
Feedly kills URL shortener to improve speed, security, and privacy
Back in January feedly -- the RSS reader that tried to fill the gap left by the death of Google Reader -- introduced a URL shortener. At the time it was billed as a "captur[ing] analytics about how people are engaging with the content you are sharing". Ten months later, the news service realized that this could be seen as being overly intrusive and has killed the tool.
The original blog post that heralded the launch of feedly.com/e has been updated to reflect the fact that the shortener is no more. "With hindsight this was a bad idea. We focused too much on feedly's growth versus doing what is right for users and for the Web. Sorry".

How to defeat network zombies this Halloween
Zombies are a staple of the horror film industry despite being absurdly ill-equipped to play the role of a predatory force unleashing Armageddon on the human race. They're embarrassingly slow and brainless, for starters. They have terrible personal hygiene, can't operate machinery of any kind, they can't drive and they even don't know how to use a computer or a smartphone. As if that wasn't bad enough, no one has properly explained why some people they kill become zombies and others are completely gobbled up.
Network zombies, on the other hand, are an all too real menace for the modern-day IT administrator. They are smarter than the average zombie, impossible to predict because they appear randomly without warning and dangerous because they cause downtime and lost productivity. Without the right approach, they are nearly impossible to locate and kill.

Breach detection market expected to exceed $1.3 billion by 2018
Security breaches have become a major worry for businesses in the last two years and that's reflected in strong growth of the market for breach detection products.
A new market intelligence brief by NSS Labs looks at the rapid rise of breach detection systems (BDS). In 2013 the BDS market was worth over $289 million dollars, up 99 percent over the previous year.

Apple Pay rival CurrentC hacked -- email addresses stolen
Yesterday, Ed Oswald wrote a story about the retailer-backed payment network CurrentC, describing it as a threat to iPhone and Android users alike. In the article he spoke about the security of the system, saying "CurrentC is overly complicated, and just leaves too many opportunities for something to go wrong, or a hacker to make their way in".
He turns out to have been spot on, as today MCX admits its service has already been hacked, with email addresses of participants in the pilot program and other interested individuals being stolen. Hardly the most auspicious of starts. The following email was sent to those affected:

How mobile users think and behave online
The lines between business and personal mobile use are blurring as the way consumers use their devices becomes increasingly diverse. This is leading mobile users everywhere toward an always-connected existence, dominated by mobile devices, and where brands must work even harder to meet their visitors' needs.
With this in mind, Netbiscuits recently conducted a survey of more than 6,000 consumers from six countries, asking them for their insights and thoughts around mobile web usage and behavior. Here, Netbiscuits CEO Daniel Weisbeck recaps the top ten findings from the UK, US, Germany, China, India and Brazil.

Europeans love iPhone 6, 6 Plus not so much
Europeans are a conservative bunch when it comes to the form factor of their beloved iPhones, as most of those who purchase one of Apple's new handsets opt for the smaller model. In fact, iPhone 6 is so popular among consumers on the old continent that it outsells the iPhone 6 Plus phablet by a whopping five to one.
The difference in sales is to be expected, given that phablets are still somewhat part of a niche today, and the majority of those who buy iPhone 6 and iPhone 6 Plus -- that would be existing iPhone users -- are more accustomed to less intimidating dimensions, like those of iPhone 6. However, Apple is right to jump on the phablet bandwagon, considering how big of a role such devices are expected to play in smartphone sales just a few years down the road, and the hit iPhone's market share is taking from Android handsets.

How video conferencing helps businesses cut costs
While successful businesses vary wildly in how they operate, one aspect seems to be shared -- an established communication system, both internally and externally. Through this communication infrastructure, high-level leaders can stay connected with corporate leaders, managers, and lower-level employees, allowing for precise instructions, procedures, and overall progress, to be effectively communicated and comprehended by all parties involved.
The problem most businesses encounter is maintaining that line of communication. This is especially true for larger companies with establishments in various locales.

Tor user? Your computer could be infected with malware
Authorities are advising all users of the Tor network to check their computers for malware after it emerged that a Russian hacker has been using the network to spread a powerful virus.
Tor, which began as a secret project from the US Naval Research Laboratory, works by piling up layers of encryption over data, nested like the layers of an onion, which gave the network its original name, The Onion Router (TOR).

