
Most smart car vulnerabilities can be easily exploited
Remember that cyber-experiment when a couple of hackers managed to take control over a speeding car in the middle of the highway?
Well, IOActive has published a study, entitled Commonalities in Vehicle Vulnerabilities, after three years of testing, and the results are quite scary.

Data loss and theft is on the rise
There has been a "sharp increase" in the number of lost and stolen corporate data in the past two years, according to a new report by the Ponemon Institute and Varonis Systems. But it’s not as straightforward as you’d think.
The new report, titled Closing Security Gaps to Protect Corporate Data: A Study of U.S. and European Organisations, says that 76 percent of respondents experienced either data loss, or theft, in the past 24 months.

Kaspersky finds advanced cyber-espionage malware that hid for five years
Kaspersky Lab's security researchers have found a new cyber-espionage malware, most likely built by a nation-state to use against other states' organizations.
Dubbed "ProjectSauron", it is "particularly interested" in accessing encrypted communications. The malware hunts such communications down using an "advanced modular cyber-espionage platform", comprised of a number of different and unique tools.

New solution detects enterprise data at risk on shadow IT
Shadow IT is an increasingly major concern for businesses, the use of public cloud services offers convenience for workers but risks confidential information being exposed outside the organisation.
Canadian endpoint security company Absolute is launching new functionality for its Absolute Data and Device Security (DDS) product that detects data at risk on endpoints associated with cloud storage applications.

Google will block Flash in Chrome 53
Following the lead of Apple with Safari in macOS Sierra, and Mozilla with Firefox, Google has announced that Chrome will begin to block Flash content. Starting with Chrome 53 in September, Google will "de-emphasize Flash in favor of HTML5".
Google says that the decision has been made to improve security, performance, and battery life, and it builds on an earlier change that made some Flash content click-to-play rather than loading it by default.

How to hide the Windows Defender icon in Windows 10 Anniversary Update
If you have just upgraded to Windows 10 Anniversary Update, you have possibly noticed the addition of a Windows Defender icon in the notification area. Then again, you may not -- a quick straw poll in the BetaNews newsroom reveals that not everyone is seeing it.
Assuming the icon has suddenly appeared for you, it's possible that you'd rather it vanished. Here's what you need to do if you would like to banish the Windows Defender icon and clean up your notification area.

Google can already protect most Android phones from the QuadRooter threat
The discovery of QuadRooter is one of the biggest security threats to Android users since Stagefright. Security firm Check Point Software has released a tool to help people determine if their phones are at risk, but Google says that it is already able to block apps with the QuadRooter exploit.
The Verify Apps feature of Google Play Services is able to detect and block any apps that feature QuadRooter. As the exploit has to be delivered via an app, this effectively protects the vast majority of handsets that are threatened.

Adware and Pay-Per-Install software deals rake in big money
After a yearlong study into 'unwanted software' Google has published a report that shows that there is a good deal of money to be made out of bolting crapware onto software installers. The authors suggest that unwanted software is a problem that affects three times as many people as malware, making it an incredibly lucrative business.
The paper, entitled "Investigating Commercial Pay-Per-Install and the Distribution of Unwanted Software", is a joint venture between Google and New York University and it reveals the techniques used by developers to evade detection. It also found that Pay-Per-Install (PPI) methods are used to deliver not only harmless unwanted software, but also malware.

