
TP-Link launches Deco BE63 BE10000 Tri-Band Wi-Fi 7 Mesh System
TP-Link has launched the Deco BE63 BE10000 Tri-Band Wi-Fi 7 Mesh System, and it looks friggin’ incredible! Designed for homes packed with many devices, the Deco BE63 offers tri-band speeds up to 10Gbps, ensuring seamless internet coverage across spaces as large as 7,600 square feet. This versatility makes it suitable for different housing types, from apartments to large multi-level homes.
The Deco BE10000 stands out in the Wi-Fi 7 mesh system market, providing gigabit speeds of up to 5.2Gbps on the 6GHz band, 4.3Gbps on 5GHz, and 574Mbps on 2.4GHz. These speeds are delivered across 8 simultaneous streams. Its performance is significantly enhanced by features such as Multi-Link Operation, a broad 320MHz band, and advanced 4K QAM technology, making it 3.6 times faster than Wi-Fi 6/6E routers. The new 6GHz band offers ample bandwidth with minimal congestion and interference, ensuring a smooth and reliable connected experience.
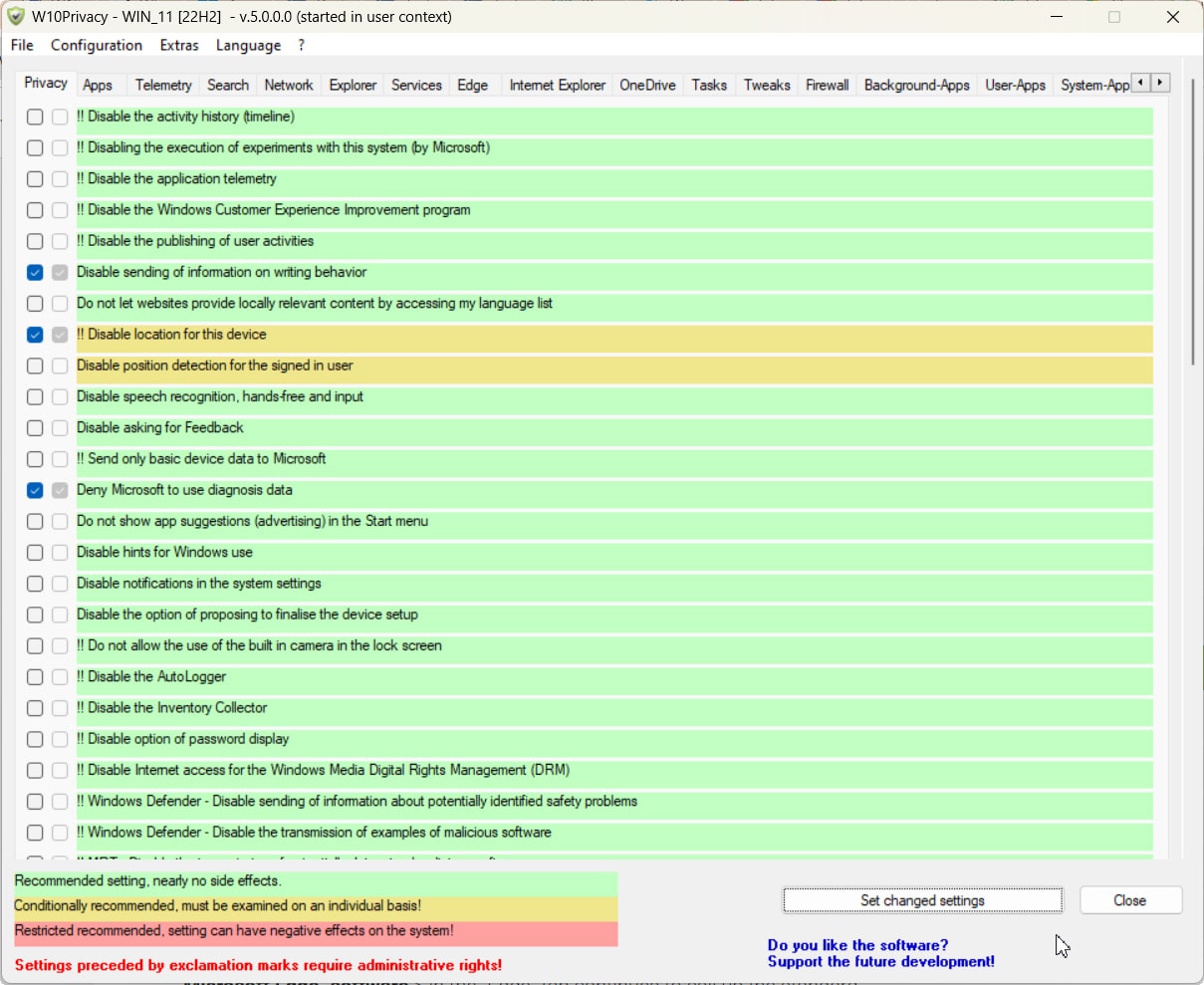
Win10Privacy 5.0 gives you complete control over your privacy in Windows 10 and Windows 11
When it was first released, Windows 10 famously spied on users and shared all sorts of information with Microsoft. Over the years, the software giant has reigned in this behavior and introduced a wealth of privacy controls to let you manage what you share.
That said, these controls are scattered throughout the OS and finding them isn’t always easy. This is where Win10Privacy can help.

