
Microsoft warns that Iran is using cyber operations to influence the US 2024 election, just like China and Russia
Every country in the world has a vested interest in the outcome of the US election in November. The choice of either Donald Trump or Kamala Harris will have huge impact around the globe, and there are some countries that are actively engaged in trying to sway voters and influence 2024 US election.
That the likes of Russia and China are engaged in targeting the result of the poll is unsurprising, but Microsoft has issued a warning that Iran is also planning to influence this year's US presidential election. A report from the Microsoft Threat Analysis Center highlights evidence of Iranian cyber-influence operations which have already been running for months.

TUXEDO InfinityFlex 14: The Linux answer to Microsoft Windows 11 convertibles
TUXEDO Computers has unveiled the InfinityFlex 14, a 3-in-1 Linux convertible PC that stands as a compelling alternative to Windows 11 convertible laptops. This device is designed to accommodate various user needs by seamlessly transitioning between a laptop, tablet, and touch monitor.
The InfinityFlex 14 integrates a 14-inch matte touchscreen with a resolution of 1920x1200 pixels in a 16:10 aspect ratio, offering 400 nits of brightness and full sRGB color gamut coverage. It's well-suited for both indoor and outdoor use, featuring MPP 2.0 pen support with 4096 pressure levels for detailed and precise touch inputs.

MSP market turns to providing security solutions
New research suggests that managed service providers (MSPs), which have historically expected to manage IT infrastructure for their customers, are increasingly expected to protect this infrastructure too.
The study from CyberSmart of 250 senior leaders at UK-based MSPs, finds that 65 percent of MSP customers now expect their provider to manage either their cybersecurity infrastructure or both their cybersecurity and IT infrastructure.

Lessons unlearned -- the cybersecurity industry is stuck in the past
People can make mistakes, well-intentioned or otherwise, in any walk of life or industry. It happens all the time.
Take the cybersecurity industry, for example. Just over two weeks ago, the well-publicized Microsoft outage caused by CrowdStrike's corrupted software update wreaked havoc across the world.

Thousands of industrial control devices exposed online
Recent attacks have highlighted the vulnerability of industrial control systems to attack and a new report has found 18,000 exposed devices that are likely used to control industrial systems.
The report, from internet intelligence platform Censys, focuses on ICS devices in the US and UK and also finds that almost 50 percent of the human-machine interfaces associated with water and wastewater systems (WWS) identified could be manipulated without any authentication required.

Keychron launches K2 HE magnetic switch keyboard on Kickstarter
Keychron has introduced the K2 HE through a Kickstarter campaign, a new 75 percent layout magnetic switch keyboard aimed at providing extensive customization. The anticipated delivery for the K2 HE is in October 2024.
With a starting price of $125, the K2 HE expands on the popular Keychron K2 series by incorporating Hall Effect magnetic functions and Gateron Double-rail magnetic switches, which enable precise adjustments to actuation points. This feature is particularly beneficial for users requiring responsive keyboard actions, such as gamers.
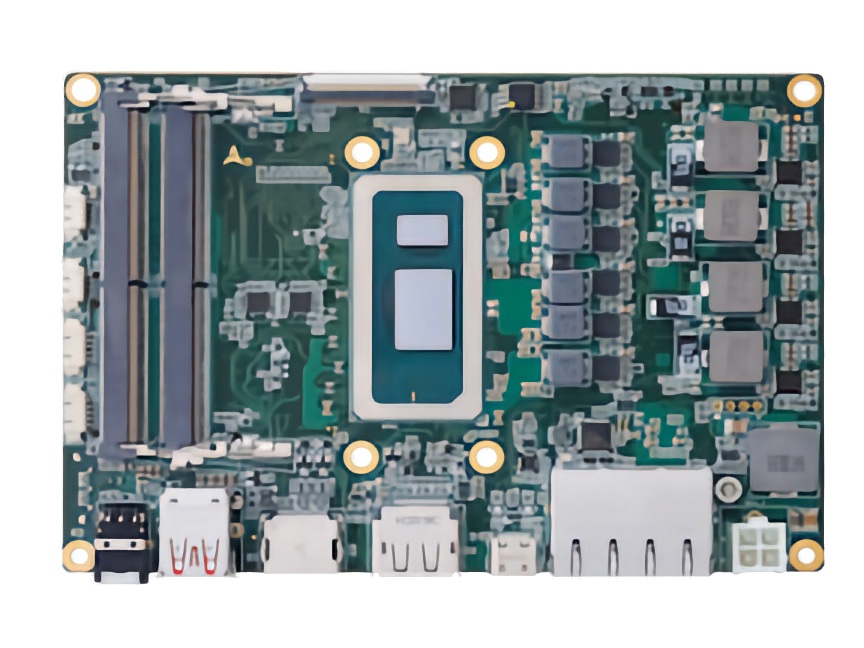
ADLINK introduces SBC35 Series: Compact 3.5-inch single board computers
ADLINK has announced its latest addition, the SBC35 Series of 3.5-inch single board computers (SBC), designed for space-limited environments. This new series comprises two models: the SBC35-RPL, which utilizes the 13th Gen Intel Core processors, and the SBC35-ALN, which features the Intel N97 processor for energy efficiency.
Each model is constructed in a compact 146x102mm form factor, aiming to support diverse applications across automation, transportation, medical industries, and smart city projects. The SBC35-RPL can support up to 64GB DDR5 4800MHz RAM and four independent displays, whereas the SBC35-ALN accommodates up to 16GB RAM and three displays.

