
Phishers cash in on WannaCry attack
The UK's ActionFraud cyber crime reporting center is warning customers of BT’s internet services of a phishing scam claiming to protect against WannaCry-style attacks.
The emails claim that BT has launched preventative measures to protect data on an international scale and try to get recipients to click on a link to a 'security upgrade'.

Data breach at DocuSign leads to massive phishing campaign
E-signature and security firm DocuSign has confirmed a data breach in which attackers gained access to a database containing customer email addresses. The company says that no other data was revealed in the security breach, but it led to a large phishing campaign.
Attackers used the stolen email addresses to spam people with emails containing an infected Microsoft Word document. The company insists that its core service remains secure, but coming in the wake of the WannaCry ransomware attack, people around the world are on high alert.

Word vulnerability, Windows bug, and 'Trump's_Attack_on_Syria' document used in Sednit phishing attack
The Sednit group believed to have been involved in interference with the French election was also responsible for a phishing attack that used President Trump to lure in victims. Security firm ESET analyzed a phishing email with an attachment named Trump's_Attack_on_Syria_English.docx and found that it had the hallmarks of the well-known group.
The document was engineered to infect victims' computers with the Seduploader tool, and it did this by exploiting two vulnerabilities, one in Microsoft Word, and one in Windows. Sednit -- previously known as APT28, Fancy Bear, and Sofacy -- took advantage of a recently discovered Remote Code Execution vulnerability in Word (CVE-2017-0262) as well as a security hole in Windows (CVE-2017-0263) in executing the attack.
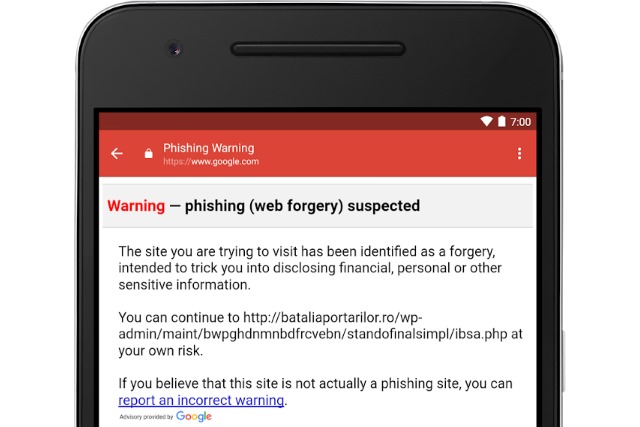
Google adds phishing protection to Gmail app on Android
Gmail users will now be protected from phishing attacks on their Android phones thanks to a new update from Google. The company is rolling out a new security feature similar to that found in the web version of Gmail, warning people when an email contains a suspicious link.
For now, the update is only rolling out to Android users, and Google has not indicated whether it will make its way to iOS in due course or not. The update comes just shortly after a phishing scam emerged in which recipients were encouraged to click on a link to open files purporting to be stored on Google Docs.

Cyber squatters target UK bank domains
Part of the art of making a phishing attack successful is having a domain name that looks sufficiently similar to a legitimate one not to arouse suspicion in the target.
Research by threat intelligence specialist DomainTools has uncovered over 300 registered domains using the names of five of the UK's top high street banks.

Security researchers uncover phishing attack with very high success rate
A new and "very aggressive" airline phishing attack was just spotted, and it's one with such a high success rate that even security experts are baffled. It was spotted by Barracuda, and it says that this new attack has a success rate of 90 percent.
The attack combines impersonation, advanced persistent threats and phishing, giving the attackers long-term stealth access to a myriad corporate networks.

Social media makes phishing attacks easy
People like getting friend requests on social media, and hackers are using that to launch successful phishing campaigns. This is according to a new report released by phishd by MMR InfoSecurity.
After reviewing simulated attack campaigns targeting almost a million users, phishd by MMR InfoSecurity says that social media is the most effective lure to have victims clicking email links.

Half of 2016’s phishing attacks aimed to steal money
Almost half (47.48 percent) of all phishing attacks in 2016 were aimed at stealing victim's money, and the amount of financial phishing attacks increased by 13.14 percent according to a new report.
The study by Kaspersky Lab analyzed attacks registered in 2016 by the company's heuristic detection technologies.

Consumers are starting to get the message on phishing
According to a new report from security awareness training company Wombat Security, people are starting to get the message on phishing.
When asked, 'What is phishing?', 65 percent of those surveyed in the US answered correctly. Ransomware remains a bit of a mystery for many, however, 52 percent were not even able to hazard a guess in response to 'what is ransomware?'

Warning: Chrome, Opera and Safari's auto form fillers make it easy to steal personal data
We're all looking for ways to save time and effort, so it's hardly surprising that some web browsers offer a feature that automatically fills in online forms with commonly requested personal information. While incredibly useful, the feature can also be exploited to extract data a user might not want to share with a particular website.
Chrome, Opera and Safari all offer to save and automatically fill in details such as name, address, phone number, and so on, and users are ordinarily only aware of the data which is obviously filled in on their behalf. But a web developer shows how it is possible -- and very, very easy -- to use hidden fields to secretly gather all of the information saved in an autofill profile.

Watch out for Amazon sellers with New Year phishing scams
This is one of the many times of year that retailers have sales, coinciding neatly with the time of year when many people are feeling the pinch after splashing out on food and presents. But if you're scouring Amazon for great deals, watch out for sellers who are actually using low prices to lure you into a phishing scam.
One seller going by the name of (among others) Sc-Elegance uses "used, like new" tech products as bait, ultimately directing buyers to a fraudulent site to make payments. Security experts are warning shoppers to be on their guard.

Automated phishing boosts profits for hackers
Phishing has proved to be one of the most profitable techniques for hackers. A new report from cyber security company Imperva reveals that the availability of turnkey services is making it even more effective.
Imperva researchers explored the darknet marketplace to estimate the cost of phishing campaigns and to get a clear picture of the hackers' business model. They discovered phishing-as-a-service (PhaaS) campaigns were easy to buy and low cost.

The five most common social engineering attacks
However much technology you throw at protecting your organization's systems the weakest link is still the person sitting in front of the endpoint.
No surprise then that social engineering is increasingly the attacker's weapon of choice for gaining access to sensitive systems. Security rating and risk monitoring company SecurityScorecard has put together an infographic showing the five most common attacks and their impact on enterprises.

New solution aims to stop phishing attacks in their tracks
We know that phishing is on the increase and that attacks are becoming ever more sophisticated.
The Anti-Phishing Working Group (APWG) found more than 460,000 unique phishing sites in the second quarter of 2016 alone, up 61 percent over the previous quarter and almost three times the number observed in the fourth quarter of 2015.

Healthcare staff lack basic cyber security awareness
The consequences of a security breach in the healthcare sector can be severe, yet a new survey reveals that healthcare staff are among the most likely to fall victim to social engineering attacks.
The study from SecurityScorecard exposes vulnerabilities across 700 healthcare organizations including medical treatment facilities, health insurance agencies and healthcare manufacturing companies.