
UK's Trident nuclear weapons could be hit by cyberattacks
The UK's former defense secretary Des Browne has issued a stark warning that the country's nuclear weapons could be vulnerable to cyberattacks. The Trident program is already a highly-divisive subject, and Browne is seeking assurance from the Prime Minister that it is secured against attacks from hostile states such as China and Russia.
He has called upon the government to perform an end-to-end assessment of the system. The US had previously warned that it could not be confident that its own defenses and those of its allies would be capable of withstanding a cyberattack from a "sophisticated and well-resourced opponent".

ProtonMail: banning encryption won't stop terrorism
In the panic that followed the attacks on Paris by ISIS there have been calls for various measures to be put in place to stop similar atrocities happening in the future. As well as calls for an increase in online surveillance, politicians have also suggested that encryption should be weakened or banned entirely.
Secure email service ProtonMail found itself the subject of unwanted attention when it transpired that ISIS recommended using it to evade detection. The company has remained silent about the post-Paris backlash; until now.

Europe should set up its own cybersecurity agency
Europe is being urged to set up its own international cybersecurity agency to tackle the growing threat posed by cyberattacks. Jose Luiz Gilperez, security chief at Telefonica, said that cyberthreats have developed in recent years to pose just as significant a danger as physical threats.
Of particular concern is a fundamental change in the types of individuals perpetrating cyberattacks. While the stereotypical image of the lone hacker may have held true in the past, cyberattacks are now being carried out by hacking collectives, gangs of organized criminals or even national governments. Gilperez stressed that in order to counter this new threat, cybersecurity must become "a matter of business, and a matter of states".

Google can remotely reset your Android passcode
A common recommendation for securing a mobile device is to set up a passcode. Having a PIN or password will make it harder for a third-party to have access to personal information, which lowers the chances of data theft or loss but also incrimination or blackmail.
But, when that third-party is a government agency looking to retrieve data from someone's Android device, it might be easier than you think to get in. On top of all the resources they have at their disposal, government agencies can also turn to Google to have the passcode remotely reset.
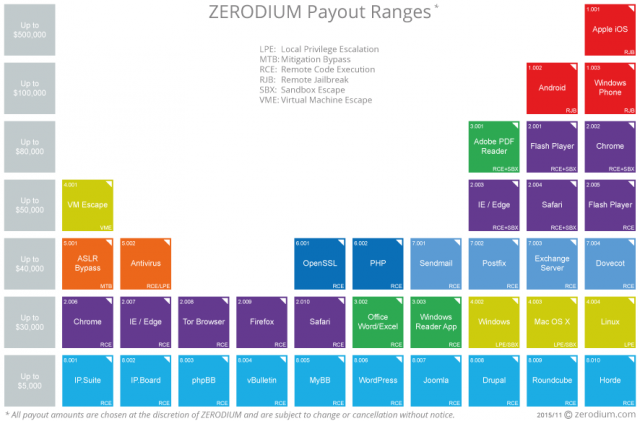
Zerodium reveals price list for zero-day exploits
Exploit acquisition platform Zerodium has just published a price chart for different classes of digital intrusion techniques and software targets that it buys from hackers and later resells in a subscription service to its clients.
This is important as it is the first time someone has publically put a price tag on hacking.

Anonymous releases guides to help anyone hack Islamic State
Hacktivist group Anonymous, which has recently declared "war" on ISIS, has released a guide on how to find and take out ISIS-related websites and social media accounts.
The group posted three different guides, to be used within #OpParis, the online campaign against the Middle-Eastern militants.

69 percent of users would bypass security controls to win a big deal
When faced with the chance of clinching a major deal people are willing to throw security controls out of the window.
This is according to research by contextual security company Balabit which asked over 380 European IT executives, CIOs, CISOs, auditors and other IT professionals about their thoughts on IT security and business flexibility.

