
Apple battles Wordle with new Emoji Game
Newspapers have long been associated with all manner of games and puzzles, including crosswords, sudoku and so on. This is something that has endured the crossover from print to digital, with the likes of Wordle from the New York Times remaining incredibly popular.
Now Apple is looking to get in on the action, announcing a new puzzle called Emoji Game. The puzzler is just the latest addition to the Apple News+ collection, giving subscribers a new challenge every day.

The rise of the machine identity and what it means for cybersecurity [Q&A]
A report earlier this year highlighted the fact that machine identities now vastly outnumber humans.
This leads to a wider attack surface leaving many organizations vulnerable to cyberattack and loss of data. We spoke to Refael Angel, the co-founder and CTO of unified secrets and machine identity platform Akeyless Security, to find out more about the problem and how enterprises can protect themselves.
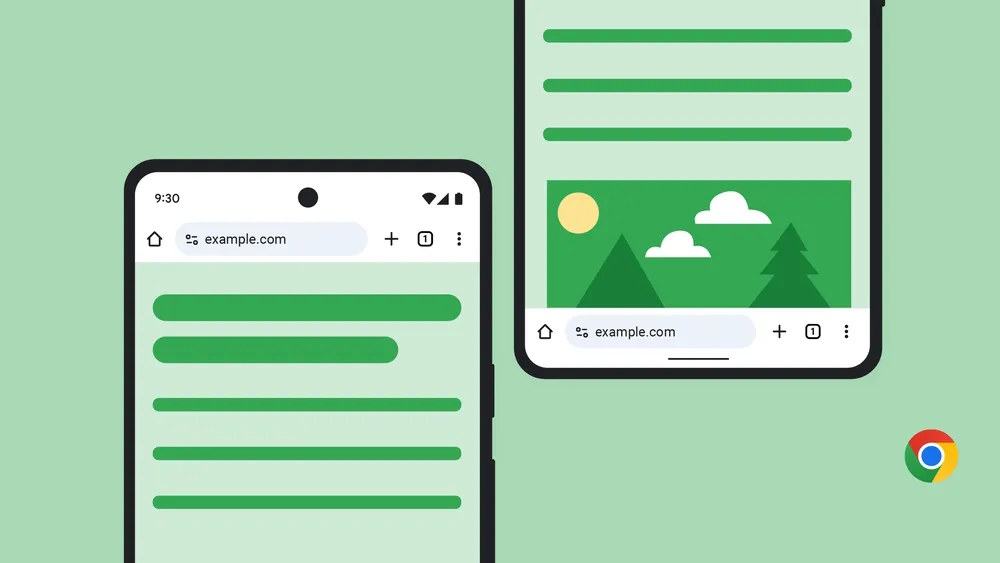
Google Chrome address bar – are you a top or a bottom?
Across all platforms, Google Chrome remains one of the most popular – if not the most popular – web browser. But while the desktop version of the software is versatile, customizable and flexible, the same cannot be said of the mobile apps.
And this is why an announcement made by Google several weeks ago caused a flurry of excitement. On the face of things, the news that it would be possible to move the address bar from its familiar position at the top of the browser may not seem huge, but now that it is rolling out, it is becoming clear that it is actually pretty significant for Android users.

Microsoft announces Extended Security Update programs for Exchange and Skype for Business
Support has ended, or is coming to an end, for a lot of Microsoft products at the moment. Perhaps the most notable or well-publicized is Windows 10, but this is far from being the end of the story.
In a move designed to push people towards Teams, killing off Skype and Skype for Business made a lot of sense. The same is true of the aging Exchange 2016 and 2019 losing support. But while this makes sense for Microsoft, it is also incredibly disruptive and expensive for businesses that rely on these tools – hence two newly announced Extended Security Update programs.

AI is fueling an explosive rise in fraud and digital identity crime
AI-powered fraud is evolving faster than most organizations can detect it. That’s the message from Proof, the identity authorization company, in its new report, The Trust Ledger: Transaction & Identity Fraud Bulletin.
The research reveals how synthetic identities, stolen credentials, and generative AI are fueling a surge in digital impersonation and fraud across industries.

