perfect example. Although ZoomIt has been merged into the PowerToys utility suite, a standalone version remains available for Sysinternal fans who want to steer clear of PowerToys. In an interesting move, Microsoft has pushed an update to the standalone version of ZoomIt with new features which are not available in PowerToys.

The first Extended Security Update for Windows 10 is here
The end has been nigh for Windows 10 for what feels like an eternity, but Microsoft finally pulled the plug on mainstream support last month. After a confused period of communication and a few niggles, the company has now released the first Extended Security Update for the operating system.
With the release of the KB5068781 update, Microsoft is now only addressing problems with Windows 10. With the ESU program now in operation, no new features should be expected.

One in 44 GenAI prompts risks a data leak
In October, one in every 44 GenAI prompts submitted from enterprise networks posed a high risk of data leakage, impacting 87 percent of organizations that use GenAI regularly.
A study from Check Point Research finds an additional 19 percent of prompts contained potentially sensitive information such as internal communications, customer data, or proprietary code. These risks coincide with an eight percent increase in average daily GenAI usage among corporate users.

Financial sector ups investment in ID verification tech
Banks, fintechs, and crypto platforms are ramping up investment in fraud prevention and identity verification (IDV), positioning it as the next layer of cyber defense, according to a new survey.
The study from Regula shows banks are leading this trend: the share of institutions intending to increase IDV budgets by more than 50 percent is nearly tripling -- from 4.4 percent to 15 percent in just two years.

The AI Paradox: GitLab finds faster coding is slowing teams down
GitLab has published new findings highlighting what it calls the “AI Paradox,” whereby artificial intelligence is speeding up coding but introducing new productivity barriers as a result. The company’s 2025 Global DevSecOps Report, conducted with The Harris Poll, surveyed 3,266 professionals working in software development, IT operations, and security. The results suggest that while teams deploy faster than ever, they are losing time to inefficiencies that AI alone cannot fix.
According to the study, DevSecOps professionals lose about seven hours per week to inefficient processes. The main causes include fragmented toolchains and collaboration gaps between teams.

MX Linux 25 'Infinity' arrives with a cleaner look and easier installation
MX Linux 25 “Infinity” has been released and offers a major update for the Debian-based distribution known for stability and usability. The cooperative project between the antiX and former MEPIS communities offers editions based on Xfce, KDE Plasma, and Fluxbox desktops and is built on Debian 13 “Trixie” with MX’s repositories included.
All core releases now include systemd by default, a shift from the project’s long history with sysVinit. Any users who prefer the older initialization system can still download alternative sysVinit editions. The developers say this change improves compatibility with modern Debian packages and simplifies maintenance going forward.

SomniPods 3 AI-powered earbuds aim to improve sleep quality through monitoring and sound control
Fitnexa has announced SomniPods 3 ultra-light earbuds developed for sleep use. They combine active noise canceling, sleep tracking, and app-based analysis to help users monitor and adjust their sleep patterns.
SomniPods 3 features a dual-microphone hybrid active noise canceling system designed to reduce external noise by up to 42dB in Fitnexa-tested conditions. The feedforward and feedback microphones detect and counter background sounds through reverse sound waves, cutting disturbances from snoring or low-frequency hums.

AiPaper Reader is an AI E Ink device for focused reading
Viwoods has introduced the AiPaper Reader, a 138g Android 16-powered e-reader that adds on-page AI assistance. The compact device lets readers verify terms, translate passages, or summarize figures directly within text. Viwoods thinks this will be of particular use to professional and academic users who read for long stretches or while traveling.
AiPaper Reader keeps answers beside the text rather than diverting users to another app or browser. Its 6.13-inch 300ppi E Ink Carta 1300 display features a low-reflectance layer and adjustable front light for comfortable reading in different environments.

Apple announces iPhone Pocket, a knitted pouch for carrying your mobile
Apple has joined forces with ISSEY MIYAKE to create a new way for iPhone owners to carry and protect their smartphone. The iPhone Pocket is a sash-style 3D-knitted pocket which is available in a rainbow spectrum of colors.
This is not the first time the iPhone-maker has collaborated in this way, and the result this time around is a versatile phone sling that can be worn or carried in a variety of ways. There are two different styles to choose from, but potential buyers may baulk at the price.

Meta is killing off Facebook social plugins including the external Like button
There are few things more iconic online than the Facebook Like button. Found underneath every post on the social media platform, the button has become a handy way for sites to encourage engagement.
But now Meta has announced plans to discontinue two of its Facebook Social Plugins in the early part of next year. Specifically, it is the Facebook Like button that appears on external websites, as well as the Facebook Comment button. This is quite a change for the social media giant to come up with out of the blue, so what is the thinking behind it?