Siri poses privacy and security risks for iPhone users
Digital assistants such as Siri are billed as great time-savers, and there's no denying that Apple's voice-activated feature can be a real help. But security experts at Trend Micro warn that it also poses a serious privacy risk for iPhone owners.
Even if your iPhone is protected with a PIN or passcode, it could still be possible for someone else to use Siri to learn personal information about not just you, but your relations and other contacts, as well as details about your schedule. Described by Trend Micro as a 'flaw', Siri actually acts as a backdoor that enables anyone with physical access to your phone to bypass security features.

Government organizations are major target of Q3 cyber attacks
PandaLabs, the malware research arm of Panda Security has released its latest quarterly security report revealing a wave of cyberattacks where the security and information of various governments has been compromised.
The company has detected a growing interest between countries in compromising the security and information of different governments. With that in mind, one of the most important attacks during this period was against the Hacking Team, which controls a multitude of cyberespionage and cyberattack tools for various governments around the world.

Microsoft announces its Cyber Defense Operations Center for a mobile-first, cloud-first world
Microsoft invests more than a $1 billion every year on security, showing the company is taking one of biggest digital problems of today quite seriously. The information was unveiled on the Microsoft blog, where the company’s Chief Information Security Officer, Bret Arsenault, reported on CEO Satya Nadella’s keynote in Washington, D.C.
According to the blog post, not only does Microsoft invest large sums of money into security, it is also announcing the Cyber Defense Operations Center, a new state-of-the-art facility which will bring together security response experts from across the company to help protect, detect and respond to threats in real-time.

Almost a third of consumers feel unsafe shopping on mobile apps
The use of mobile devices for shopping is increasingly becoming the norm. But, as we approach the year's peak shopping season, a new survey reveals that many consumers are worried about shopping with their mobile devices and providing credit card information to mobile apps.
The study from Blancco Technology Group of more than 1,400 consumers in the United States, Canada, UK and Australia, finds that 28 percent of consumers feel completely unsafe shopping from a mobile device, while two out of 10 are hesitant to link credit cards to mobile apps.

Most smartphone owners fear hackers, thieves and government control
Edward Snowden's NSA and GCHQ revelations seem to be unending. One of his more recent disclosures was that UK intelligence agencies had the ability hack and remotely control any smartphone.
A survey by Broadband Genie shows that smartphone owners are more than a little concerned about this, with more than half (55 percent) saying the possibility of remote control worries them. A similar number (53 percent) express concern that these surveillance and control powers are open to abuse, and nearly a quarter (24 percent) feel they are a breach of human rights.

How to enable two-factor authentication on your Amazon account
One of the best ways to protect your online accounts is by using two-factor authentication (2FA) wherever possible. With this activated, logging into a site requires the use of both a password, and a code sent to your mobile phone. Since most of us have our smartphones within easy reach 24/7, this isn’t as much of a chore as it could be, and it certainly delivers a useful layer of additional security.
Not all sites offer this feature however, Amazon being a prime example (pun intended). However, from today that all changes, as the retail giant has quietly introduced the option to set up two-factor authentication on your Amazon account. This means that even if your password falls into the wrong hands, no one will be able to get into your account and go shopping at your expense. This is what you need to do:

Top UK companies offered free cyber health check
The UK's 350 largest businesses are being urged by the government to take part in a free Cyber Health Check to help them understand and improve their level of cyber security.
Companies taking part will receive a confidential, tailored report enabling them to understand boardroom trends, compare themselves to their peers and address any weaknesses identified. The health check also generates aggregated data showing how well the FTSE 350 companies are performing.

Trustwave launches new tools to protect SMBs from cybercrime
It isn't just big organizations that are at risk from cybercrime. Smaller businesses are vulnerable too, figures from the Small Business Committee suggest 71 percent of cyber attacks target businesses with under 100 employees, and they're less able to afford sophisticated tools to protect themselves.
To address this security company Trustwave is launching a new set of integrated security tools aimed at small and medium enterprises.