Automated phishing boosts profits for hackers

Phishing has proved to be one of the most profitable techniques for hackers. A new report from cyber security company Imperva reveals that the availability of turnkey services is making it even more effective.
Imperva researchers explored the darknet marketplace to estimate the cost of phishing campaigns and to get a clear picture of the hackers' business model. They discovered phishing-as-a-service (PhaaS) campaigns were easy to buy and low cost.
In addition, they saw that hackers were easily able to hijack compromised webservers for their campaigns, which further lowers the investment needed. Based on the researchers' analysis of costs, PhaaS is about a quarter of the cost and twice as profitable compared to a traditional unmanaged phishing campaign, which is skill and labor intensive. Unfortunately, lowering the costs and technology barriers associated with phishing is likely to lead to an increase in phishing campaigns, and see more people falling victim to them.
"The combination of PhaaS and compromised web servers has significantly lowered the monetary, technological and time investment needed to conduct a successful phishing campaign", says Amichai Shulman, co-founder and CTO of Imperva. "It’s no longer feasible for enterprises to use the client-side approach of endpoint software to fight phishing attempts because people continue to click nefarious links in email. One way to slow the attacks is to choke off easy access to compromised servers, which would make the phishing business model more expensive and lower profitability. Web applications are ubiquitous today, and web application security needs to be widely adopted to stem the growth of phishing and protect valuable data and applications".
Imperva's researchers were also able to uncover a surprising amount of data on both the victims and the hackers' social engineering techniques. Mornings are most dangerous it seems, with most people likely to take the email phishing bait during the hours of 9am to noon while at work and when they were busy writing and replying to emails. In addition, victims are more likely to enter their username and password to open an email attachment -- an Adobe PDF file in the case of the research -- than to click on a URL in the email and blindly log in.
You can find out more about the report on the Imperva blog and there's a summary of the findings as an infographic below.
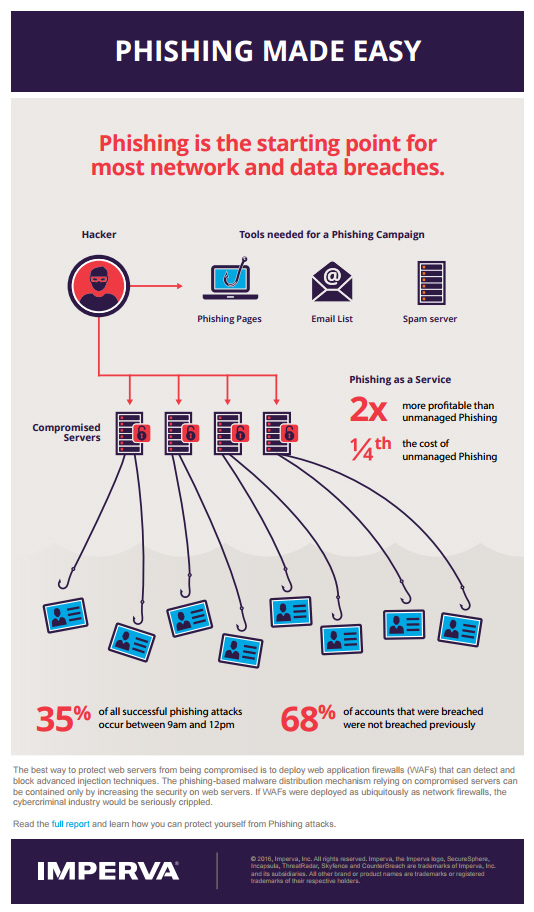
Image Credit: Maksim Kabakou / Shutterstock