
Cisco's new network can learn, adapt and overcome security threats
Cisco has unveiled its network of the future designed with the ability to learn, adapt and evolve to combat security threats and manage the increased load put on networks by an ever-increasing number of devices.
The company created its new network with the intent of developing an intuitive system that can anticipate actions, stop security threats and continue to evolve and learn over time. Cisco's network of the future will allow businesses to solve the challenges they face in a time of increased connectivity and distributed technology.

Retailers will lose $71bn due to payment fraud
Retailers are facing losses of up to $71 billion globally as the number of fraudulent card-not-present (CNP) transactions rises hugely within the next five years.
A new report from Juniper Research has revealed that a number of different factors are driving the increase in fraud, including the US shifting towards EMV cards, delays in 3DS 2.0 and click-and collect fraud methods.

Google Play fails to catch trojan-injected apps (again)
Getting your Android apps through Google Play is considered safe, but there are times when even the search giant's store is dangerous. Case in point, Kaspersky uncovered two more trojan-infected apps that weren't removed until they had over 60,000 installs.
Kaspersky security researcher Roman Unuchek reports that, since September 2016, he has discovered "several dozen new malicious apps" on Google Play, all of which "were rooting malware that used exploits to gain root rights on the infected device." Obviously, Google failed to catch any of those in time either.

Mobile employees are willing to place security above privacy
Given the recent increase of violent incidents around the world, in addition to everyday risks and natural disasters, businesses are naturally concerned about protecting their staff.
New research by enterprise safety application company Everbridge shows that mobile workers expect that their companies will be able to provide safety information to them should something happen or should they be in the proximity of a serious event. It also shows staff are willing to sacrifice privacy to achieve this.

Top websites struggle to guard against sophisticated bot attacks
A report released today shows that, while an average of 16 percent of websites across all industries can thwart simple bot attacks, only five percent are able to properly protect against sophisticated attacks.
The study from bot detection specialist Distil Networks, in conjunction with the Online Trust Alliance (OTA), evaluated the top 1,000 websites in retail, banking, consumer services, government, news media, internet service providers and OTA members.

Consumers ignore security risks for free Wi-Fi
A growing number of British consumers are using their neighbors' Wi-Fi, sometimes even without permission, because they can't afford their own.
This is according to a new report by Santander, which also says that the price of phone and broadband services has increased hugely over the past ten years.

Microsoft: We disabled third-party anti-virus software in Windows 10 Creators Update to keep users safe
Two weeks ago, Kaspersky Labs filed antitrust complaints against Microsoft in Europe, alleging that the software giant disabled third-party antivirus software in Windows 10 in order to benefit Windows Defender.
In a long blog post today, Rob Lefferts, director of program management for Windows enterprise and security, admits (without mentioning Kaspersky specifically) that Microsoft "temporarily" disabled some parts of AV software it considered incompatible with Windows 10 Creators Update.

Web hosting company pays $1 million after Erebus ransomware attack
The cost of a ransomware attack can be pretty substantial. Businesses that are not well prepared are looking at lost revenue from downtime and massive damage to their reputation, not to mention a pretty hefty ransom bill as well.
For web hosting company Nayana, that was $1 million. Nayana, which is based in South Korea, had 153 of its Linux-based servers infected by the Erebus ransomware on June 10. The attack affected roughly 3,400 customers that relied on its services for hosting websites, databases and multimedia content.

New vulnerability manager aims to prevent the next WannaCry
When the WannaCry attack hit last month, a patch was already available to prevent it. Its victims were those who had failed to deploy it.
Software management company Flexera is aiming to help companies close the risk window between patches and attacks with the launch of its new Software Vulnerability Manager.

Retail industry leads the way in data breaches
The largest share of data breach incidents involved the retail industry, closely followed by food and beverages, according to a new report.
The 2017 Global Security Report from Trustwave shows that 22 percent of incidents involved the retail industry, followed by food and beverages at 20 percent.
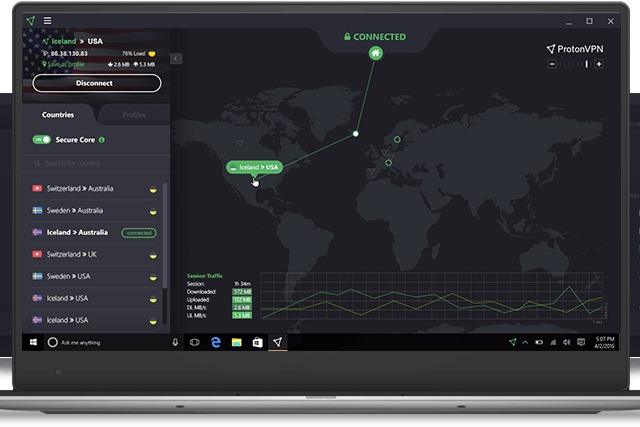
ProtonVPN is a free VPN service that's now available to everyone
ProtonMail has opened up its free VPN service to anyone who wants to use it. ProtonVPN was previously only available to a limited number of beta testers, but now everyone can secure their internet connection for free.
The company is best known for its encrypted email service, but the prospect of a free VPN tool will also be enticing to anyone who has concerns about privacy. It also provides a free way of bypassing internet restrictions that may be put in place by governments or ISPs.

New report reveals how malware uses evasion to hide in plain sight
People have been hiding secrets in everyday objects for hundreds of years. The digital world is no exception, and McAfee Labs has released its latest Quarterly Threat Report, part of which looks at how evasion techniques can be used to distribute malware.
The use of evasion techniques started in the 1980s, when a piece of malware defended itself by partially encrypting its own code, making the content unreadable by security analysts. Since then a dark market for off-the-shelf evasion technology has developed and several contemporary malware families now make use of evasion techniques.
UK officials believe North Korea is behind WannaCry ransomware
Nearly a month after it struck devices around the globe, new information has emerged surrounding the major WannaCry ransomware attack.
The BBC says British officials from the National Cyber Security Center (NCSC) are now claiming infamous North Korean cyber-criminal group Lazarus was behind the attack.

Cyber security is more important than Brexit in boardroom talks
Cyber security is a top concern in the boardroom, to the point where it’s a more important issue than Brexit. That's according to a new report from Radware examining the state of cyber security across the US and Europe.
The study shows that in 85 percent of cases security threats are now being discussed on a board level. Almost all of them (94 percent) see cyber security as a top priority, and two thirds (62 percent) see it as "extremely important." This figure is up nine percent, compared to last year.

Unsecured Amazon server leaks details of 198 million American voters
Personal data and profiling information about millions of American voters has been exposed in what is believed to be the largest ever leak of its kind.
198 million records were found stored on an unsecured Amazon S3 server owned by Deep Root Analytics, a Republican data analytics firm. It is thought that the data, which dates back more than a decade, includes information about every registered American voter.