
HandBrake for Mac server compromise means downloaders have 50-50 chance of Proton RAT malware infection
Anyone who downloaded the Mac video transcoder HandBrake in the last few days stands a 50 percent change of being infected with a Trojan. The download for version 1.0.7 of HandBrake was infected after the mirror download server was compromised.
The Trojan allows for an attacker to remotely access an infected computer, and a malware-laced version of the app was made available for download between May 2 and May 6. If you downloaded the app in this window, you're advised to check the SHA1/256 sum, and if you have gone as far as installing the software, there are steps to take to determine if you're infected and remove the malware if you are.

More Vault 7 leaks from WikiLeaks: Archimedes is the CIA's man-in-the-middle hacking tool
WikiLeaks continues to release revealing documents from its Vault 7 cache. This time around the organization introduces us to a CIA tool called Archimedes -- previously known as Fulcrum.
As before, there is little to confirm whether or not the tool is still in active use -- or, indeed, if it has actually ever been used -- but the documentation shows how it can be installed on a LAN to perform a man-in-the-middle attack.

Emmanuel Macron hit by EMLEAKS email hack ahead of French election head-to-head with Le Pen
Left-wing French presidential hopeful Emmanuel Macron has been hit by a "massive and coordinated" hack attack just before voters go to the polls. A 9GB cache of emails and photos was dumped as a torrent on Pastebin by a leaker by the name of EMLEAKS. The torrent was initially hosted on Archive.org.
It was quickly pulled offline, but not before it had spread far and wide on social media. Released just before midnight on Friday night, the leak was timed to prevent Macron from responding. French election rules forbid candidates from engaging in any form of campaigning immediately before polls open.

How to lock down Windows 10 Home/Pro like Windows 10 S
Microsoft this week introduced a new version of Windows 10 aimed primarily at users in education, and designed as an alternative to Google’s Chrome OS.
The main difference between Windows 10 S, and Windows 10 Home/Pro is it only runs apps from the Windows Store. You can’t install programs from elsewhere, and this includes Chrome. This mean users can only install Microsoft-verified software which, the software giant says, will result in better security and superior performance. You don’t need to buy or install Windows 10 S to get this feature though, you can simply lock down an existing version of Windows 10.

One in four banks struggle to identify customers online
Around a quarter of banks are struggling to identify their customers when delivering digital and online banking services, according to Kaspersky Lab.
The latest findings from its Financial Institutions Security Risks survey show that 38 percent of financial institutions surveyed confirm that balancing prevention techniques and customer convenience is one of their specific concerns.

'Fatboy' ransomware uses a location-based charging model
A new ransomware-as-a-service product named 'Fatboy' has been advertised on Russian language forums. What makes it different is the way it uses a sliding scale to charge its victims.
Threat intelligence company Recorded Future has revealed that Fatboy uses the Economist's Big Mac Index -- designed to explain exchange rates -- to ensure victims in areas with a higher cost of living will be charged more to decrypt their data.

DDoS attacks could cost enterprises over $2.5 million in revenue
A new report from information services specialist Neustar looks at the frequency and cost of DDoS attacks and what is being done to counter the threat.
In terms of revenue loss, three percent of organizations report average revenue loss of at least $250,000 per hour, with 51 percent taking at least three hours to detect an attack and 40 percent taking at least three hours to respond, that means an attack could cost over $2.5 million.
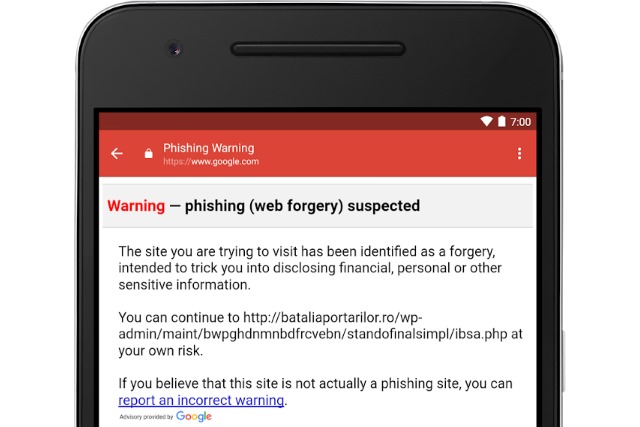
Google adds phishing protection to Gmail app on Android
Gmail users will now be protected from phishing attacks on their Android phones thanks to a new update from Google. The company is rolling out a new security feature similar to that found in the web version of Gmail, warning people when an email contains a suspicious link.
For now, the update is only rolling out to Android users, and Google has not indicated whether it will make its way to iOS in due course or not. The update comes just shortly after a phishing scam emerged in which recipients were encouraged to click on a link to open files purporting to be stored on Google Docs.