You can turn your car into an Atari gaming arcade and play Asteroids and Breakout
Old video games never really die; they just find new screens to live on. Classic titles like Asteroids and Breakout have been part of the gaming culture for decades and now, they're being reintroduced inside a place few expected -- the car.
AirConsole, an in-car gaming platform, has partnered with Atari to bring Asteroids and Breakout to supported Volkswagen models starting today.

Millions of unsecured Wi-Fi networks are putting data at risk
New threat intelligence from Zimperium reveals over five million unsecured public Wi-Fi networks have been detected globally since the beginning of 2025, with a staggering 33 percent of users still connecting to these open networks, putting enterprise data at risk in the process.
“Mobile devices are now a primary gateway to corporate data, but during travel, they’re also the most vulnerable,” says Kern Smith, VP of global solutions at Zimperium. “Unsecured Wi-Fi, phishing disguised as travel alerts, and risky sideloaded apps are creating an ideal attack surface for cybercriminals -- especially in peak travel months.”

Cloaking-as-a-service set to reshape the phishing landscape
Imagine if hackers could give their scam websites a cloak of invisibility, showing one web page to regular people and a harmless page to security scans. Sneaky, huh?
According to new research from SlashNext that’s essentially what’s happening as cybercriminals start to leverage AI-powered cloaking services to shield phishing pages, fake stores, and malware sites from prying eyes.

CrapFixer update fixes Windows 11 and turns it into the operating system you deserve -- download it now!
There are a number of great tools that you can use to improve Windows 10 and 11, but our new favorite is CrapFixer. The free program can remove bloat, ads, AI, unwelcome data collection, and more from the operating system.
Although it was originally created seven years ago it has been completely rewritten for Windows 11 and a new update makes it even better, with its own small, modern Policy Editor.

The future of encryption in a post-quantum world
As quantum computing speeds edge closer to practical use, the ‘harvest now, decrypt later’ approach is already in motion with adversaries collecting encrypted data today, anticipating they'll be able to crack it tomorrow. But is enough being done to prevent it?
New research from Forescout highlights the urgent need for organizations to prepare for a future where quantum-capable adversaries can break widely used cryptographic protocols.

Application layer comes under threat
A new report from Contrast Security exposes a growing crisis at the application layer as adversaries use AI to easily launch previously sophisticated attacks at scale.
Recent reports from Verizon (DBIR 2025) and Google Mandiant (M-Trends 2025) confirm what many security leaders already suspect: components of the application layer are among the most targeted and least protected part of the modern enterprise.

Outdated printer firmware can leave organizations open to attack
In the past the printer has tended to be a pretty dumb device, but as they’ve gained more features and extra connectivity printers have become a target for attacks and potentially a way of gaining access to networks.
A new report from HP Wolf Security, based on global study of 800+ IT and security decision-makers (ITSDMs), highlighs the challenges of securing printer hardware and firmware.

Financial firms keen to use AI but their data isn't ready
A new study into AI readiness shows that while financial services firms are ready to adopt AI, they still have work to do in terms of improving data quality and modernizing systems.
The study from Indicum finds many financial services firms are hindered by legacy data systems and outdated IT infrastructure, which often lack the real-time processing and data quality capabilities required for effective AI deployment.

