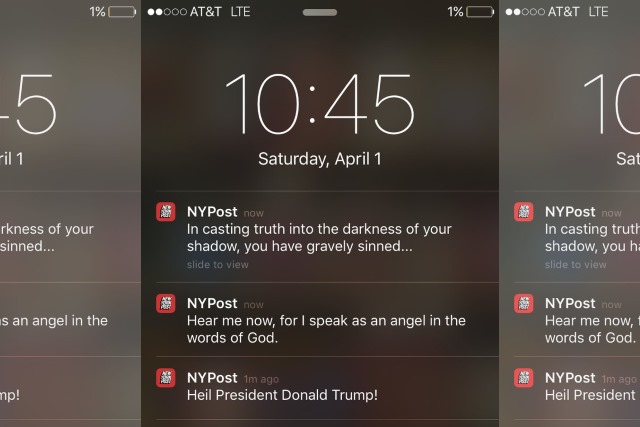
Hacked! New York Post mobile app compromised in security breach
The New York Post suffered a security breach this weekend when its push notification system was compromised. Unknown attackers used the system to send out messages to users of the New York Post mobile app.
The hackers sent out messages with strange, cryptic content. One read "Heil President Donald Trump!", while others had a religious or spiritual tone to them, and one quoted a Nirvana lyric.

Top tips: How to protect your privacy against ISP snooping
We live in an age where privacy is valued incredibly highly, but at the same time there are more and more ways for our privacy to be encroached upon. One of the most recent concerns came after the US Senate voted last week to allow ISPs to sell customers' browsing histories without consent.
Things were turned up a notch a couple of days ago when the House agreed and voted to repeal FCC-approved privacy rules. Since the result of the vote was known, there have been reports of a huge surge in interest in VPN tools, private search engines and the like, and now VPN review site The Best VPN has come up with a series of tips to help internet users maintain their privacy, and stop ISPs from getting their hands on potentially sensitive information about browsing habits.

What your smartphone knows about you
Currently, many people unlock their phones by pressing their thumbs onto fingerprint sensor panels or using their fingers to draw patterns on the screens. Those authentication methods are certainly high-tech, but, before long, you’ll likely be unlocking a phone that knows more about you than you’d ever imagine.
Check out some of the smartphone security methods being tested and what they might mean for future users.

WikiLeaks releases Marble source code, used by the CIA to hide the source of malware it deployed
Today, WikiLeaks publishes the third installment of its Vault 7 CIA leaks. We've already had the Year Zero files which revealed a number of exploits for popular hardware and software, and the Dark Matter batch which focused on Mac and iPhone exploits.
Now we have Marble to look at. A collection of 676 source code files, the Marble cache reveals details of the CIA's Marble Framework tool, used to hide the true source of CIA malware, and sometimes going as far as appearing to originate from countries other than the US.
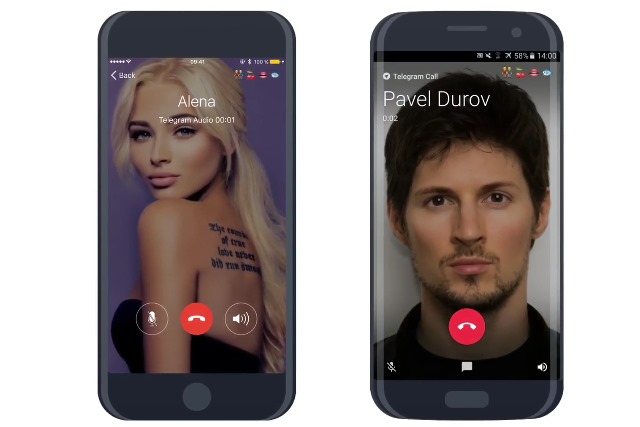
Secure messaging app Telegram gains end-to-end encrypted voice calls
In an age of constant surveillance and eroding privacy, there is increasing interest in secure messaging platforms such as WhatsApp and Telegram. While Telegram has gained quite a following, there is one feature that users have been begging for: voice calls.
Now users' prayers have been answered. The latest update to Telegram finally heralds the arrival of secure voice calling, and it features an interesting key exchange mechanism: users need just compare four emoji. If the emoji match, the connection is secure!