Samsung launches new 512GB USB flash drives
Samsung has just enhanced its USB flash drive lineup by introducing 512GB capacities for its BAR Plus and FIT Plus models, and a new USB Type-C option.
The new 512GB versions promise impressive read speeds of up to 400 MB/s and write speeds up to 110 MB/s. This capability allows users to transfer large files such as a 3GB 4K UHD video to a PC in about 10 seconds. The drives are versatile, supporting a broad range of devices through their USB 3.2 Gen1 interface, and are backward compatible with USB 3.0 and USB 2.0. They also support various operating systems including Windows, macOS, and Linux.

Azure outages should spark new urgency for a multi-cloud approach
July 19th 2024 will go down as a tough day for many IT teams, and the day started even worse for businesses using Microsoft Azure and its supported services. In addition to the widely publicized global outage caused by a CrowdStrike update, Microsoft Azure's Central US Region was down for five hours due to an unrelated failure, impacting millions of business users worldwide.
As if that wasn't enough, less than two weeks later, Microsoft Azure experienced another global outage lasting more than six hours. According to the company's service status page, it was Microsoft's 8th service status-related incident.

Switch from Microsoft Windows 11: Nitrux, Linux Mint, and Linux Lite are your new best friends
As Windows 11 continues to face criticism over its system demands and privacy concerns, many users are exploring alternatives. Linux distributions offer compelling options that not only match but often surpass the Windows experience in performance, customization, and security.
Here are the top three Linux distributions that you should consider when switching from Microsoft Windows 11.

CISOs don't feel supported at board level
While CISOs are often responsible for technology implementation, they are not getting the support they need at a strategic level according to a new report.
The study from LevelBlue looks at the dynamics among enterprise C-suite executives to better understand issues that prevent risk reduction, stall or complicate compliance, and create barriers to cyber resilience.

AI is key to innovation but infrastructure and other challenges hold back progress
A new report from Pure Storage finds that the emergence of AI is a key avenue for innovation, but infrastructure issues, talent shortages and energy costs are holding back progress.
Based on a survey of 1,500 global respondents carried out by Vanson Bourne the report finds that although CIOs and other senior IT leaders face significant economic pressures, driving innovation remains imperative for enterprises.

The C-suite conundrum: are senior executives the Achilles' heel of cybersecurity?
In today's digital landscape, an organisation's C-suite and senior executives hold the most valuable corporate data and sign-off authorities, representing the highest potential risk over email. Whether it's inbound spear phishing attacks or outbound mistakes resulting in a damaging data breach, the C-suite are vulnerable.
But what do cybercriminals want from these individuals, are breaches always a result of external actors, and what can organisations do to protect their top decision-makers?

Dealing with digital certificate vulnerabilities [Q&A]
While digital certificates are an essential part of day-to-day security they also present challenges. They can expire or be revoked, or even forged.
We spoke to Bert Kashyap, CEO of passwordless security platform SecureW2, to learn more about certificate-related vulnerabilities and what IT and security teams can do to deal with them effectively.

Devs beware: Apple announces Gatekeeper security enhancements in macOS Sequoia
Working much like Microsoft's Smart App Control tool that is part of Windows, Apple has Gatekeeper for macOS. It is a security feature which is designed to ensure that only trusted software runs on a user's Mac.
In the upcoming macOS Sequoia, Gatekeeper is being updated to help boost security. While this runtime protection change may be welcomed by many, the approach Apple has taken is also likely to irritate some users as it makes it more awkward to run unsigned software.