The five most common social engineering attacks

However much technology you throw at protecting your organization's systems the weakest link is still the person sitting in front of the endpoint.
No surprise then that social engineering is increasingly the attacker's weapon of choice for gaining access to sensitive systems. Security rating and risk monitoring company SecurityScorecard has put together an infographic showing the five most common attacks and their impact on enterprises.
The attacks identified are 'pretexting' -- assuming another identity to obtain sensitive information, 'tailgating' -- following a person with legitimate access into a secure location, 'quid pro quo' -- offering some incentive in exchange for information, 'baiting' -- leaving malware infected devices like USB sticks lying around, and our old friend 'phishing' -- copying the appearance of legitimate communications to fool recipients.
Among other things highlighted are that financial and technology companies are among the most targeted by phishing attacks. Also vulnerability to attacks increases as organizations get larger.
You can find out more, including tips to avoid falling victim to phishing, on the SecurityScorecard blog and the full graphic is reproduced below.
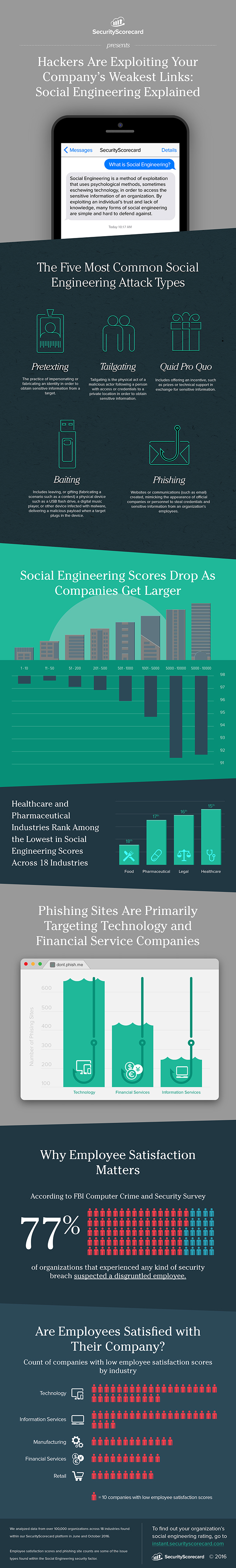
Photo Credit: Lasse Kristensen/Shutterstock