
LastPass is now available for free on smartphones, tablets and PCs
If you have considered LastPass in the past and deemed it too expensive it is now time to take another look at the popular service, as the password manager is finally offered for free across all types of devices it supports -- PCs, tablets and smartphones. Gone are the annoying limitations of before.
Previously, users who wanted to take advantage of the LastPass free plan were limited to syncing passwords only between devices of the same type -- for instance, only PCs. This was not only impractical, as few of us use only smartphones or PCs, but also a serious reason to give up on LastPass -- or free password managers altogether, for that matter. The move to a completely free LastPass is a big change in the right direction, however.

Off-the-shelf Android spyware targets high level executives
The increasing commoditization of malware means that you no longer need to be a technical expert to launch an attack. You can simply buy the tools off the shelf.
Researchers at Skycure Research Labs have uncovered just such an off-the-peg spyware attack targeting senior company executives.

Kaspersky tells ransomware victims not to pay up
If your organization ever gets infected by ransomware (and there are good chances it will) it is better not to pay up because you probably won’t get your data back, even if you do pay the ransom.
This is according to a new report by security firm Kaspersky Lab, which urges organizations to instead report the incident to the authorities. It bases its conclusions on a couple of research results -- more than a third (36 percent) of organizations pay the ransom, but around 20 percent still don’t get their files back.

Datto launches new ransomware protection for SMBs
We already know that ransomware is a lucrative business for the attackers. But for the victims, especially smaller businesses, it can prove devastating.
A new solution offering enterprise-class ransomware protection for small and mid sized companies is being launched by data protection specialist Datto. In the event of an attack it aims to shorten downtime, save money and reduce the impact to business, giving companies an effective and reliable alternative to paying hackers' ransoms.

New platform improves accuracy of behavioral attack detection
As cyber attacks get more sophisticated, so being able to spot them requires a different approach from simply looking for signatures.
Behavioral detection company LightCyber is launching a new version of its Magna platform that increases the precision and speed of detecting an in-progress attack from either a malicious insider or external bad actor.

Mozilla pulls Battery Status API from Firefox over privacy concerns
It was supposed to be a feature that allowed more efficient versions of websites to be delivered to people running out of battery power.
But the Battery Status API built into Firefox was also found to be problematic from a privacy point of view after it was discovered that visitors' battery levels could be used to track them online. In response to this the API is being pulled from Firefox.

Microsoft: Russian hackers are exploiting Windows flaw exposed by Google
Microsoft says that a vulnerability in Windows made public by Google has been exploited by a hacking group with links to Russia. The group -- known variously as Strontium, Fancy Bear, and APT 28 -- has executed several spear phishing attacks, the company says.
Google was criticized for publicizing the vulnerability before Microsoft has released a patch. A fix for the security hole is not due to be released until Tuesday, 8 November -- voting day in the US election.

Samsung's Note7 exchange booths: Could users' old data be exposed?
When it comes to the exploding batteries on Galaxy Note7 models, Samsung has been lauded for its crisis management approach and how it’s accepted responsibility for the problem. Now setting up exchange booths at airports around the world so users can exchange their Galaxy Note7 phones is yet another example of its exceptional crisis management approach.
But while it’s commendable how swiftly Samsung is taking action to replace the faulty handsets, the company has left one crucial component out of this plan. That is, erasing the data from those Galaxy Note7 devices that are turned in at its exchange booths at airports around the world. There’s no mention of whether the data is being securely and permanently erased from the Galaxy Note7 phones that are taken back at the exchange booths -- and if it’s being done so before they’re handed off to Samsung’s chosen recyclers.
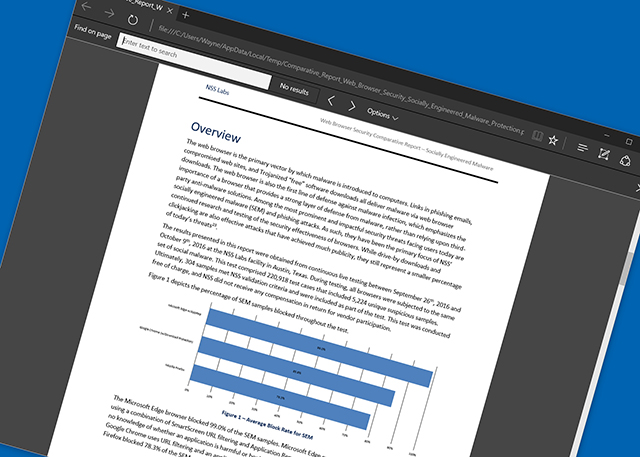
Microsoft Edge is way more secure than Chrome and Firefox
While Microsoft Edge might be a little lacking in features, compared to more established browsers like Chrome and Firefox, one area where it is better than its rivals is security.
That’s according to NSS Labs which today announced the results of its latest Web Browser Security comparative test. The test pitted Chrome, Firefox and -- for the first time -- Edge against each other to see how effective the browsers are at protecting against threats.

Google demos how neural networks can encrypt communications
In an effort to demonstrate how AI could be used to boost encryption, researchers at Google taught two neural networks how to communicate with one another while keeping their conversation secret from a third.
Researchers at the company's deep learning initiative, Google Brain, have successfully taught two neural networks, given the nicknames "Alice" and "Bob", to secretly communicate with one another while keeping the details of their conversations hidden from one called "Eve". Last week, the team behind this endeavor published a paper detailing the process of the experiment and its results.

AdWords malvertising targets macOS users
Researchers at threat prevention company Cylance have discovered a malvertising campaign on Google AdWords for the search term "Google Chrome", where unsuspecting macOS users were being tricked into downloading a malicious installer.
The installer, identified as "OSX/InstallMiez" (or "OSX/InstallCore"), ultimately downloads a malicious file named "FLVPlayer.dmg". The malware hash changes on each download, making it difficult to detect and track.

British empire strikes back with new cyber security strategy backed by £1.9 billion investment
The UK government has today launched a new National Cyber Security Strategy, setting out decisive action to protect the nation's economy and the privacy of British citizens, and strike back against attackers, while encouraging industry to up its game to prevent damaging cyber-attacks.
The strategy sets out how the UK will use automated defenses to safeguard citizens and businesses against growing cyber threats, support the UK's growing cyber security industry, develop a world-class cyber workforce, and deter cyber-attacks from criminals and hostile actors.

Enterprises put themselves at risk by running outdated Microsoft products
According to a new report 65 percent of Windows systems are still running Windows 7, and a small percentage of devices are still running Windows XP.
The survey from trusted access specialist Duo Security analyzed more than two million endpoints and found 63 percent of them running Microsoft operating systems. Yet only 24 percent are running Windows 10. Windows 7 remains the most popular despite there being over 600 vulnerabilities affecting unpatched versions.

70 percent of organizations are swamped by threat data
New research from threat intelligence platform Anomali and the Ponemon Institute shows that 70 percent of security industry professionals believe threat intelligence is often too big and/or complex to provide actionable insights.
It also shows that they often fail to share essential threat data with board members and C-level executives, despite the fact that security is now a business priority.

Number of DDoS attacks down but speed and size increases
The number of DDoS attacks fell more than 40 percent to 97,700 attacks in the second quarter of 2016 according to the latest threat report from DDoS security service Nexusguard.
The report reveals there was a sharp dip in distributed reflection denial of service (DrDoS) attacks, with DNS-based attacks falling 97 percent compared to the previous quarter. However, recent DDoS attacks on cybercrime journalist Brian Krebs and OVH, a French internet hosting provider, broke records for speed and size.