Oppo R5 is the thinnest smartphone around at only 4.85mm thick
No one can deny that making handsets thinner and thinner is a persistent trend in the mobile device market. Rarely do we see a new, prominent smartphone or tablet being thicker than its predecessor. Manufacturers love to be able to tout during announcements and in ads just how insanely slim their new products are, like this is a feature that us, consumers, are dying to get. (Sadly, sometimes that may be the only thing that such handsets have got going for them.)
Still, if you are one of those who prefer insanely-thin smartphones, Oppo has just the thing for you. The Chinese manufacturer just unveiled "the slimmest phone in the world", called R5, measuring just 4.85 mm thick. To give you an idea of just how thin it is, it shames Apple's new iPhone 6, which comes in at 6.9 mm thick.

Bring your own security approach protects Azure cloud apps
Securing applications in the cloud can prove a difficult challenge for businesses. Any solution needs to balance protection against accessibility and not harm performance.
Java security specialist Waratek has used the Microsoft TechEd Europe conference in Barcelona to announce an innovative bring your own security (BYOS) approach to the problem called Waratek Locker.

FireFTP is a great FTP/ SFTP client for Firefox
First proposed in its basic form more than 40 years ago, File Transfer Protocol (FTP) is an archaic networking technology which should have been ditched long ago.
Remarkably, though, it’s still useful in some areas -- when accessing your own web server, maybe -- and as a result there’s still a strong demand for FTP clients. Normally this might involve installing something like FileZilla; it’s fast, reliable, packed with features, and a great choice for heavy-duty FTP users.

Keyless cars being targeted by high-tech thieves in London
Thefts of cars that use keyless fobs to gain access are on the rise after criminals gained the ability to hack into the car’s onboard computer and it is causing some luxury car owners to be refused insurance.
The Society of Motor Manufacturers [SMMT] reports that organized crime syndicates have been able to bypass the onboard security by using software only meant for mechanics and start vehicles using the ignition button present in many high end models, such as Range Rovers and BMWs.

Woof! Woof! Puppy Linux reaches version 6.0 -- fetch it now!
Linux is pretty darn awesome when used on super-powerful machines. However, where the kernel really shines is when operating systems leverage it for less powerful computers. In other words, Linux can breathe new life into old computers thanks to lightweight distributions.
One of the most infamous lightweight distros is Puppy Linux. Aw, puppies are cute, right? Sure they are, but so too is the operating system that bears the name. You see, it loads from a CD/DVD or flash drives, but it runs from system RAM, making it quite fast (and secure). Today, Puppy Linux achieves 6.0 release, and you can download it now.