Study debunks viral claim that AI filters out most job applicants
Enhancv has released a new study challenging the long-standing myth that Applicant Tracking Systems (ATS) or AI automatically reject most resumes before a human review. According to its interviews with 25 U.S. recruiters and HR professionals, 92 percent said their systems do not auto-reject resumes based on formatting or content.
Instead, recruiters point to overwhelming application volume and the timing of submissions as the real reasons many candidates never make it as far as the interview stage.

Ookla brings its Speedtest expertise to a handheld diagnostic device
Ookla has unveiled Speedtest Pulse, a new diagnostic device aimed at solving the long-standing “Wi-Fi blame game.” The technology is designed to help ISPs and enterprise IT teams accurately identify whether connectivity issues stem from the network, the router, or the device itself.
Speedtest Pulse is described as a smartphone-based tool that puts two decades of Ookla’s connectivity expertise into the hands of field technicians.
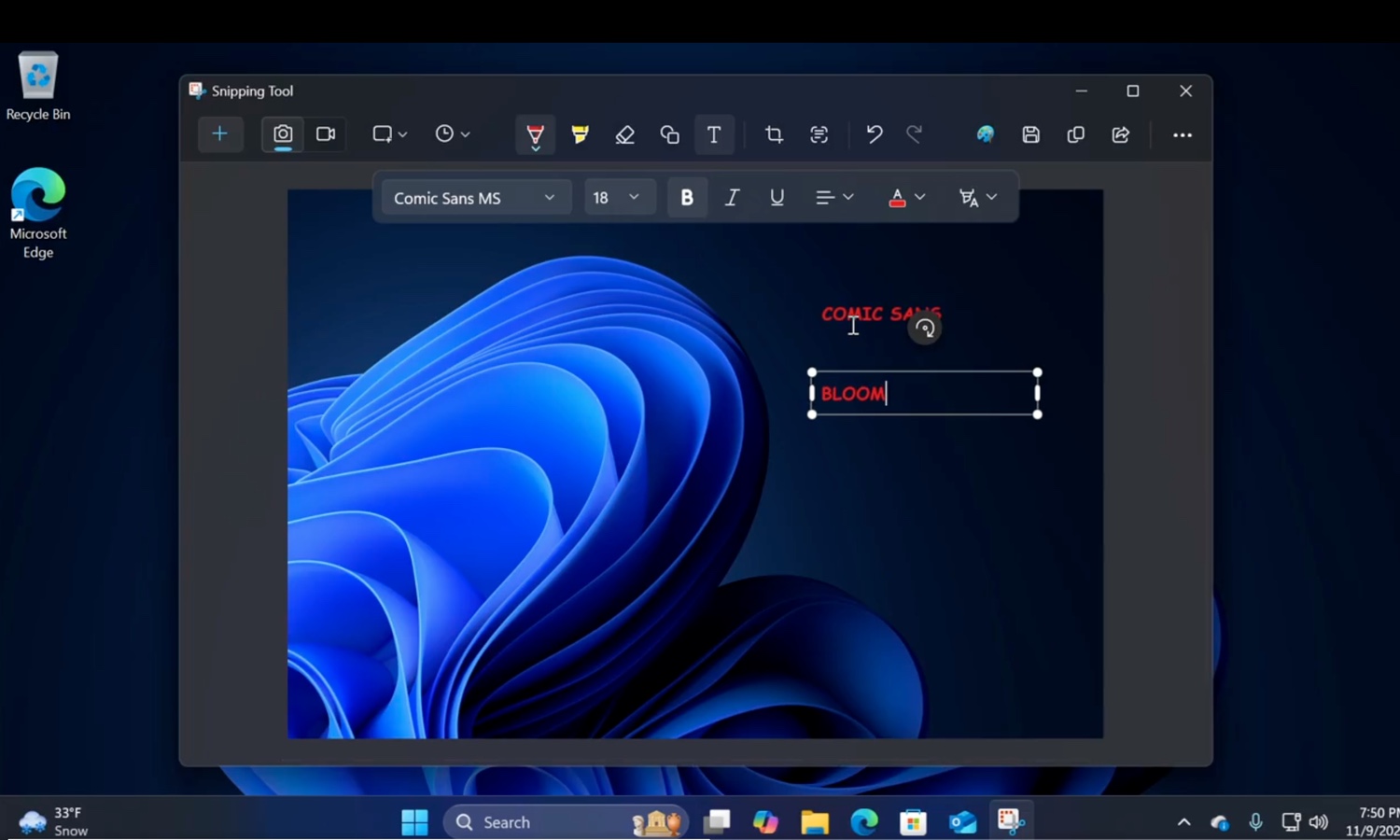
Microsoft is updating Windows 11’s Snipping Tool with option to add text to screenshots
Over the last few years, Microsoft has gradually evolved the Snipping Tool from a simple screen-grabbing tool into something which is much more advanced and sophisticated than anyone could have first imagined.
Having added features such as the ability to create video, grab text from images using OCR, the company is now adding new text options to the app. While not officially available – or even announced – new capabilities have been spotted in the app that show how Microsoft is developing this increasingly essential tool.