Get 'AI & Data Literacy' (worth $14.99) for FREE
AI is undoubtedly a game-changing tool with immense potential to improve human life.
This book aims to empower you as a Citizen of Data Science, covering the privacy, ethics, and theoretical concepts you’ll need to exploit to thrive amid the current and future developments in the AI landscape. The book explores AI's inner workings, user intent, and the critical role of the AI utility function while also briefly touching on statistics and prediction to build decision models that leverage AI and data for highly informed, more accurate, and less risky decisions.

Turtle Beach launches Stealth Ultra Wireless Smart Game Controller with Charge Dock for Xbox and PC
Turtle Beach has expanded its product range with the introduction of the “Designed for Xbox” Turtle Beach Stealth Ultra Wireless Smart Game Controller. This new offering, compatible with both Xbox and PC, aims to provide gamers with a variety of features and customization options.
One of the key aspects of the Stealth Ultra is its wireless connectivity. Using Turtle Beach's low-latency technology, the controller connects to Xbox consoles, Windows PCs, Smart TVs, and Android mobile devices via Bluetooth. The controller is also equipped with tactile microswitches, which are claimed to offer faster response times and a longer lifespan compared to standard controller buttons. Additionally, the AntiDrift thumbsticks are designed to reduce controller drift and improve control accuracy.

Putting individuals back in charge of their own identities
From letting hotels keep copies of our passports to handing over IDs for car hire or air travel, we seldom think twice about the implications of physically sharing our identity documents. By now, we’ve gotten accustomed to exchanging personal information in return for a product or service we value -- but we need to be more vigilant at a time when identity fraud is jumping as much as 37 percent.
Proof of a person’s identity is the key to accessing goods, services, financial accounts, and opportunities -- which makes identity a valuable target, motivating fraudsters to try to gain our trust to trick us into disclosing our personal information so they can impersonate us. They also hack into identity databases that store personal information of millions of consumers. As a result, the frequency of data breaches has increased exponentially. In fact in 2022 alone, identity theft reached a staggering $42 billion in the US.

Demand for developers remains high
Despite difficult economic conditions, software development and quality assurance skills remain a priority for businesses, according to a new study.
Research from the Qt Group looks at the number of vacancies for 'software development', 'software testing', 'software engineering', and 'quality assurance' positions at 30 tech companies which have made the most redundancies this year.

Brits reach for the phone when seeking support from businesses
New research finds that 69 percent of British adults will contact a business via phone call first before trying other methods when seeking assistance.
The study from telecoms company Gamma Communications shows 38 percent of 2,000 people surveyed say direct phone calls are their preferred method of communication with businesses over other channels such as emails, web chats, social media and video calls.

Number of cyber extortion victims up by 46 percent
The cyber extortion threat landscape continues to evolve quickly and the past 12 months have seen the number of victims globally increasing by 46 percent, marking the highest numbers ever recorded.
A new report from Orange Cyberdefense shows large enterprises were the victim in the majority of attacks (40 percent), with those employing more than 10,000 people seeing a steady increase.

'Go f*@k yourself!': Elon Musk hits X-boycotting advertisers with profanity-laden attack
X CEO Elon Musk has used an appearance in New York to hit back at the growing number of advertisers opting to avoid the social platform. In recent weeks, there has been a mass exodus of big names such as Apple, Coca-Cola and Disney following concerns about antisemitism.
In mid-November, Musk endorsed an antisemitic tweet posted by another user, something he has since tried to walk back from, describing it as one of the worst posts he'd ever made. Unsettled, companies pulled advertising from the service, ultimately leading to Musk to implore them to "go fuck yourself".