Logitech announces Keys-To-Go Bluetooth keyboard, refreshes cases for iPad Air 2
Some people are fans of movies or books; me? I love computer peripherals. Yeah, its crazy, but PCI cards, keyboards and mice really get my motor running. With that said, I particularly appreciate quality and value. In other words, I like solid build quality and reasonable prices.
It is for these reasons that I am a Logitech fan. Yes, there are other companies that make awesome keyboards and mice too, such as Microsoft, but Logitech tends to have a more diverse product offering. Today, the company announces the all-new Keys-To-Go Bluetooth keyboard, which takes a rather unique design approach to mobile typing. True, a small keyboard is not innovative, but the svelte nature of the design is something to behold.
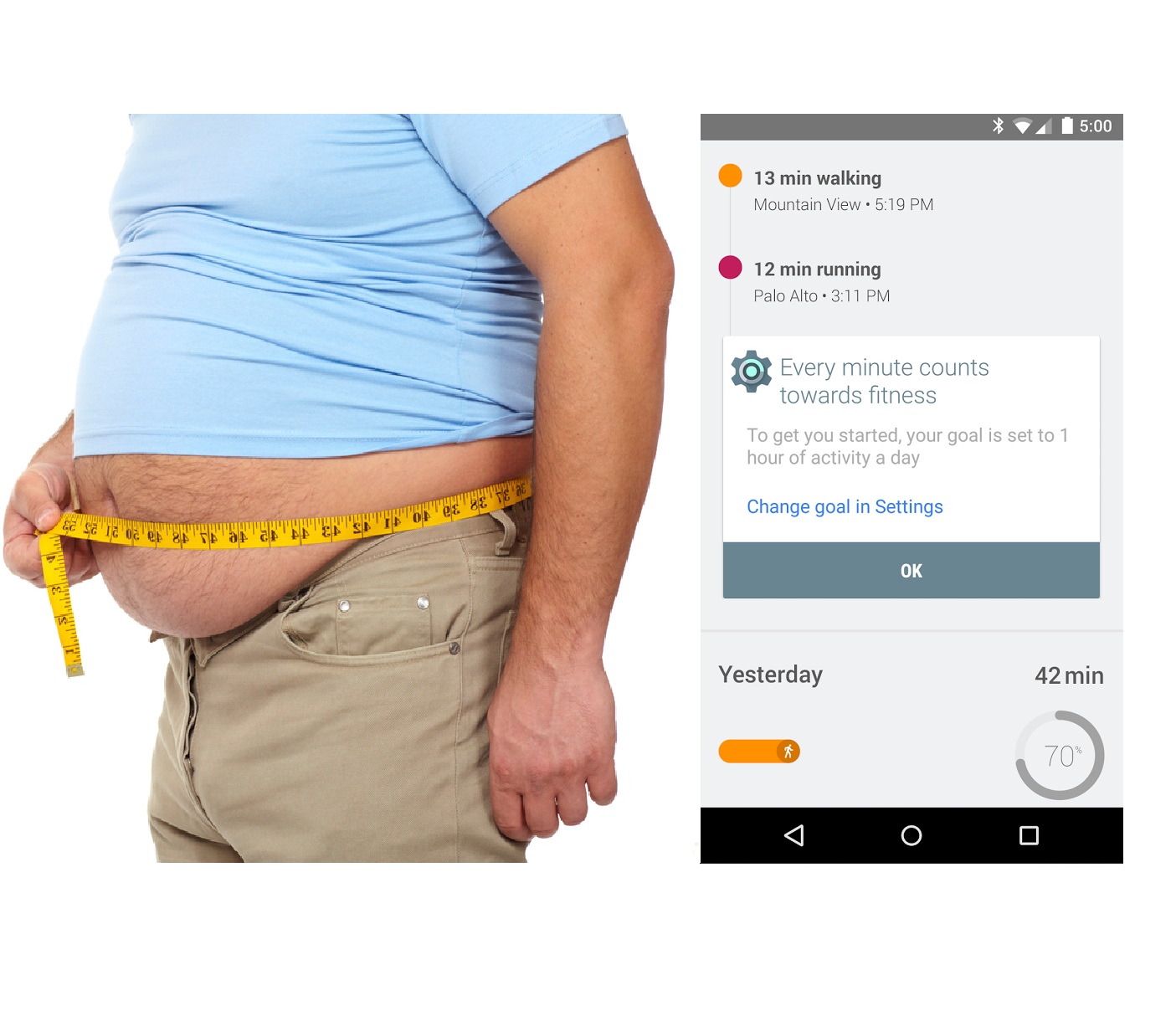
Google wants to get sloppy Android fans off the couch and into shape, releases Fit app
You haven't exercised in a while. It's OK, we know. We can see you getting winded when playing Wii. Who can blame you? I mean, nowadays, there is such incredible technology, that it is hard to be impressed by real life. It is easier to sit on the couch with your precious Nexus 7 watching Law and Order than going for a walk. Hell, maybe you are a Brony and you watch My Little Pony; whatever, it is your life. No judgement. Well, a little judgement -- you are fat and need to get in shape. Your parents are worried about you.
Don't worry, Google is going to motivate you. No, the company is not going to dangle an Inbox invite on a string in front of you and have you chase it around the yard, although that would probably work. Today, the company releases an app called "Fit" that is aimed at getting you off the couch and moving. Sure, it is ironic that technology is being used to motivate sedentary Android fans, since technology has contributed to their lazy ways. But hey, whatever works, right?