Matanbuchus 3.0 is a serious malware threat spread via Microsoft Teams
The Matanbuchus malware loader is not new – it has been around for at least 4 years – but it has evolved into something incredibly dangerous.
Matanbuchus 3.0 has been found targeting victims as part of a ransomware attack. Described as being “highly targeted”, the cyberattack campaign uses Microsoft Teams as a delivery method for the latest version of the malware loader. The highly sophisticated attack employs a Microsoft Teams call impersonating an IT helpdesk.
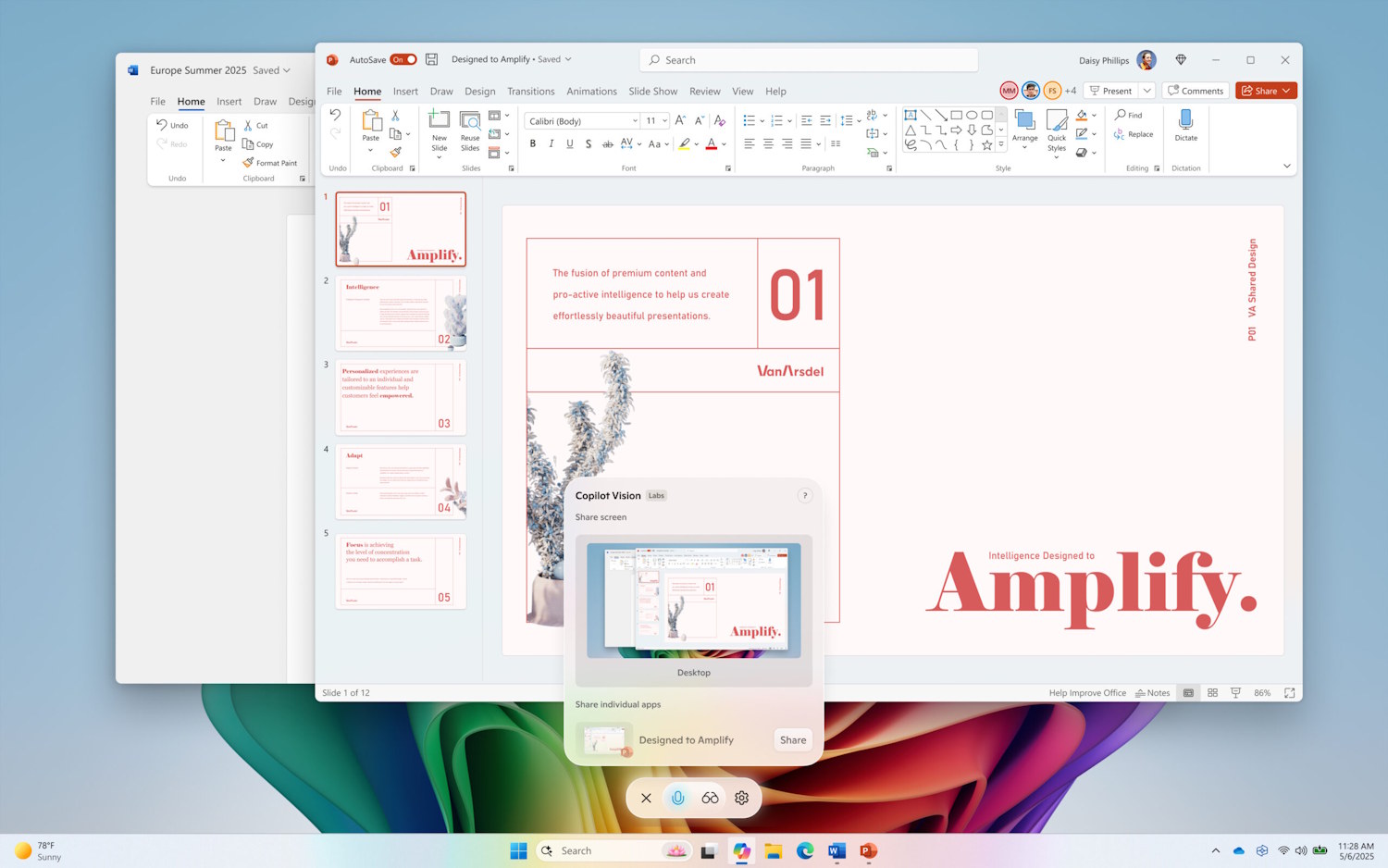
Microsoft rolls out whole desktop sharing to Copilot on Windows 11
Microsoft’s development of Copilot continues apace, and the latest update is one that could prove to be divisive. Windows 11 users signed up to the Windows Insider program are being given a new option in Copilot Vision for Windows – namely the ability to share the entire desktop with the AI tool.
Sharing your desktop in this way means that Copilot Vision for Windows will be able to see everything that is on your screen asnduse it in your interactions. While there are many potential uses for this, the controversy caused by screenshotting desktops with the Recall feature of Windows that was so controversial that Microsoft had to withdraw and rebuild it.