Consumer tips for World Password Day
Almost everything has its own day these days and May 4th is -- along with all the Star Wars puns -- World Password Day.
Cyber security firm Kaspersky Lab is keen to help people avoid common password problems and is calling for a standardization of password criteria.

Cyber squatters target UK bank domains
Part of the art of making a phishing attack successful is having a domain name that looks sufficiently similar to a legitimate one not to arouse suspicion in the target.
Research by threat intelligence specialist DomainTools has uncovered over 300 registered domains using the names of five of the UK's top high street banks.

Healthcare breaches down following 2016 peak
Healthcare data breaches hit an all-time high in 2016 resulting in the records of almost 16.6 million Americans being exposed as a result of hacks, lost or stolen devices, and unauthorized disclosure.
But the latest Healthcare Breach Report from data protection company Bitglass shows a sharp decline in breaches over the first quarter of 2017.

Assembly line robots vulnerable to hacking
Industrial robots make many of the things that we use in our everyday lives, from cars to domestic appliances.
If the world isn't to descend into chaos therefore, it's imperative that robots follow their programming. But a new report from the TrendLabs research arm of cyber security company Trend Micro reveals just how easily industrial robots can be hacked.

Is it time to replace the VPN?
It’s time to replace the traditional VPN and regain trust of your endpoints with a more secure and easier approach to remote access. VPNs have typically been the go-to solution for access to internal applications, with one-third of access requests to corporate networks coming from outside the firewall.
However, VPNs come with security drawbacks, including the increased risk of unauthorized remote access to sensitive data. Typically, they grant access at the network level, meaning every user with VPN rights can access the same applications that any other user can, which is a risky practice.
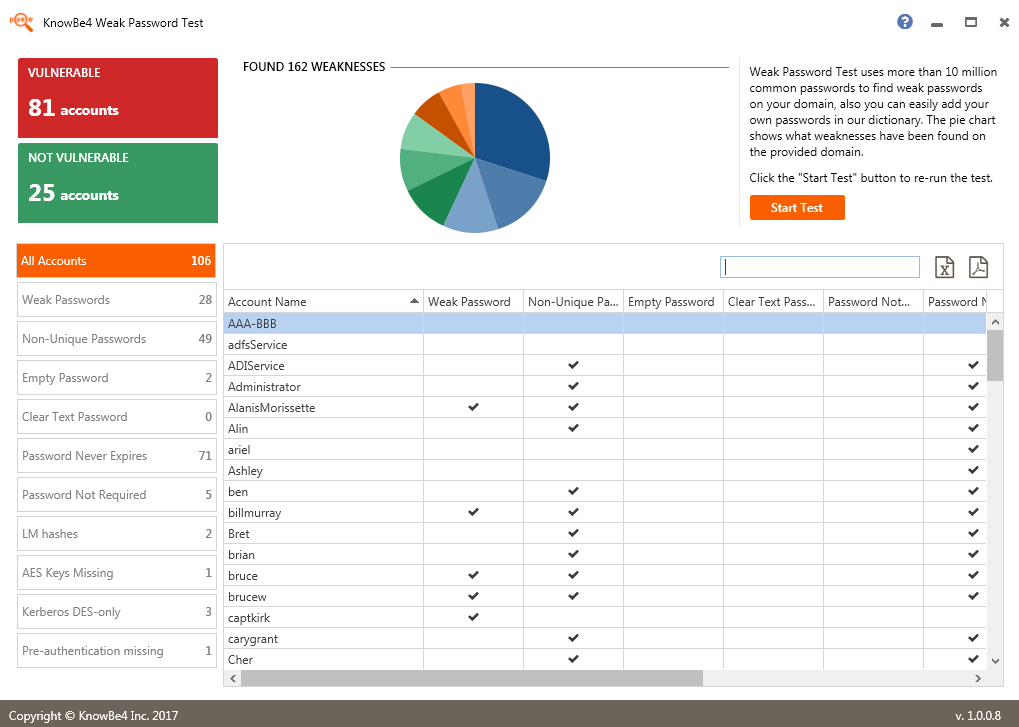
Free tool allows Active Directory users to test for weak passwords
While security is still heavily reliant on passwords, they represent a target for hackers and weak or reused choices offer an easy way into systems.
Security awareness training company KnowBe4 is releasing a free Weak Password Test (WPT) tool for organizations that use Active Directory, allowing them to check for multiple types of threats related to weak passwords.

New integration delivers improved security analytics for mainframe users
Many enterprises still rely on logs and data from a range of different security products to get a picture of user behavior, particularly where legacy mainframe systems are involved.
A collaboration between data analytics company Syncsort and application audit specialist Compuware is aimed at improving an organization's ability to detect threats against critical mainframe data, correlate them with related information and events and satisfy compliance requirements.