
Kim Dotcom reveals his Megaupload replacement -- Mega
You’ve got to hand it to Megaupload founder Kim Dotcom. Despite living under house arrest, his assets frozen, and facing the prospect of extradition to the United States and up to 20 years in prison if found guilty of copyright theft, money laundering and racketeering fraud, he’s pressing ahead with plans for a new file-sharing site.
Mega, his Megaupload replacement, was revealed yesterday, and despite just consisting of a holding page at the moment, was quickly overwhelmed. "Millions of users hitting at once. I'm delighted by the interest. But servers can't handle it. The new Mega will. WOW!!!" Dotcom tweeted an hour after the news broke.

Whom do you trust with your personal data?
Like Microsoft in the late late 1990s and early 2000s, antitrust scrutiny confronts Google on two continents. Among the core issues emerging from the preliminary investigations: privacy. Your data, who has access to it, how clear are the search giant's privacy policies and how carefully does the company adhere to them. But Google is by no means the only concern. Facebook is renown for making user interface and feature changes that can suddenly and unexpectedly expose personal data, and there are problems past about third-party applications accessing what they shouldn't.
As more established tech companies offer more services in the cloud, increasingly there is lingering question: Whom do you trust with your personal data? Last month, Apple expanded cloud services with iOS 6 and iPad mini and the fourth-generation 9.7-inch model go on sale November 2, supporting them. On Friday, Microsoft launched Windows 8 and Surface and does same with Windows Phone on October 29. To get the most from these products, users must have a Microsoft account, like Apple and Google require for their cloud services. Meanwhile, Office 365 extends online sync, storage and collaboration features.
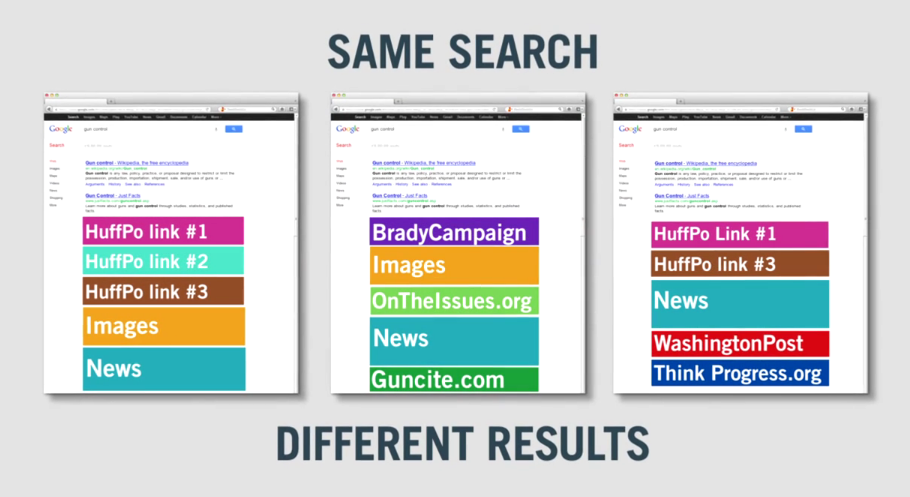
Your search results may vary -- why I switched from Google
Search engine DuckDuckGo released a video a few days ago that shows how Google personalizes results for all signed in and signed out users. It asked 131 people to search for the same Election related topics ("abortion", "gun control", and "Obama") on Google at the same time, and most of them received slightly different results.
That Google personalizes results in this way is hardly new information. The company has been doing it since 2009 and Eli Pariser covered the topic in depth in his 2011 book, The Filter Bubble (a great read). He also gave an enlightening Ted Talk on the subject in which he observes that "the Internet is showing us what it thinks we want to see, but not necessarily what we need to see."

Dropbox for Teams admins can help users enable security features
Following the introduction of two-step verification, the popular cloud storage service Dropbox has updated Dropbox for Teams to help team admins enable security features.
The service is updated starting today, and will allow admins to verify which team members have turned on two-step verification and to email those that have yet to enable the feature, all through the "Team" tab. The feature is implemented to aid admins instead of offering them the possibility to remotely enable an extra layer of security through two-step verification, and according to the blog post new features will be developed over time.

MRU-Blaster helps protect your privacy
"Most Recently Used" lists are generally a good feature in applications, as they allow you to reload recent documents without having to remember exactly where they’re stored.
But, of course, there are also privacy implications with doing this. And so if you don’t want other users of your PC to see exactly which documents you’ve been accessing recently, you may want to use a third-party tool, like MRU-Blaster, to wipe them all away.

Ad-Aware 10.3 improves with age
Lavasoft has announced the availability of Ad-Aware 10.3, an incremental update to the classic antivirus tool that delivers small but still worthwhile improvements all across the package.
Installation is now faster and more straightforward, for instance.

DeepSound protects your files from prying eyes
When you have personal documents that you’d like to keep safe from snoopers then your first thought might be to encrypt them. But this isn’t always the best idea. Just seeing a “Mysterious.doc” file that they can’t open will be enough to tell others that you’ve something to hide.
The free DeepSound, though, offers a different approach. In just a few clicks it’ll take your documents and conceal them within WAV or FLAC files. And if anyone checks, now, all they’ll see is regular audio files that play as usual: there’s nothing to be suspicious about.

