
Most enterprise attempts at email authentication fail
A new study shows that 75 percent of large businesses attempting implementation of the DMARC email authentication standard are not presently capable of using it to block unauthorized email.
This means that enterprises are putting their own security, compliance, and brand protection at risk. Automated mail authentication specialist ValiMail looked at email authentication policies for more than a million business domain names, including those of Fortune 1000, NASDAQ 100, and FTSE 100 businesses.

The 'age of automation' can benefit the security landscape
Artificial intelligence (AI), machine learning and automation are technology trends dominating discussions in many different industries at the moment and cyber security is no exception.
As cyber criminals become more advanced and the threat landscape continues to develop, businesses are looking to new technologies that can help secure their organization in a more proactive way.
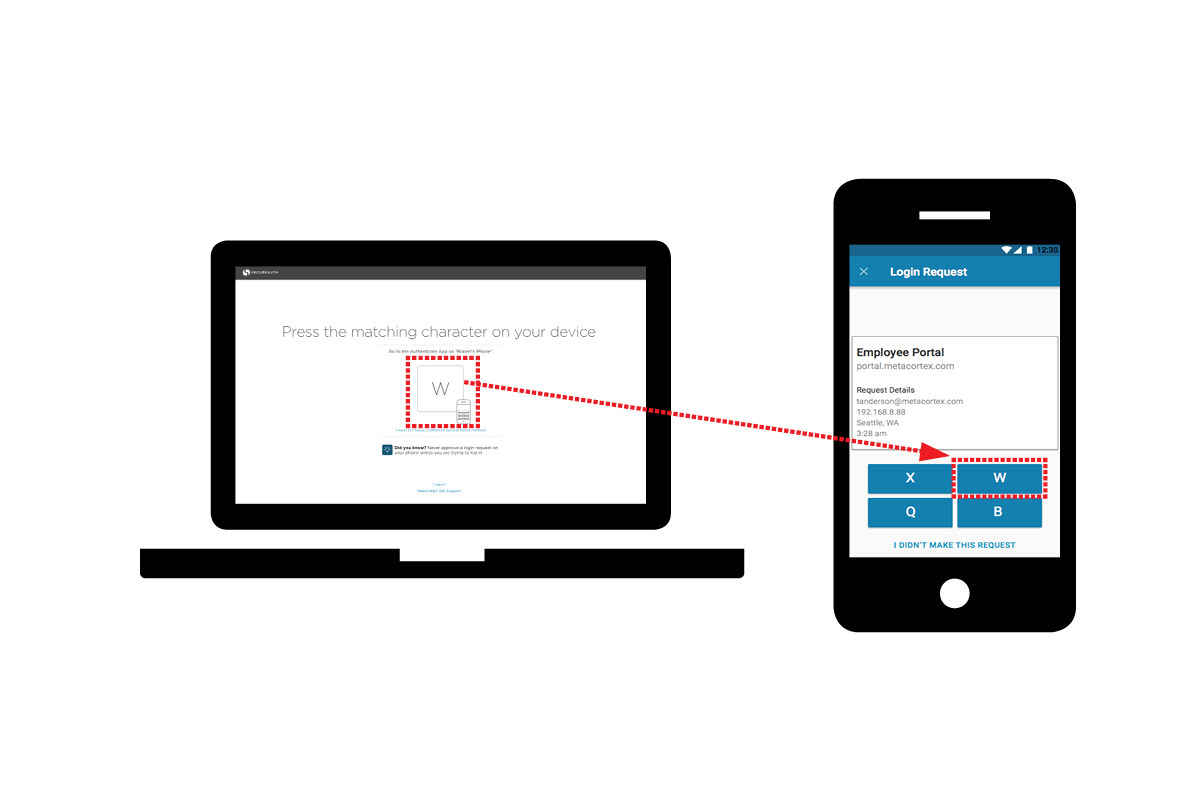
Symbol-to-accept strengthens multi-factor authentication
One of the more popular ways of securing logins in recent times has been the use of push-to-accept technology, sending a verification message to a user's mobile device.
However, this runs the risk of users inadvertently approving login requests that they didn't initiate. Adaptive access company SecureAuth is launching its new Symbol-to-accept technology to boost security without sacrificing convenience.

60 percent of enterprises have fallen victim to social engineering in 2016
A new study from cyber security company Agari reveals the scale of social engineering attacks on industrial organizations across the US.
Of over 200 security leaders surveyed 60 percent say their organizations were, or may have been, victim of at least one targeted social engineering attack in the past year, and 65 percent of those who were attacked say that employees' credentials were compromised as a result. In addition, financial accounts were breached in 17 percent of attacks.

