
Enterprises overwhelmed by endpoint alerts
Organizations receive an average of more than 600 endpoint alerts in a typical week according to a new report. These represent a severe drain on an organization's financial resources and IT security personnel and the cost can average $1.4 million annually.
The study by endpoint security company Absolute and the Ponemon Institute reveals that, of all alerts, 45 percent (277 alerts) are considered reliable and an average of 115 are investigated. An average of 61 percent or 369 of these alerts involve malware infections.

Malicious antivirus apps prey on ransomware fears
Recent weeks have seen a rise in fake WannaCry protectors on mobile app stores, even though this particular infection doesn't target mobile devices.
But using the fear of high profile infections to get users to download potentially unwanted programs or malware is nothing new according to threat management company RiskIQ. Using its mobile database, hundreds of examples of apps that claim to help defend mobile phones were found, instead, to be preying on unsuspecting users by pushing adware, trojans, and other malware.

People in the US are less savvy about cyber security than people in the UK
A new report suggests that people in the UK are more aware of the terminology surrounding cyber security, and are less likely to fall victim to hacking and identity theft. Wombat Security Technologies' 2017 edition of its User Risk Report reveals a stark difference in cyber knowledge on either side of the Atlantic.
The report is based on a survey carried out last month into knowledge of, and attitudes to, cyber security topics and best practices. While the report shows that the UK is generally more cyber security savvy, the US is shown to fare better when it comes to passwords and backing up data.

Collaboration cloud services lead to a rise in data violations
Almost 10 percent of data loss prevention (DLP) violations come from collaboration services according to a new report.
The study from cloud security company Netskope shows that as cloud services like HipChat and Slack have increased in popularity enterprises need to put policies in place to protect the information that’s shared.

Do you know where your cloud data is stored?
IT security heads may be drastically underestimating the size of their organization’s cloud presence, leading to potentially huge security risk, a leading expert has warned.
Speaking to ITProPortal at the recent InfoSecurity 2017 event in London, Darren Thomson, EMEA CTO at Symantec, said that it was "a massive, massive concern" that many CISOs and CIOs were unable to accurately say how big their company’s cloud presence was.

Microsoft integrates with Zimperium to guard against zero-day mobile threats
Cyber attacks aren't limited to desktop systems, mobile endpoints are equally at risk and for enterprises this is something else that needs protection.
Mobile threat defense specialist Zimperium is announcing an integration with Microsoft Enterprise Mobility + Security to integrate its product with the Microsoft Intune mobile device and application management product.
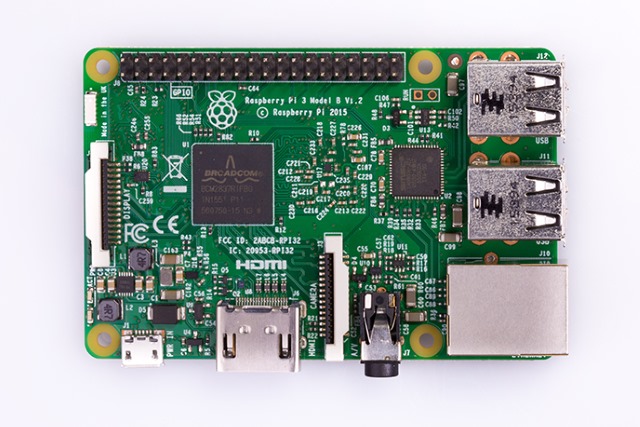
Raspberry Pi devices transformed into cryptocurrency miners by Linux malware
The words "Linux" and "malware" don’t tend to belong in the same sentence, but a new strain called Linux.MulDrop.14 is infecting Raspberry Pi devices. Infected machines are used to mine cryptocurrency for the malware's author, and it take advantage of poor security to generate money from nothing.
The good news is that the malware is fairly simple, and its spread is dependent on the laziness of Pi owners.

Google makes the mobile internet safer with reCAPTCHA Android API
On the tenth anniversary of the arrival of reCAPTCHA, Google announces the first reCAPTCHA Android API as part of Google Play Services. The API makes it easier for reCAPTCHA to differentiate between humans and bots.
Just as reCAPTCHA has evolved over the years into Invisible reCAPTCHA, the aim with reCAPTCHA Android API is to cut down on spam and abuse in as unintrusive a way as possible.

Remote workers may put businesses at risk
Freelance workers have proven to be an extremely useful resource for many small companies in recent years, allowing for specialized expertise to be recruited when needed the most.
However, a new research report from security firm Tripwire has found that using such workers, particularly for IT projects, might actually be putting your business in danger of a major security breach.
Patch management is a major issue for enterprises
We already know that outdated systems are a major problem for enterprises as they increase the risk of data breaches.
But a new study by enterprise security specialist Bromium reveals that the act of patching is a big problem for many companies too.

NSA cites privacy concerns for u-turn over revealing the number of Americans it spies on
Section 702 of the FISA Amendments Act -- the legislation used to permit the NSA to conduct online surveillance -- is due to expire at the end of the year. We have already seen a number of the big names from the world of technology calling for a number of changes during reform.
As part of the reform, officials had promised that they would reveal broad details about the number of American citizens about whom information has been, and is, collected. This is no longer the case. The Director of National Intelligence has performed a u-turn on the promise.

Botnet activity rises by 69 percent
PhishMe has released its latest malware trends report for Q1 2017, concluding that botnets are on the rise, it is unusually quiet on the ransomware front, and cyber criminals are tapping into international trends.
The report, entitled 2017 Q1 Malware Review, is based on an analysis of 749 sets of phishing emails delivering nearly 10,000 unique malware samples supported by over 14,000 online resources.

UK businesses prepare for ransomware attacks by buying Bitcoin
British businesses are ready to pay as much as £136,000 to get their files back after a ransomware attack. This is according to a new report by Citrix and One Poll, based on a poll of 500 IT decision makers at UK companies with 250 or more employees.
The report says these new figures are four times higher than 12 months ago, highlighting the growth of ransomware risk among businesses on the Island.

EventTracker launches improved threat intelligence platform
The rapidly changing world of cyber security means that companies need to be able to respond quickly to threats.
Security information management company EventTracker is launching a new version of its SIEM platform, which provides advanced features to combat modern ransomware and mutating malware, along with expanded threat intelligence.

You can create a hacking tool for just $20
If you have $20 to spare and some "basic programming knowledge," you can create a powerful hacking tool that can collect huge amounts of user credentials, easily. The best part about it is that you don’t even need to use any malware or viruses -- everything can be clean as a whistle.
The news was revealed by security experts Kaspersky Lab, which was able to create such a device using a Raspberry-Pi microcomputer that was then configured as an Ethernet adapter.