
More than half of companies fail to protect privileged credentials
Details of privileged accounts represent a major prize for hackers because they unlock the access required to exploit virtually any part of an organization's network and data. Yet according to a new report many companies are failing to adequately protect them.
The study by privileged account management (PAM) specialist Thycotic and research firm Cybersecurity Ventures benchmarked the PAM performance of more than 550 organizations and found that 52 percent received a failing grade.

Shadow IT responsible for cyber attacks
Shadow IT has always been considered a huge risk to an enterprise’s cyber-security efforts, but now we have a new survey which supports the claim and shows the scope of the problem.
The report, recently released by Tenable Network Security, says that both German and UK-based companies acknowledged shadow IT as a problem, but the former reported more cyber-attacks.

CryptoDrop can stop ransomware early on in the encryption phase
New software, designed by scientists at the University of Florida (UF), just might be the answer to thwarting the ever-growing problem of ransomware.
Ransomware is a form of malware used by cybercriminals to exploit users into paying significant sums of money to retrieve their own files. When an infection happens, the files on a user’s system are encrypted by the virus and the only way to regain access to those files is by paying a ransom to the hackers behind the attack.
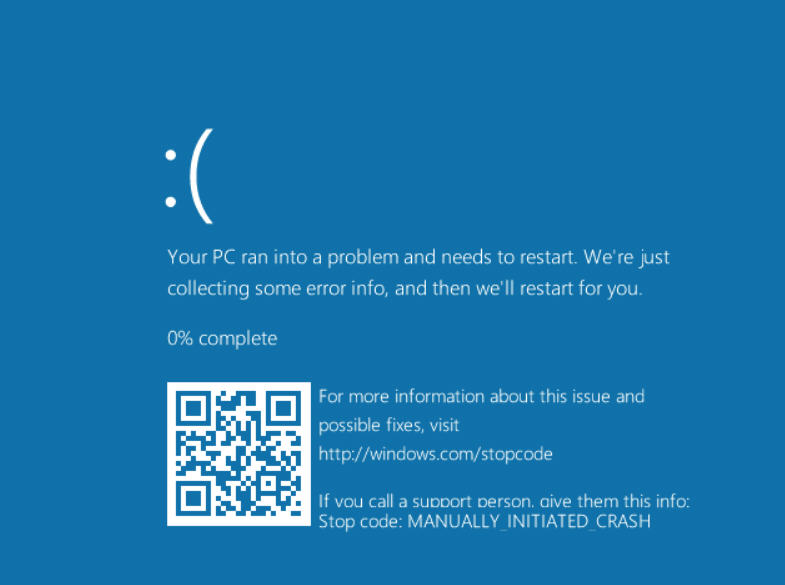
Windows 10 Anniversary Update's new Blue Screen QR codes could put your smartphone at serious risk
PCs can go wrong in all sorts of ways, and the problems can manifest themselves in the form of slowdowns, freezes, or worse. Occasionally, you might encounter a blue screen of death (BSOD), accompanied by a usually pretty cryptic message outlining the cause of the crash.
In the soon-to-be released Windows 10 Anniversary Update, Microsoft has given the blue screen a makeover, introducing QR codes to make it easier for anyone to troubleshoot the problems they encounter. It’s a helpful change, but Panda Security warns it could actually be a godsend to cybercriminals, and result in users having personal details stolen, and smartphones getting infected with drive-by malware.

CEO fraud scams target more than 400 businesses every day
More than 400 businesses get targeted by CEO fraud scams every day, a new report by security researchers Symantec says. CEO fraud is a type of scam in which cyber-criminals target financial staff, often posing as CEOs or other executives, and request large money transfers.
Even though it sounds too simple to work, its success rate is actually quite high, and relies mostly on putting financial staff under a lot of pressure through a sense of urgency, not giving them enough time to think things through.

Enterprises leave vulnerable industrial control systems exposed online
Industrial control systems (ICS) are not supposed to be connected to the Internet, Kaspersky Lab says, as it opens a sea of opportunities for hackers. Such systems are run by energy, transportation, aerospace, oil and gas, chemicals, automotive and manufacturing, food and drink, governmental, financial and medical institutions, and should be, for the sake of security, run in a physically isolated environment.
However, Kaspersky Lab says that is not the case, and that it has found 13,698 ICS hosts exposed to the Internet, which very likely belong to large organizations. More than nine in ten (91.1 percent) host remotely-exploitable vulnerabilities, and 3.3 percent contain "critical and remotely executable vulnerabilities".

New self-phishing tool helps companies measure attack risks
Protecting against data breaches is always better than dealing with their aftermath. And since phishing is still one of the most popular attack methods businesses and employees need to be alert to the risks.
Authentication specialist Duo Security is launching a new, free tool to let IT teams run internal phishing simulations and assess their vulnerability to such attacks.

