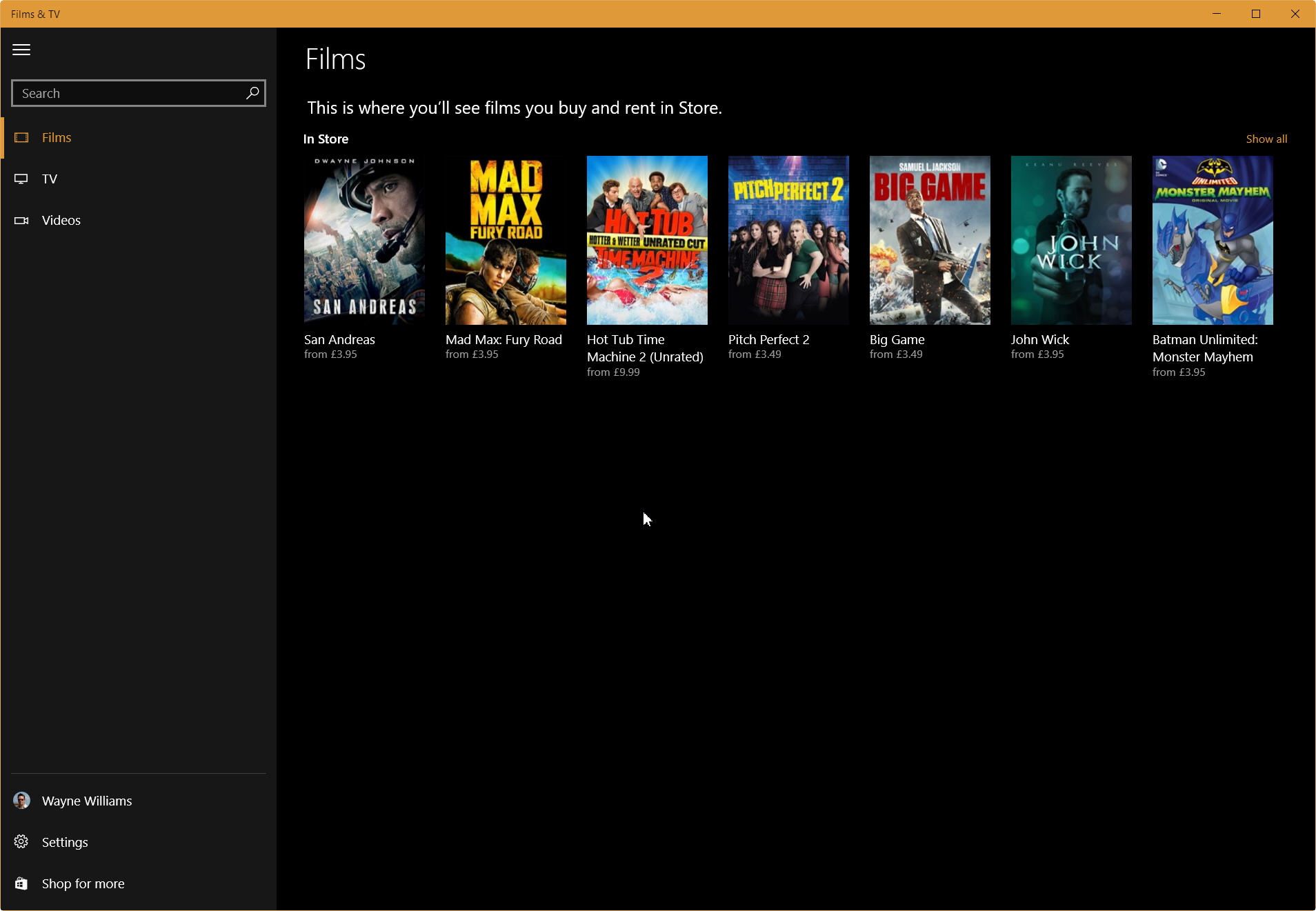
How to enable the Dark Mode in Windows 10's Films & TV app
Windows 10 is still very much a work in progress, as are the apps that come as part of it. The November Update (aka Theshold 2) introduced some cosmetic changes throughout, and there have been other changes made in the many other updates.
The Films & TV app recently gained a new Dark Mode which improves things greatly, but it’s disabled by default. Here’s how to turn it on.