Kick Microsoft Windows 11 to the curb and switch to 4MLinux 44.0 today
4MLinux 44.0 series has just marked a significant milestone by achieving stable status. This new release packs a powerful suite of applications and functionalities, aiming to enhance both productivity and entertainment for its users.
At the core of document editing and office tasks, 4MLinux 44.0 offers LibreOffice 7.6.3 and GNOME Office, including AbiWord 3.0.5, GIMP 2.10.34, and Gnumeric 1.12.55. These applications provide a comprehensive and efficient environment for handling a wide range of document formats and creative tasks.
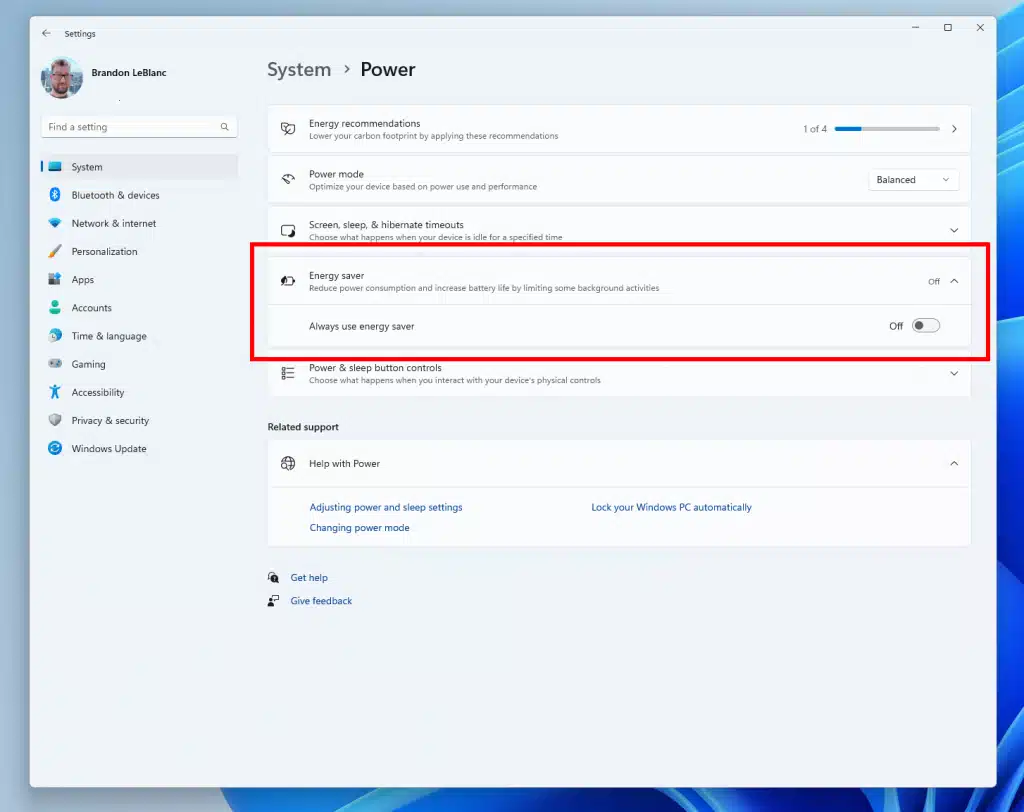
Experimental new Windows 11 feature aims to significantly boost PC battery life
Microsoft has released a new Insider build for testers in the Canary Channel. Build 26002 includes changes to the taskbar and system tray, but the standout feature is a new Energy Saver tool.
This experimental inclusion offers an "easy way to extend battery life and reduce energy use by trading off some system performance."

Windows 11 Build 23595 moves the Copilot icon to where it always should have been
Microsoft has released Windows 11 Build 23595 for those Insiders in the Dev Channel. This new flight comes with the usual selection of changes, improvements and fixes, including shifting the location of the Copilot AI icon.
Microsoft has taken the wise decision to relocate the icon from its current position next to the search box, to the right side of the system tray on the taskbar. The reason for this it to "make the entry point to Copilot more clear and easily accessible by being closer to where the Copilot pane opens."

TEAMGROUP unveils T-CREATE CinemaPr P31 USB-C SSD
Today, TEAMGROUP unveils the T-CREATE CinemaPr P31 Portable External SSD. What sets the CinemaPr P31 apart is its innovative design that allows it to be mounted to DSLR cameras. It includes unique 12 1/4" screw holes, complete with a bundled screw set compatible with all standard 1/4" screw hole cages. The ability to mount the SSD in multiple directions makes it incredibly adaptable to various shooting environments. Plus, its compact size and light weight of just 110g make it an effortless addition to any photographer or videographer's toolkit.
But the T-CREATE CinemaPr P31 is more than just an elegant piece of hardware. Its promises respectable performance, supporting high-speed data transfer over a USB Type-C interface, which is essential for professionals working with 6K or 8K resolutions. The storage capacity is impressive too, offering up to 4TB of space. That's enough to hold around 960 minutes of 4K 60 fps video.

Apricorn Aegis NVX: A rugged, super-fast, hardware-encrypted solid-state drive that fits in your pocket [Review]
If you have personal files that you want to be able to access when on the go, there are a couple of concerns you may have. Firstly, you may not fully trust cloud providers to keep your files safe and secure. Secondly, you might be worried about the risks associated with storing your files on a USB memory stick, as it could be easily lost or stolen. Fortunately, there is a solution that addresses both of these concerns: the Aegis NVX.
This rugged, 256-bit AES XTS hardware encrypted USB drive offers the best of both worlds for accessing personal data while maintaining security. Unlike cloud providers, you have complete control over your files as they are stored directly on the internal NVMe SSD, eliminating the need to rely on third-party services.

Harmonizing human insight with AI: The future of tax and finance in the digital era
In common with many industries, the digital transformation era has ushered in a paradigm shift in the tax and accountancy sectors. This has placed automation and artificial intelligence (AI) at the center of operational innovation, efficiency and competitive advantage. In doing so, these and other technologies are redefining the way industry professionals approach their work, with profound implications for the future.
Among the key questions this creates are: what does this all mean for human skillsets and expertise, and how can businesses balance these changes with uniquely human capabilities, ensuring that one complements the other? In looking for answers, there are several key areas to consider:


