
81 percent of security pros say phishing is the top threat
A new study finds that that most organizations anticipate phishing (81 percent), malware and ransomware (76 percent), and accidental data loss (63 percent) will be the top security risks over the next six months, followed by social engineering (55 percent) and third-party risks (52 percent).
The report from Fortra looks at the challenges security professionals have faced over the past year, as well as what they plan to focus on next as they continue to embrace digital transformation, new hybrid infrastructures and a challenging security landscape.
Best Windows apps this week
Five-hundred-and-seventy-eight in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Windows 10 is still the leading version of Windows when you compare usage. Microsoft published a video this week that it says helps users switch to Windows 11. It is doubtful that it is going to convince Windows 10 users to make the move, as it is relatively short and without meaningful arguments.

How 5G is set to transform the way businesses connect [Q&A]
The rollout of 5G will speed up mobile communications and also enable more computing tasks to be carried out at the edge.
For businesses it presents the opportunity for a greater understanding of customer patterns and infrastructure needs. We spoke to Chris Gehlen, CEO and co-founder of SaaS/NaaS cloud platform Neutroon, to learn more.

Microsoft Copilot is pushing up base configurations so Windows AI PCs will need at least 16GB of RAM
2024 looks set to be another year dominated by artificial intelligence, and we are now entering the era of the AI PC. This is something that Microsoft is at the forefront of, and the company's Copilot assistant is playing a major role in shaping the future.
A new report from TrendForce reveals something that many people had suspected for some time -- minimum system specifications will be increasing to herald the new computing age. The research company shares the news that "Microsoft has set the baseline for DRAM in AI PCs at 16 GB". But there is more.

Online casino security: How to protect your data
The iGaming industry has made leaps and bounds since the days when online casinos were plagued by terrible graphics and slow interfaces. The massive growth in smartphone technology has filtered down to most major online industries and had an amazing effect on their quality.
There are now countless online casinos to choose from and players have an ever-growing selection of games to choose from. However, the thrill of being able to gamble for real money comes with the ever-present risk of data breaches. Here's how to protect your data while still enjoying your favorite online casinos.

Shokz announces OpenSwim Pro bone conduction headphones for swimmers
Shokz has announced its latest bone conduction headphones -- the OpenSwim Pro. Designed with versatility in mind, the OpenSwim Pro promises a unique audio experience for swimmers and other types of aquatic athletes.
The new headphones feature a flexible Nickel-Titanium alloy frame, combined with a soft silicone material, ensuring a comfortable and secure fit. This design does not interfere with other sports gear such as swimming caps or goggles. The OpenSwim Pro’s standout feature is its ability to seamlessly switch between Bluetooth streaming and MP3 playback through a simple button press or the Shokz app.

2024 cybersecurity predictions: The continued rise of AI and regulation
The last 12 months have been seismic for cybersecurity, with successful hacks and breaches continuing to make front-page news. The task of keeping networks and data safe is an ever-evolving one, with hackers and cybersecurity professionals in a constant state of cat-and-mouse as they try to outsmart one another.
Events of the past year, including the widespread adoption of, and interest in, AI, as well as new geopolitical challenges, have had a profound impact. They provide some clues as to what 2024 might hold.
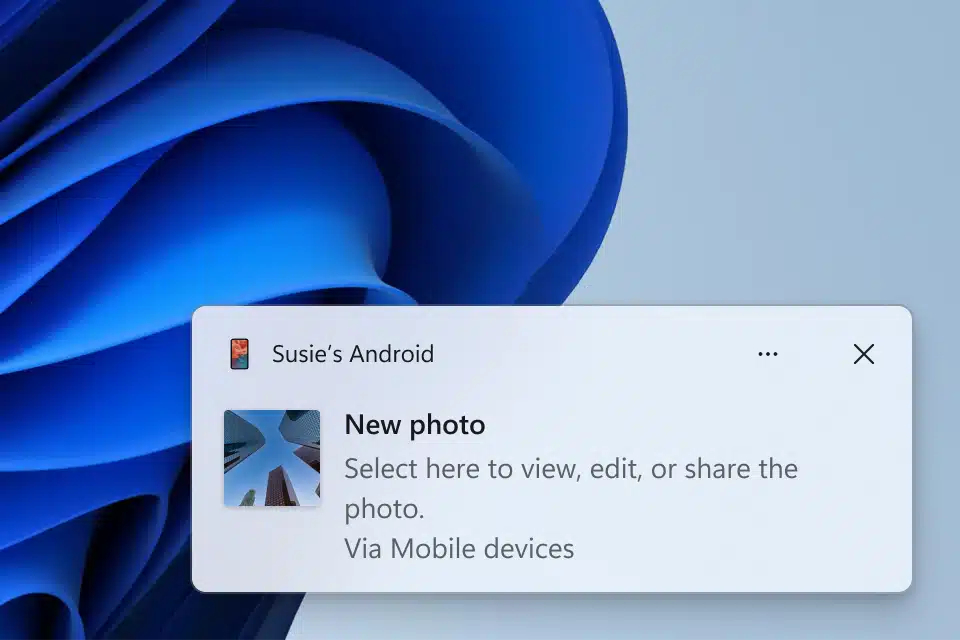
New Windows 11 build lets you immediately access new photos and screenshots from your mobile device
Microsoft is continually adding new features to Windows 11, and today the software giant introduces the ability to access and edit your most recent photos and screenshots from an Android mobile device via Snipping Tool on your PC.
Included in Windows 11 Build 23619 for Insiders in the Dev Channel, the new feature displays notifications on your PC whenever a new photo or screenshot is captured on your Android phone.

Three-quarters of CISOs considering a job change
A new report from IANS Research and recruitment firm Artico Search shows that although 64 percent of CISOs say they are satisfied in their job, 75 percent are open to a change.
More than 660 chief information security officers (CISOs) provided data for the report. Additionally, research team members held conversations with over 100 CISOs to better understand the challenges they face today and the future opportunities.

The future is now: Advancements in biometric security
Originating in the late 19th century, biometrics has come far from its forensic beginnings to become a key player in today's tech landscape. What started as a tool for crime scene investigation now unlocks our phones and customizes our digital interactions.
This article zeroes in on the latest strides in biometric technology, exploring how these innovations shape various industries and our daily lives, while also addressing privacy and accuracy concerns.

Get 'Machine Learning Engineering with Python -- Second Edition' (worth $39.99) for FREE
The Second Edition of Machine Learning Engineering with Python is the practical guide that MLOps and ML engineers need to build solutions to real-world problems.
It will provide you with the skills you need to stay ahead in this rapidly evolving field. The book takes an examples-based approach to help you develop your skills and covers the technical concepts, implementation patterns, and development methodologies you need.

Facebook stalwart Sheryl Sandberg to leave Meta's board of directors but will continue to serve as an adviser
Meta's former COO, Sheryl Sandberg, is stepping down from the company's board of directors later in the year. She has played a major role at the firm since joining Facebook when it was merely a startup, having previously spent time at Google.
Widely respected and seen as one of the most influential women in the world of technology, Sandberg served as Facebook's and Meta's COO for over 14 years and has agreed to remain a board member to help with the transition when she leaves the position. In a message posted to her Facebook page she says that "this feels like the right time to step away".

Apple Hongdae set to open in Seoul, South Korea -- the 100th Apple Store in the Asia-Pacific region
Apple is set to inaugurate its latest store, Apple Hongdae, in Seoul this Saturday, January 20, marking a significant milestone as the 100th Apple Store in the Asia-Pacific region. The store, staffed with nearly 100 experts, offers an extensive range of products including the latest iPhone 15 lineup, new Macs with M3 chips, the Apple Watch series, and the Lunar New Year special-edition AirPods Pro.
Deirdre O’Brien, Apple’s senior vice president of Retail, explains, “Combining the latest in Apple technology with the creative passion of the local community, this new store will build on the extraordinary connection we have with our customers in Korea. Our team members are excited to welcome in customers and help them discover the latest in our products and services, including the iPhone 15 lineup.”