Will 2016 be the year of Windows 10 in the enterprise? [Q&A]
Businesses are notoriously reluctant to make the leap to a new operating system. But by the start of 2016 Windows 10 will have been around for six months, so can we expect next year to be the start of its taking off in the enterprise?
We spoke to Deepak Kumar, Founder and CTO of configuration management specialist Adaptiva to get his views on the march of Windows 10 and more.

Most consumers like the idea of a single-brand ecosystem
A new Xerox report, The State of Customer Service 2015, reveals that more than half (51 percent) of consumers are comfortable with the idea of buying into a single brand ecosystem for all their technology, communications and media needs.
By 2025, 37 percent believe a single supplier will manage their home.

Apple Music declares war on streaming music rivals with new Taylor Swift exclusivity deal
Back in June, if you recall, Taylor Swift had penned a letter to Apple regrading what she perceived as unfair practices with its music service. She was successful in convincing the company to reverse course on paying royalties during the service's free period. Unfortunately, the end result was her wildly popular 1989 album becoming an Apple Music exclusive for streaming. Shortly after, I shared some of my thoughts regarding the state of the streaming music landscape, where I stated that exclusivity could be the demise of all-you-can-eat streaming, and might increase piracy too.
Today, Swift announces that she is once again making new content -- The 1989 World Tour LIVE -- an Apple Music exclusive. In other words, if you are a subscriber to an alternative service like Spotify or Groove Music, you will not be able to hear or see it. While this is arguably a wise business decision for Apple, it is a poor situation for both streaming music consumers and Taylor Swift fans alike. Will this help Apple, or simply hurt the streaming music business as a whole?

Dating app Tinder teams up with the NHS to promote organ donation
Tinder has long-concerned itself with affairs of the heart, but through the final couple of weeks of 2015 the dating app is switching its attention to other organs. Teaming up with NHS Blood and Transplant, Tinder is looking to raise awareness of organ donation.
The campaign aims to highlight to 18-35 year olds the importance of organ donation, and the challenging wait for a matching organ. A number of celebrities are getting involved, changing their profile pictures to a 'The Wait' logo. When users swipe right they will be invited to sign up on the NHS Organ Donor Register.

2016 set to be the year of malware targeting Macs and iOS
Security has long been an issue for Windows users. The sheer number of devices running Microsoft's operating system makes it a prime target for malware and virus attacks. More recently, Apple's computers have increased in popularity and security firm FireEye says that the company will find itself in the crosshairs in 2016.
It's not just Macs and MacBooks that are predicted to become more frequent targets, iOS is also expected to come under attack. FireEye warns that weaknesses have been found in Apple's walled garden, and this could spell danger for users. Symantec is issuing similar warnings, citing Apple's ever-growing user base as the reason.

Alexa app gets new alarm tones and ratings for Skills
Amazon Echo continues to learn new tricks, with music, home automation and much more. Some of the most popular things are called "skills", which are written by third-party programmers. There's also alarms and timers, which can wake you up or tell you when your food is done cooking.
Skills are important, as they allow Alexa to do more all the time. You can find them by opening the app and clicking the menu and then tapping on Skills. To review you will simply need to scroll down after clicking a particular one. From there you can read existing reviews and write your own.

Apple spams users to promote iPhone 6s
Microsoft managed to irritate a lot of people with its heavy-handed pushing of Windows 10, and now Apple has taken a leaf out of the company's book. December may be the time when many people think about getting a new phone -- and Apple is likely to fare very well out of upgrades -- but some iPhone owners have been upset by the appearance of spam in the App Store.
We're not talking about a mass mail-out inviting people to upgrade to the latest iPhone, but ugly, unsolicited popup ads used to push Apple's mobile. Describing the iPhone 6s as 'ridiculously powerful' the ads have been seen by those running iOS 9.1 and 9.2. It's something that could be dismissed, but spamming is unchartered waters for Apple.