A+ Proxy Finder locates and rates HTTP, HTTPS and SOCKS proxies
If you’d like to find a good proxy server to keep you anonymous online then there are plenty of online sources which claim they can help. These lists aren’t always reliable, though -- some recommended servers may not work any more, others aren’t as anonymous as you might think -- and you can spend quite some time manually checking their various suggestions before you find anything that suits your needs.
If all that sounds too much like hard work, then, you might prefer to use the free A+ Proxy Finder, which automates the process of locating and evaluating HTTP, HTTPS and SOCKS proxies.

Your Fourth Amendment rights don't apply to Facebook
Last week, a federal district court made a ruling that has broad implications for your privacy on Facebook. The end result is that you should be much more careful about what you share on Facebook with whom, because regardless of whether your profile is private or not, the Federal Government can use your friends to gather evidence against you, which in turn can be used against you in a court of law.
This is what happened to accused gangster Melvin Colon. The Bronx, N.Y. man used his Facebook to brag about his apparent exploits, which according to reports included messages of loyalty to his gang, posts on violent acts and threats to other people. The US Government was then able to find a friend who worked against Colon, and allowed law enforcement to use his or her Facebook to gather evidence.

Retailers may soon use tagged Facebook photos to identify you in stores
A new tech startup that produces facial recognition camera systems tied to Facebook tagged photos, plans to offer the technology to more traditional physical stores so they could offer you appropriate deals as you enter their business. That’s great for stores that want to have more targeted information about you, based on a bit of your history and likes. But what about privacy, what are the implications?
For now, you are not included in this scheme unless you opt in via Facebook to a third party service. The service would then present tailored deals to your mobile device when you enter an establishment using the technology (currently being tested in Tennessee). Facedeals, the provider, says this simply bolsters and leverages check-ins so that local businesses have more personal information, and by knowing and targeting the products they offer you based on your likes and preferences they can seem more relevant, like discounted or free drinks for using the service at a bar & grill.

Spend your vacation with one of these 18 software downloads
The release of Windows 8 draws ever closer and this means that there is a slew of apps being updated to add support it. Paragon Image Backup for Windows 8 is one such program, giving you the chance to backup and restore your data free of charge. Fans of system tweaking and optimization should take a look at Auslogics Disk Defrag 3.5.0.0 and Auslogics BoostSpeed 5.4.0.0, which can be used to ensure the best possible performance from your hard drive as well as giving you a raft of tools to help boost the speed of Windows.
Whether you’re upgrading to Windows 8 or not, you should keep an eye on your internet connection to check how it is being used by different programs, or malware, and this is something that Net Guard 2.0.7.0 enables you to do. This week also saw the release of Windows Essentials 2012, the latest collection of free tool from Microsoft including Live Messenger, Movie Maker, SkyDrive and more.

Google pays record $22.5 million for Safari cookies
The rumors were true. Today, the US Federal Trade Commission fined Google $22.5 million for putting its hand in the Safari cookie jar. Technically, the amount is a settlement, but effectively a fine. The search and information giant circumvented Apple browser privacy controls to mine personal data.
Google isn't the only company accused of bypassing Safari privacy controls, but it is most answerable to regulators. The search company already is under 20-year oversight for violating the FTC Act. In October 2011, Google agreed not to misinterpret its consumer privacy practices.

Steve Wozniak is right -- users are going to eventually be burned if they rely solely on cloud backup
Apple co-founder Steve Wozniak this week warned of the perils of depending too much on cloud storage and the general press reacted like this was: A) news, and; B) evidence of some inherent failure in cloud architecture. In fact it is not news (Woz never claimed it was) and mainly represents something we used to call “common sense”.
However secure you think your cloud storage is, why solely rely on it when keeping an extra backup can cost from very little to nothing at all?

Scattered clouds: Why I don’t trust other people with my data
It’s the Next Big Thing. Any vaguely IT-related person just has to say something like “computing is moving to the cloud” and everyone nods their heads wisely. And so it is with Office 2013. I’ve been using the Public preview of Office since it appeared two weeks ago, and I have to say I like it; and I also like the much more straightforward integration with Skydrive and Sharepoint. But there’s still no way I’m going to change my default habit of local saving and working to using the Cloud as my primary storage. And here’s why.
There are several aspects to this, and the first two are most revealing of the way in which people sitting in Redmond, Wash., Cupertino, Calif., or most other major corporations live in a different world from the rest of the population of this little blue planet of ours.

Simply set up Parental Controls with Kurupira Web Filter
If you’ve tried setting up parental controls before, you’ll know this can often involve a lot of work. You may need to create accounts for each one of your children, for instance, before defining in very precise detail exactly what sort of content they can access, and what they really shouldn’t.
And so we were very surprised to see how straightforward the free Kurupira Web Filter was, by comparison. No “per user” settings, no lists of content types, no real need to set up any web filtering options at all: the program automatically blocks “inappropriate” websites just as soon as it’s installed, without you having to take any additional actions.