GRE tunneling: Keeping human traffic unaffected during DDoS attacks

Picture a standard subway ride during rush hour. The car, of course, is crammed full. Some of those subway riders are pleasant commuters, and some are subway villains like pickpockets and purse-snatchers. Now imagine someone has invented a private subway that quickly and efficiently connects you and other pleasant commuters to the subway station in your neighborhood. You don’t have to deal with slowdowns, unexpected stops, or any of the risks associated with being lumped in with the aforementioned subway villains.
Now stop imagining, because someone has invented such a blissful sort of system. It’s just that instead of being a form of transportation it’s a method of directing legitimate human traffic to a website while it’s being protected from a DDoS attack. Not the best news for your commute, but great news for your website.
The DDoS Details
As large and complicated as DDoS attacks can get these days -- and that would be very large and very complicated indeed -- at its core, a DDoS attack is a method of rendering a website or other online resource unavailable to its legitimate users by overwhelming it with malicious traffic.
Being targeted by a DDoS attack can be incredibly costly. An unmitigated attack can cost a company $40,000 per hour, and that’s not even considering the other consequences of a DDoS attack. (Hardware damage, software damage, and theft of intellectual property, confidential data and consumer information, to name a few.)
However, one of the most devastating consequences of a DDoS attack for many businesses is the loss of consumer trust or loyalty. When legitimate users are impacted by a DDoS attack, those users may be distrusting enough to abandon your website or business altogether.
After all, if a website isn’t protected against DDoS attacks, it isn’t protected against DDoS-related intrusions that can steal user information, including financial information. Additionally, this is the age where a competing website is just a click away. Loyalty has become easy to lose.
So how do you keep your users from being impacted by a DDoS attack?
A GREat Method
The general solution is obvious: keep your users from being impacted by a DDoS attack by keeping your website from being impacted by one. Yes, high-quality professional DDoS protection of any sort will go a long way in protecting your users. However, there are specific methods of ensuring an uninterrupted website experience, and one of the best is GRE tunneling.
GRE stands for Generic Routing Encapsulation. GRE is what’s called a tunneling protocol, and, as DDoS protection service provider Imperva Incapsula explains in this blog post, it is used to establish direct and private point-to-point links between network nodes. These private point-to-point links are the so-called "tunnels".
In DDoS protection, GRE is used to protect all elements of critical infrastructure. This can be an organization’s website, email, FTP and other online communications. GRE is capable of doing so because it can transmit packets of all sorts, quickly sending them directly to where they need to go.
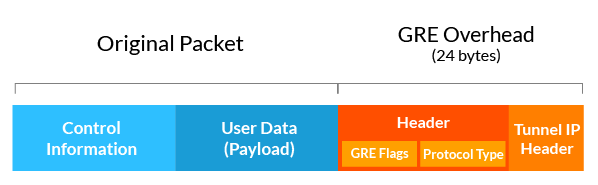
Example of GRE encapsulation (Source: Incapsula)
Border Gateway Patrol (BGP): Traffic Control
DDoS mitigation that uses GRE tunneling is often combined with BGP routing. BGP is the internet protocol that dictates how routing information is transferred between all major internet service providers.
When a website or other internet-connected resource is targeted by a DDoS attack, it sends up a BGP announcement which immediately directs all traffic -- legitimate and malicious -- to a scrubbing server that can inspect traffic at a granular level, which enables it to separate legitimate traffic from malicious traffic.
Malicious traffic is scrubbed and never even touches the website (or network, or server, etc.) while legitimate traffic is allowed through via GRE tunneling, with users never experiencing an interruption of any sort.
Infrastructure DDoS Protection
This form of DDoS protection is most critical for businesses or websites that require 100 percent uptime, like online banking, Forex and other trading companies, online gaming companies, and SaaS. It’s also critical for businesses or websites in highly competitive industries. However, this quality of protection is also available for smaller websites or companies, it simply uses a protected IP address instead of BGP routing.
Essentially, there’s no reason to let your legitimate users struggle to get through on a subway would-be muggers when it’s entirely possible to filter out all that bad traffic during a DDoS attack. A GRE tunnel is better for users, and therefore better for your website.
 Debbie Fletcher is an enthusiastic, experienced writer who has written for a range of different magazines and news publications over the years. Graduating from City University London specializing in English Literature, Debbie's passion for writing has since grown. She loves anything and everything technology, and exploring different cultures across the world. She's currently looking towards starting her Masters in Comparative Literature in the next few years.
Debbie Fletcher is an enthusiastic, experienced writer who has written for a range of different magazines and news publications over the years. Graduating from City University London specializing in English Literature, Debbie's passion for writing has since grown. She loves anything and everything technology, and exploring different cultures across the world. She's currently looking towards starting her Masters in Comparative Literature in the next few years.
Photo Credit: Creativa Images/Shutterstock