Malware attack targets European energy companies
The Labs team at malware protection company SentinelOne has discovered a sophisticated malware campaign that's specifically targeting at least one European energy company.
The malware, called SFG, is the mother ship of an earlier malware sample called Furtim, which targets the industrial automation control systems with sophisticated malware and acts as dropper to deliver a payload which could be used to extract data or potentially shut down the energy grid.

The Halvening means that bitcoin mining rewards just dropped by 50 percent
It just became significantly harder to mine Bitcoins. The halving event rolled around yesterday, July 9, and means that the reward for mining just dropped by 50 percent. The cryptocurrency is generated by machines around the world 'mining' for new bitcoins.
Rewards of bitcoins are handed out for giving over computing power to process bitcoin transactions. It's a very, very slow way to make money -- and it just got a whole lot slower. While there were previously 25 bitcoins (around $16,000) available globally to miners every 10 minutes, the figure is now just 12.5 bitcoins. But what does this mean for the digital currency?
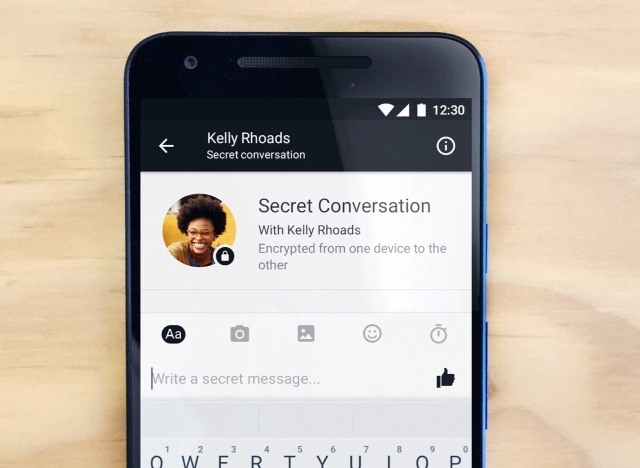
Facebook Messenger ups security with end-to-end encryption in 'secret conversations'
Continuing in its relentless drive to take over the world of messaging, Facebook Messenger is gaining end-to-end encryption. To start with, the security feature is only rolling out on a 'limited test basis' but if feedback is positive, it will get a wider airing.
Facebook says that the move comes in response to requests for additional security options to protect discussions about sensitive matters, saying that security and privacy experts have been involved in the implementation of the feature.

Court papers show Silent Circle's privacy-boosting Blackphone was an unmitigated sales disaster
With so much focus now placed on privacy and security, you would have thought that the Blackphone from Silent Circle would have been a roaring success. But documents from a court case with former partner Geeksphone reveal that there have been just a handful of sales, and revenue is hundreds of millions of dollars lower than expected.
Silent Circle found itself in court after Geeksphone complained that it had not received a $5 million payment agreed as part of a buyout. Geeksphone had helped to build the original Blackphone, and Silent Circle went on to buy the Spanish company's share before launching the Blackphone 2. But sales were much, much lower than expected, leading the company to describe its hardware business to "be a significant financial drain".

Government IT pros overconfident about detecting insider threats
Federal government IT professionals are overconfident in their ability to detect insider threats, endpoint security firm Tripwire has found. Analyzing the confidence of IT experts regarding their efficiency in seven key security controls, it polled 763 professionals from various industries.
Almost a third say they would not be able to detect every time a non-privileged user attempted to access files. Almost three quarters (73 percent) assume their system would generate an alert or email within hours if a user inappropriately accessed file shares.

New security tool addresses Android app collusion threat
As we reported last month app collusion, where apps work together to extract sensitive data, now represents a very real security risk to mobile devices.
To address this emerging threat, component technology firm Formaltech, today is releasing FUSE, a DARPA-funded tool that detects inter-application collusion and other vulnerabilities in Android apps.

90 percent of security events are caused by bots
Bots account for 49 percent of all internet traffic, most of which is from malicious 'bad bots' according to website security company Incapsula.
Of course there are good bots too, such as the crawlers used by major search engines, but according to Incapsula’s figures 90 percent of all security events are caused by bots, and 66 percent of all bot activity is malicious.
Avast to acquire antivirus rival AVG for $1.3BN
Although Avast and AVG both offer paid security tools, they are best known for their free antivirus software.
Some people confuse the two firms because of the similarity of what they do, and the fact their names begin with the same letters, they were founded at around the same time, and originated in the Czech Republic, but that confusion soon won’t be an issue as today Avast announces it is set to acquire AVG.