
OpenYOLO API project set to enhance user security and make login easier
Google and online identity and password management company Dashlane are announcing the upcoming launch of a new, open-source API project to enhance user security.
The collaboration between Dashlane and Google, plus other leading password managers, will develop OpenYOLO (You Only Login Once), an open API that will enable app developers to access passwords stored in password managers to easily and securely log users into their Android applications.

New solution lets enterprises transfer sensitive data securely
Businesses in industries like healthcare, financial services, insurance, retail and government hold sensitive data and need to be able to keep it safe at all times.
Compliance with regulations like PCI and HIPAA often requires new layers of security between the public internet and protected data. Network management software company Ipswitch is tackling this with the launch of Ipswitch MOVEit 2016.

HTTP/2 has four huge security vulnerabilities
The HTTP/2 standard was approved some time ago, but it is yet to be widely adopted. Before the standard can become widespread, however, there are four serious vulnerabilities that need to be addressed.
The high-profile issues were revealed at Black Hat USA 2016 by Imperva researchers. They found that exploits similar to those that work on HTTP/1.x also work on the HTTP/2 protocol. The problems specifically affect server implementations from Apache, Microsoft, NGINX, Jetty, and nghttp2, but it is likely that other implementations are also at risk.

How Pokémon Go could be putting corporate data at risk
The privacy implications of the Pokémon Go craze have already had plenty of publicity, but according to a report from cloud security specialist CloudLock employees are granting access to corporate environments, despite these warnings, and are potentially opening backdoors to their organization's most sensitive databases via the app.
CloudLock analyzed more than 900 corporate environments and found that 44 percent of all organizations have employees who have granted access to Pokémon Go using their corporate credentials.

Almost 40 percent of enterprises hit by ransomware in the last year
Ransomware is one of the biggest security threats that organizations face. New research from malware prevention and removal specialist Malwarebytes across the US, Canada, UK and Germany and finds that nearly 40 percent of businesses have experienced a ransomware attack in the last year.
The study conducted by Osterman Research also reveals that of those that have fallen victim more than a third lost revenue and 20 percent had to stop business completely.

New malware campaign avoids detection to target major financial brands
Updated versions of the Gozi malware are being used in currently active campaigns targeting global financial brands according to threat intelligence experts buguroo Labs.
Targets of the attack include PayPal, CitiDirect BE, ING Bank, Société Générale, BNP Paribas, and the Bank of Tokyo. It's expected that attacks currently being perfected in Poland, Japan and Spain, will soon be launched in the US and Western Europe.

Most enterprises lag behind in mobile security
Enterprises are still not doing enough to protect corporate data on their employee’s mobile apps and devices from cyber threats, according to a new report from MobileIron.
According to the Mobile Security and Risk Review report for Q2 2016, less than five percent of enterprises are using mobile threat detection software and only eight percent have an enforced operating system update policy in place.

$72 million Bitcoin theft from Bitfinex exchange causes cryptocurrency price plunge
The theft of 119,756 Bitcoin from the Bitfinex exchange has seen the price of the cryptocurrency plummet by 23 percent. In what has been described as the second biggest Bitcoin theft after MtGox, $72 million worth of Bitcoins vanished from user's accounts.
It seems that Bitfinex suffered a massive security breach when it was hit by hackers who started to filter money out of segregated wallets. Despite the hack, the exchange says that this incident doesn’t "expose any weaknesses in the security of a blockchain".

Cyber security is not a priority for most UK businesses
Despite the constant warnings experts keep giving out to businesses concerning cyber-security, UK’s firms won’t be prioritizing it in the next 12 months.
This is according to a new quarterly survey by Close Brothers. Its key takeaway is that 63 percent of companies decided not to invest in better security, while the other 37 percent decided to do so.

CheckPoint launches real-time zero day browser protection
The most common way for malware to get onto a PC is via files downloaded from the web. According to Exploits at the Endpoint: SANS 2016 Threat Landscape Study, 41 percent of people suffered their worst security events from drive by downloads and 80 percent suffered phishing attacks.
Threat protection specialist CheckPoint is launching a new anti-malware and anti-phishing extension for web browsers to address this growth in web-based malware and social engineering attacks.

New subscription service offers flexible threat intelligence
Depending on their size and the sector they operate in, businesses need to respond to threats of different types and require intelligence to suit.
Endpoint protection specialist CrowdStrike is launching a tiered eCrime subscription that will allow customers to choose the option that best meets their needs to gain new capabilities and insights into the entire eCrime adversary ecosystem, and orchestrate detection and response options in a more effective manner.

New security solution offers anytime, anywhere user protection
As growing numbers of devices are connected to the internet, security and privacy concerns grow. Businesses are looking for solutions that provide protection for both the endpoint and the network.
Israel-based Allot Communications is announcing a new collaboration with Intel Security to introduce McAfee Unified Security Powered by Allot, providing complete end-to-end security capabilities.

The rise of the Linux botnet
A new report from Kaspersky Lab on botnet-assisted DDoS attacks shows a steady growth in their numbers the second quarter of this year.
SYN DDoS, TCP DDoS and HTTP DDoS remained the most common attack scenarios, but the proportion of attacks using the SYN DDoS method increased 1.4 times compared to the previous quarter and accounted for 76 percent.
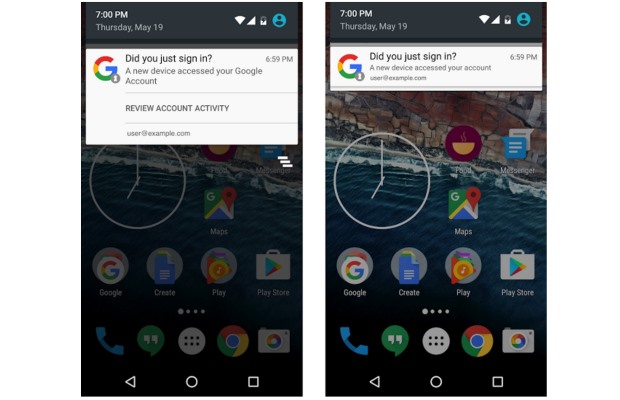
Google rolls out native notifications to Android users when new devices sign into their accounts
Google continues to take steps to improve the security of Android, and the latest addition starts to roll out today. Lengthily referred to as "Android notifications for newly added devices", the feature does exactly what you would expect it to do.
Whenever a new device is added to an account, a native Android notification will appear. This gives users the opportunity to review the device and determine whether it is something suspicious.

Arxan guards against application layer threats
Cyber attacks are increasingly happening at the mobile and IoT application layer. This allows hackers to bypass server-level security and go straight for the binary code, to steal IP, credentials and other sensitive information.
Attack prevention company Arxan Technologies is launching new features to help guard against this type of threat. These include new and enhanced support for major operating systems and languages, including QNX (a subsidiary of Blackberry) and Apple's Swift programming language, as well as new white-box cryptographic schemes including SHA-3.