The tension between the CDO and the CISO: The balancing act of data exploitation versus protection
Data is the most valuable resource for the global enterprise. For any company wanting to remain relevant in today’s competitive business landscape, data needs to be at the center of every business decision, allowing the C-suite to review initiatives, make real-time decisions and if necessary reverse actions. A quick response fueled by real data insights will power and improve the customer experience and product offerings while driving lower prices through better efficiency. Ultimately, this will improve the bottom line and deliver successful outcomes for many organizations.
However, to unlock the true value of data, it is equally important that organizations ensure that confidential data is always secure. To achieve this, the Chief Information Security Officer (CISO), who acts as the gatekeeper to data to ensure it is compliant and secure, and the Chief Data Officer (CDO), who aims to unlock and exploit data, have different and competing priorities, yet they must be able to work together towards a common goal to achieve the strategic objectives of the organization and deliver great customer and business outcomes. There are significant benefits to be had when these two role holders work together and huge drawbacks when they don’t.
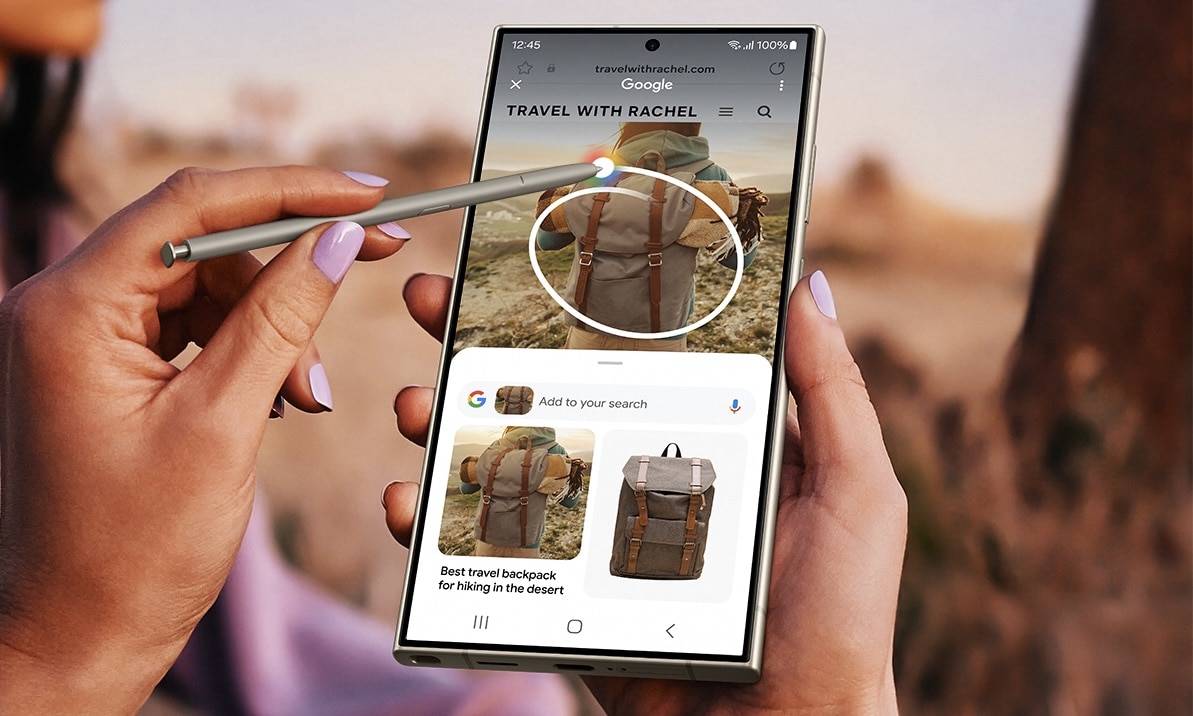
Samsung unveils Galaxy S24 Android smartphones with innovative Galaxy AI -- pre-order yours today!
Samsung today announced its latest flagship smartphones, the Galaxy S24 Ultra, Galaxy S24+, and Galaxy S24. These devices are notable for utilizing the company's innovative Galaxy AI technology. This development signals the beginning of a new era in mobile experiences, where AI is expected to revolutionize user interactions with their devices.
The Galaxy S24 series introduces advanced features for enhancing communication. The series offers barrier-free communication with intelligent text and call translations. The 'Live Translate' feature provides two-way, real-time voice and text translations within the native app, eliminating the need for third-party applications. This feature ensures privacy as it is powered by on-device AI. Additionally, the 'Interpreter' feature facilitates instant translation of live conversations on a split-screen view, functioning even without cellular data or Wi-Fi.