Sentiment analysis helps sales teams measure customer reaction
One of the problems sales teams face is knowing how their pitches, presentations and marketing materials are perceived by the customer.
Cloud-based sales and content management platform Pitcher is hoping to offer teams better insight with its newly patented Sentiment Analysis Module (SAM).

Deutsche Telekom hack affects 900,000 customers
German telecommunications giant and T-Mobile parent company Deutsche Telekom was the victim of a cyber-attack over the weekend, which left some 900,000 users affected, the company confirms in a blog post.
This weekend, a hacker (or more likely, hackers) infiltrated the company, and tried to infect users' home routers with malware. Deutsche Telekom said its network was not affected "at any time".

It is terrifyingly easy to bypass BitLocker in Windows 10
The BitLocker feature of Windows is supposed to offer a degree of peace of mind that files are going to be secure -- but one expert points out that a simple key combo is all it takes to bypass the security feature.
A bug has been discovered in the way Windows 10 handles a Feature Update -- the installation of a new build of the operating system. By taking advantage of the bug, it is possible to access a Command Prompt and gain unrestricted access to the contents of the hard drive.

Mitigating the risks of third-party access to your data
If your office was broken into, you would fear what the intruders might take. Being so concerned about the possibility, you fit all the right locks and alarms and have good door and window security. However, do all the service providers that access your office do the same? If they’re not as security conscious, and they get broken into, the intruders could get hold of the access card or key to your office and then they’re in.
It would be galling because, despite having done all the right things to protect your company’s assets, your defenses were still breached. There was a weakness but it wasn’t your security. You gave a vendor the means to access your business to do you a service, and that access was exploited by someone with the skills to take advantage of their weak security.

The Snooper's Charter is now law, giving the UK some of the most extensive, invasive and draconian web surveillance powers in the world
The Investigatory Powers Act 2016, the Snooper's Charter, legalized spying: call it what you will, the UK now officially has some of the most extreme internet surveillance powers in the world. The Investigatory Powers Bill was today given royal assent, meaning it has now passed into law.
Unsurprisingly, there have been huge protests from privacy groups, and an online petition against the new powers has already gained more than 136,000 signatures. The Investigatory Powers Act 2016 not only requires ISPs to store records of their customers' browsing history, but also make this data available to dozens of government agencies, and even permits state hacking of phones and computers.

Sophisticated social engineering attacks target hotel chains
In the run up to one of the hospitality industry's busiest periods, cyber criminals are targeting hotel chains with a series of targeted attacks.
Cyber security company Trustwave has investigated the attacks, which combine social engineering with sophisticated malware, against a number of its clients in the past month.

Two factor authentication is not enough
The general consensus appears to be that two-factor authentication (2FA) is the answer to our authentication needs. Be that from usage of consumer sites in our personal lives or as part of our daily requirements when signing into enterprise infrastructure and applications at work.
However the cyber-attack on Three's customer upgrade database is yet another example of how 2FA is not enough. Organizations must move away from relying solely on usernames and passwords, as once again access was gained with a stolen employee login.

Cold War 2.0: Russia is borrowing the Great Firewall of China to implement greater state censorship and control
The Great Firewall of China is a famous tool of censorship and state control of the internet -- and Russia wants to throw up its own version of the web filtering system. Russia already operates the so-called 'red web' which is used to not only monitor what Russian citizens are up to online, but also implementing blocks and filters such as the recent ban on LinkedIn.
But now President Putin wants to step things up a notch. Russia and China have become close allies in recent years, particularly in the field of state control of the internet, and there are plans to roll out even greater controls over what web users are able to do and access online, ostensibly from fears of an uprising against the government.

UK businesses unprepared for virtualization security challenges
For UK companies with at least 1,000 PCs, virtualization is a "strategic priority", however, they are yet unprepared for all the different security challenges this approach brings. This is according to a new report by Bitdefender.
Surveying 153 IT decision makers in the UK, working in such companies, the report says hybrid infrastructures are the major common architecture in enterprise environments, as CIOs all over the world being to increasingly adopt them. The report sheds some light on the biggest fears and concerns IT decision makers have with the new infrastructure approach.

Security tips for 2017
In an increasingly digital world, criminals have the information and the means to ensure that high profile security breaches, involving major household names, continue to make the headlines.
As technology evolves, so do the threats being developed by hackers who have a whole host of motivations for wanting to disrupt businesses of all sizes. It’s a constant battle but thankfully one that has resulted in increasingly sophisticated security tools coming to the market.

If you're going to San Francisco be sure to travel free with ransomware
The Muni public transport system in San Francisco has been hit by a major ransomware attack over the weekend that left the network having to give passengers free travel.
It's estimated that around 2,000 systems have been affected by the attack, which began on Friday, including ticket machines, servers and Windows workstations.