Microsoft is in an apologetic mood right now -- what next? 'Sorry for Windows 10'?
Sorry may be the hardest word, but it seems to be tripping off Microsoft's tongue quite freely at the moment. Maybe it's the holiday season making the company look at itself, but we've had two apologies in recent days -- first, a semi-apology for stealing OneDrive storage from people, and now it's sorry about the Surface Book and Surface Pro 4.
Recognizing that many people's experiences with the latest addition to the Surface range has been "less-than-perfect", Microsoft's Josh_F has issued an apology on behalf of the company. Thanksgiving may be little more than a memory now, but Microsoft is thankful for the "open and candid feedback" (or bitching and complaining) about the latest Surface devices. With Microsoft in an apologetic mood, what else could it say sorry for?

Sarah Koenig's podcast comes to Sonos, this time featuring the story of Bowe Bergdahl
Sonos, the whole home audio system, is one the darlings of today's tech world, though it doesn't come at a cheap price. However, the device can pump out high-quality home audio throughout your dwelling and its offerings for content keep getting better.
Season two of Serial has just debuted and this season follows the story of Bowe Bergdahl, who people have mixed opinions of. If you aren't familiar with the story, Bergdahl was stationed in Afghanistan and left his post for, what he claims, was seeking help from superiors due to a lack of leadership in his platoon. There are many caveats and nuances to this tale, and listeners will form their own opinions about the events of that day.

Ford plans to make 40 percent of its cars electric by 2020
The green revolution has hit the auto industry and it has become time to adapt or move on. The company started by Henry Ford has always been near the front in innovation, especially under Alan Mulally. We've seen Ford Sync evolve into the platform it now is and the introduction of electric vehicles.
Now the company is laying out its plans for the next few years and a lot of that involves energy savings. The environment is in trouble and fossil fuels are part to blame.

Microsoft OneDrive is making it rain gigabytes -- here's how to score free cloud storage
Microsoft is doing some great things lately. Between Windows 10, Xbox One and its embrace of open source, you would think the company would be put on a pedestal by its users. Unfortunately, the company acted more like Scrooge than Santa Claus when it announced it was taking away cloud storage capacity from all of its users citing abuse by a few. Not cool.
Today, however, Microsoft is righting this wrong -- at least partially. While unlimited storage is still dead and buried, it is now possible to prevent the decrease from 15GB to 5GB. Shockingly, you can even keep your 15GB camera roll bonus too. How do you achieve this awesomeness? Just use the special link below.

The struggle to keep up with private cloud workload demands
Organizations are struggling with the ability to deliver infrastructure to end users to enable the demands of a DevOps environment.
Those are the results of a new global survey conducted by Qualisystems, provider of private/hybrid cloud orchestration software for DevOps and cloud sandboxing.

Data security is key for customer retention
Nearly two-thirds (64 percent) of consumers worldwide say they are unlikely to shop or do business again with a company that had experienced a breach where financial information was stolen, and almost half (49 percent) had the same opinion when it came to data breaches where personal information was stolen.
This is according to a recent global survey by Gemalto, titled Broken Trust: 'Tis the Season to Be Wary, which surveyed 5,750 consumers in Australia, Brazil, France, Germany, Japan, United Kingdom and United States.
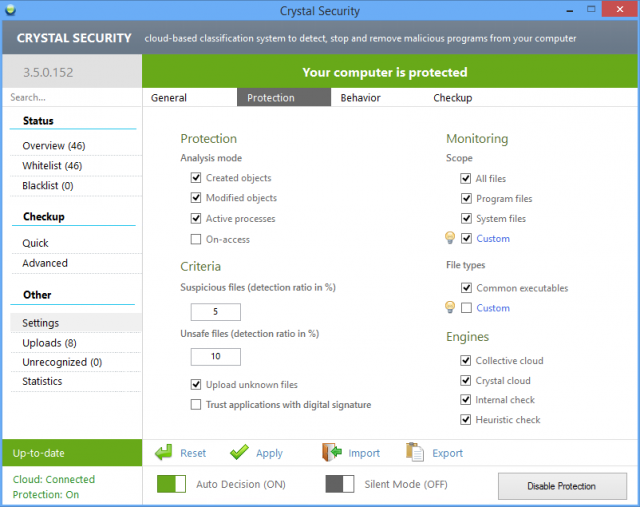
Crystal Security is a compact cloud-based malware detector
Install any anti-malware with real-time protection and you’re generally weighing down your system with services, drivers, DLLs, background processes and more.
Crystal Security does things differently, its tiny download unpacking to a single 830KB executable which runs happily on Windows XP and later.