
SailPoint launches updated identity governance platform
Identity management company SailPoint is announcing enhancements to its open identity platform, designed to enable identity to be woven throughout the IT operations and security fabric of organizations.
IdentityIQ version 7.2 enables a unified approach to identity governance that shares identity information across all IT and security investments.

Apple responds to iPhone X Face ID privacy concerns but dodges law enforcement request query
One of the undeniable highlights of Apple's iPhone X is Face ID -- the face recognition technology that makes it possible to unlock a phone with a glance. While exciting and impressive, many people have security and privacy concerns about the feature, and last month Senator Al Franken wrote to Apple asking a series of questions and outlining his worries.
Apple has now responded to Franken, just ahead of the launch of the iPhone X in a little over two weeks. The company points to a series of documents that have already been made public, but also goes on to provide some detail about how Face ID data is stored and used.

Iran may have hacked the UK Parliament
It seems to be Iran, and not Russia, who is behind last summer's cyber attack against the UK Parliament. At least that’s what The Times is reporting, and it’s backing its claims with "secret intelligence assessment."
If that truly is the case, this would be Iran’s first foray into cyber-warfare. When it comes to possible motives behind the attack, it’s all still in domain of speculation. From looking into UK’s interests to try it to make any concessions, to scouting for advantages in trade, to changing the direction of the nuclear deal.

Why orchestration and threat intelligence are a perfect match
Today’s adversaries are moving faster than ever before, and for organizations trying to protect themselves against advanced and evolving threats, speed is essential. But the reality is that security teams don’t necessarily have the time to manage and evaluate every single alert they receive while also completing their everyday tasks -- and even the most skilled teams are struggling to keep up.
Certain aspects of cybersecurity are just inherently slow, like copying and pasting information from one tool to another. And if security teams are focused on getting through these simple, repetitive, time consuming tasks, it’s no wonder they struggle to achieve the speed needed to outpace hackers. And, at worst, it can mean a threat falls through the cracks.

Google offers its strongest ever security with new Advanced Protection Program
As part of Cybersecurity Awareness Month, Google has announced numerous security-related updates including revamped phishing protection. Now the company has also announced what it is referring to as its "strongest security, for those who need it most."
Aimed at protecting people who are most likely to find themselves the target of attacks -- Google suggests journalists and human rights workers as examples -- the new Advanced Protection Program is being made available to anyone who wants to use it. It will protect Gmail, Google Drive and YouTube data with a variety of measures including a physical authentication key.

Are your employees snooping on your corporate network?
A new survey of IT security professionals reveals that 92 percent of respondents say employees at their organizations try to access information that is not necessary for their day-to-day work.
The study from identity management company One Identity also shows that IT security professionals themselves are among the worst offenders for corporate data snooping. One in three respondents admit to having accessed sensitive information that is not necessary for their day-to-day work -- showing an ongoing abuse of elevated rights given to the IT security role.

Companies overlook risks in open source software
Open source code helps software suppliers to be nimble and build products faster, but a new report reveals hidden software supply chain risks of open source that all software suppliers and IoT manufacturers should know about.
The recent Equifax breach for example exploited a vulnerability in a widely used open source web framework, Apache Struts, and the study by software monetization specialist Flexera points out that as much as 50 percent of code in commercial and IoT software products is open source.

Teen image sharing site We Heart It reveals historic security breach affecting over 8 million accounts
We Heart It -- the image sharing service used by at least 40 million teenagers -- suffered a "possible security breach" several years ago. The breach affects more than 8 million accounts that were created between 2008 and November 2013.
Although this is a historic data breach, in which information from the user account database was leaked, We Heart It was only notified about it on October 11. The company says that email addresses, usernames, and encrypted passwords were accessed, and it recommends that users now change their passwords as they are not secure.

Microsoft suffered an internal bug database hack in 2013 and didn't tell anyone
Four and a half years ago, an internal bug-tracking database at Microsoft was breached by a "highly sophisticated hacking group," according to five former employees of the company. The hack of the secret database was never made public.
It is believed that this is only the second time such a corporate database has been breached. US officials were alarmed to learn of the hack which could have exposed software vulnerabilities to the attackers, reports Reuters.
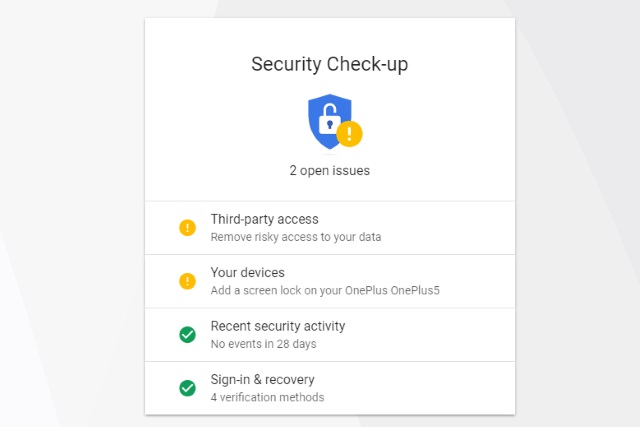
Google launches personalized phishing protection and updated Security Checkup tool
We're in the middle of Cybersecurity Awareness Month and Google is taking part. The company has launched two updated protection tools to help keep internet users safe online.
While Google refers to "two new protections," these are really updates rather than completely new offerings. Both the Security Checkup tool and Google Safe Browsing have been updated to make them more personal, and both of them will adapt over time to protect against new threats.

Google and IBM launch open-source security tool for containers
Google and IBM, together with a few other partners, released an open-source project that gathers metadata that developers can use to secure their software.
According to an IBM blog post, the goal of the project is to help developers keep security standards, while microservices and containers cut the software supply chain.

Google rolls out Chrome Cleanup to help secure its web browser
With so much time now spent online, and with so many cloud-based tools now in use every day, we're all spending more time than ever in our web browsers. To ensure that this is as secure an experience as possible, Google is rolling out a trio of important changes to Chrome -- for Windows users, at least.
At the heart of these changes is Chrome Cleanup. This feature detects unwanted software that might be bundled with downloads, and provides help with removing it -- but Mac and Linux users miss out.

[Updated] Microsoft has patched Windows against the KRACK Wi-Fi vulnerability -- Google will secure Android soon
Earlier today, news broke about the KRACK vulnerability that affects the WPA2 protocol. Security researchers have warned that the problem affects millions of devices running everything from Windows to Android and Linux.
Microsoft has announced that it has already released a security patch to fix the vulnerability in Windows. Google says that a patch for affected Android devices will be released "in the coming weeks."

AsTech offers Qualys Cloud Platform with a $1 million breach cost guarantee
The Qualys Cloud Platform is designed to give customers a continuous, always-on assessment of their global security and compliance posture across all global IT assets, wherever they reside.
Cyber risk management company AsTech is boosting its attractiveness further for its Managed Qualys Service customers by offering a $1 million guarantee for securing perimeter networks.

Android: DoubleLocker ransomware encrypts data and changes PINs
A new breed of Android ransomware has been discovered that hits victims with a double whammy. DoubleLocker not only encrypts data as all ransomware does, it also changes the PIN on the target device.
DoubleLocker was discovered by security researchers at ESET. They say that the ransomware abuses Android accessibility settings, and is the first to use a double-lock approach. Based on previously released banking malware, it is though that a test version of DoubleLocker could have been in the wild since as early as May.