Adding Linux Bash to Windows 10 Anniversary Update could be a huge security risk
The arrival of Linux in Windows 10 caused ripples of excitement in certain circles. But as well as making it possible to run GUI Linux apps on the desktop, there are also concerns that there are security risks associated with having the Bash feature from Linux available in Windows 10 Anniversary Update.
Speaking at the Black Hat USA security conference, Alex Ionescu from Crowdstrike said that he had reported some concerns to Microsoft during the testing period of Windows 10. While some of the issues he raised have been addressed, he says that the presence of Linux represents a "new potential attack surface" that users need to be aware of.
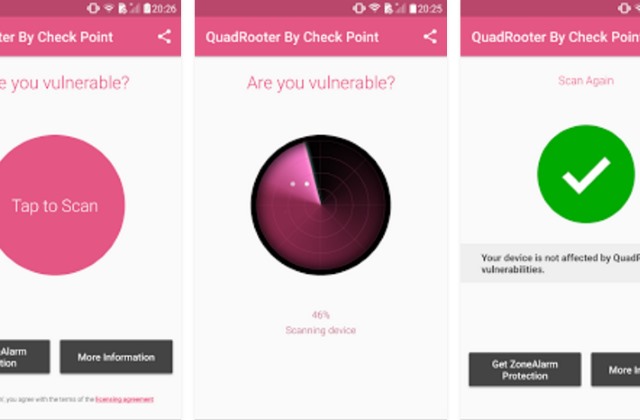
Check if your phone is at risk from QuadRooter vulnerability
The latest vulnerability for Android handsets is QuadRooter, and there are an estimated 900 million devices at risk. Just shy of a billion phones and tablets is undeniably a lot, but how can you know if you are affected?
While a list of devices that are definitely affected has been published, it is far from exhaustive. Thankfully the good folk at Check Point Software have put together a special app that will test your phone or tablet and let you know the risk.

Apple finally announces a bug bounty program of its own -- but it's not open to everyone
Bug bounty programs have become commonplace in recent years. Tech companies offer up rewards to coders, engineers and hackers who manage to unearth security vulnerabilities in software, and this means that problems are detected and patched faster than normal.
It is something that the likes of Google and Microsoft have offered for some time, and now Apple has decided it wants a piece of the action as well. Starting in September, the company will pay out up to $200,000 to anyone identifying vulnerabilities in its software and services.

'QuadRooter' vulnerability affects 900 million Android devices -- the sky is falling!
As a Linux desktop user, you'd think I'd be a big Android proponent. Actually, I rather detest Google's mobile operating system lately. Other than Nexus devices, most Android devices fail to get regular updates, leaving users exposed to vulnerabilities. That is unacceptable! It is why I own an iPhone now, but I digress.
Sadly, yet another set of vulnerabilities have been discovered for Android. Dubbed 'QuadRooter', all Qualcomm devices are affected. In other words, this is really, really, bad, folks. You see, 900 million phones and tablets are impacted, and most of them will probably never be patched. The Android sky is falling!

Google Compute Engine lets users create their own encryption keys
Until now, anyone using the Google cloud platform, Google Compute Engine, was forced to use encryption keys generated by Google. Clearly this spooked a lot of people, and there have long been calls for users to be granted greater control of security.
Now this is happening -- users are able to provide their own encryption keys. Customer-Supplied Encryption Key (CSEK) are used to provide a second layer of security, on top of the Google-generated keys that are used by default.

Why Ashley Madison's 'oh no' data breach didn't scare new users away
There once was a time when most people hadn’t heard of casual dating site Ashley Madison. That all changed in July 2015, when hackers stole sensitive customer information and posted the information on the dark web in a massive data dump, 9.7 gigabytes in size. The files included account details and logins for approximately 32 million of the dating site’s users.
One year later, the dating site is doing several things to redeem its damaged reputation, including rebranding its parent company from Avid Life Media to Ruby, bringing in a new CEO and President to lead the business, revamping their value proposition and launching their first-ever TV ad.

Application control is a solid defense against ransomware
Application control, such as greylisting, paired with selective local admin rights management, is 100 percent effective against ransomware and unwanted file encryption.
This is according to CyberArk Labs’ new report, based on the analysis of more than 23,000 real-world samples from common ransomware families, such as Cryptolocker, Petya and Locky. More than 30 different malware families were tested, and the results posted in the report entitled Analyzing Ransomware and Potential Mitigation Strategies.