Security professionals still struggle with the cloud and IoT
Organizations are using multiple cloud services and security staff are worried about the visibility problems this presents as well as the risks presented by IoT devices.
These are the findings of a survey of RSA attendees, carried out by security management and threat intelligence specialist AlienVault. A third of respondents to the survey describe the state of security monitoring within their organization as 'complex and chaotic'.

Calls for transparency as UK government meets technology firms to discuss encryption and privacy
The UK Home Secretary Amber Rudd is today meeting with technology firms to discuss how they can help to combat terrorism. The meeting comes just days after Rudd said that encrypted messaging services such as WhatsApp should not be a "secret place to hide."
Calls for backdoors to be built into encrypted apps and services have been met with shock, derision and incredulity, but some have pointed out that the controversial Investigatory Powers Act (aka the snooper's charter) already grants the government the right to force the removal of encryption. Ahead of the Rudd's meeting, civil liberty organizations have written a letter demanding transparency.

Businesses lose 44 data records every second
Before you are done reading this article, there will have been more than 2,500 digital records stolen. This is according to a new report by Gemalto, which was released to show just how unprepared UK's businesses are for cyber risks.
Gemalto says that in 2016 1.37 billion data records were compromised. That basically means 3,776,738 records every day, 157,364 every hour, 2,623 every minute, or 44 data records every second.

Almost 40 percent of industrial computers face cyber attacks
In the second half of 2016 Kaspersky Lab products around the world blocked attempted attacks on 39.2 percent of protected computers that it classifies as being part of industrial enterprise technology infrastructure.
The study from the Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (ICS CERT) also reveals that the top three sources of infection were the internet, removable storage devices, and malicious e-mail attachments and scripts embedded in the body of e-mails.

Non-malware attacks pose greater risk to business
Non-malware attacks pose more of a business risk than commodity malware attacks according to 93 percent of cybersecurity researchers.
The study by endpoint security company Carbon Black interviewed more than 400 cyber security researchers and finds that 64 percent say they’ve seen an increase in non-malware attacks, such as remote logins and in-memory attacks, since the beginning of 2016.

Comodo launches no-cost DNS security for businesses
Malicious websites provide a haven for malware and other threats to lurk, waiting for users to click links in emails or on other sites to contract an infection.
Cyber security specialist Comodo is helping to combat this problem by making its DNS- and cloud-based web security offering, Dome Shield, available free of charge to both individuals and enterprises.

How the dark web creates a fraud pandemic
The statistics continue to chill. Two point three million estimated fraud victims in the UK alone in 2015 according to the ONS. 173,000 confirmed reports of identity theft amongst CiFas members (largely utilities and finance companies) in 2015.
From a consumer perspective the chances are that over a period of three to four years you are now more likely than not to be a victim of a successful fraudulent act of some kind.

CIA's internal hacking tools rival those of the NSA
Debate and discourse around WikiLeaks’ announcement about a series of leaks from the CIA continue unabated. Codenamed "Vault 7," WikiLeaks claims this is the largest classified information leak to have come from the CIA to date. Added to that, only one percent of documents have been made public so far.
From the leaked documents it’s become clear that the CIA has created its own internal hacking capabilities to rival that of the NSA. It may be more tactical than strategic -- but with exploit sets including Android, IoS, Samsung TVs, Linux, Mac, zero day attacks and more, it could certainly give the NSA a run for its money.

European information security execs face major challenge from insider threats
New research shows that 35 percent of employees across the UK, France, Germany and Italy admit to have been involved in a security breach.
This presents CISOs with a significant challenge when it comes to protecting company data, particularly in light of the forthcoming European General Data Protection Regulation (GDPR) which comes into effect in early 2018.

Microsoft's Docs.com search feature leaks sensitive files
Users of Microsoft's Docs.com website took to Twitter to complain after files marked as private were made public by the sites' search function.
In response, Microsoft pulled the search feature from the site, but it is now back up and running. Even during the time it was not possible to search the site directly, Google and Bing searches could still be conducted to reveal social security numbers, job applications, contact details, and other private information.