
Only 14 percent get back all their data after a ransomware attack
New research shows that only 14 percent of businesses get back 100 percent of their data following a ransomware attack -- even if they agree to the ransom demand.
The study sponsored by Zerto and conducted by Enterprise Strategy Group also reveals that nearly 60 percent of organizations reported an impact to regulated data, such as personally identifiable information, in successful ransomware attacks.

IBM helps put AI into space
AI seems to be just about everywhere at the moment and it seems that there's no escape from its reach, even beyond the confines of the Earth.
IBM is announcing a new partnership with space AI leader, Ubotica Technologies, that will use IBM cloud infrastructure and watsonx.ai components, to simplify the process for developers to deploy AI applications to satellites and generate insights from data on the edge in space.

You can't win: Learning to live with security pessimism
Cybersecurity can, at times, feel like a thankless and invisible task. The punishment for a mistake is immediate and ruthless, the reward for success next to non-existent, because how do you recognize the absence of a breach? But this isn’t a new scenario; the IT industry has dealt with this outlook for decades. The job of an IT department is to be invisible, but when something does go wrong all eyes are inevitably on them to fix it.
In a threat landscape where there exists a constant push to innovate, adapt and breach, there are only three possible outcomes for the IT industry: defeat, indefinite struggle, or complete structural collapse.

Get 'AI for Marketing and Product Innovation' (worth $17) for FREE
AI for Marketing and Product Innovation offers creatives and marketing professionals a non-tech guide to artificial intelligence (AI) and machine learning (ML) -- twin technologies that stand poised to revolutionize the way we sell. The future is here, and we are in the thick of it; AI and ML are already in our lives every day, whether we know it or not. The technology continues to evolve and grow, but the capabilities that make these tools world-changing for marketers are already here -- whether we use them or not.
This book helps you lean into the curve and take advantage of AI’s unparalleled and rapidly expanding power.

Nigerian princes are back -- now with the help of AI
Emails from supposedly wronged and robbed Nigerian nobility asking for help in exchange for a payout of millions were one of the very earliest email scams.
For a while 'Nigerian prince' emails, also known as '419 scams' in reference to part of the Nigerian Criminal Code relating to fraud, were a regular feature in most people's inboxes.

Google updates Android Auto with support for WebEx by Cisco, Zoom, Prime Video and more
Android Auto has long been about much more than getting from A to B, and there has been support for various messaging and music apps for some time. But now Google has announced a new update that not only expands entertainment options, but also allows for remote meetings while on the road.
The addition of support for WebEx by Cisco and Zoom sees Android Auto branching out into completely new territory, so you can engage in an audio-only meeting when driving. The company is also adding the Prime Video app for in-car entertainment, the Vivaldi browser app, as well as the Weather Channel app, and expanded support for digital car keys.

Sony BRAVIA XR A95L Google TV offers PlayStation Remote Play gaming on QD-OLED 4K HDR display
Today, Sony Electronics Inc. shocked the gaming community with a major announcement. You see, the company revealed that the BRAVIA XR A95L QD-OLED 4K HDR Google TV will now support PlayStation Remote Play. A remarkable development, the BRAVIA XR A95L Series TV stands out as one of the pioneering Android TVs to leverage this innovative feature. This means players can remotely access their PS5 and PS4 games right from the comforts of this television.
The PlayStation Remote Play isn’t just a superficial add-on. It is a bridge for users to dive into their favorite PS5 and PS4 titles, no matter where their consoles might be stationed. What makes it even more compelling on the BRAVIA XR A95L Series TV is the fluidity it brings. Gamers can transition between their devices seamlessly, picking up their game from the exact point they paused. As long as there’s a stable high-speed internet connection and a device like the BRAVIA XR A95L on hand, players have the liberty to tap into the vast PlayStation universe from virtually any corner of the world.

Linux Mint Debian Edition (LMDE) 6 'Faye' Beta now available for download
Today marks the highly anticipated Beta release of Linux Mint Debian Edition 6. Codenamed "Faye," LMDE 6 derives its lineage from Debian 12 Bookworm. Linux enthusiasts are always eager for fresh Mint releases, and this one promises a host of new features and fixes. Keep in mind, as with most beta releases, there are several known issues.
For heightened security, LMDE has opted to lock the root account by default. Those needing to access the recovery console or wish to log in as root will need to set a new password for root using the sudo passwd root command.
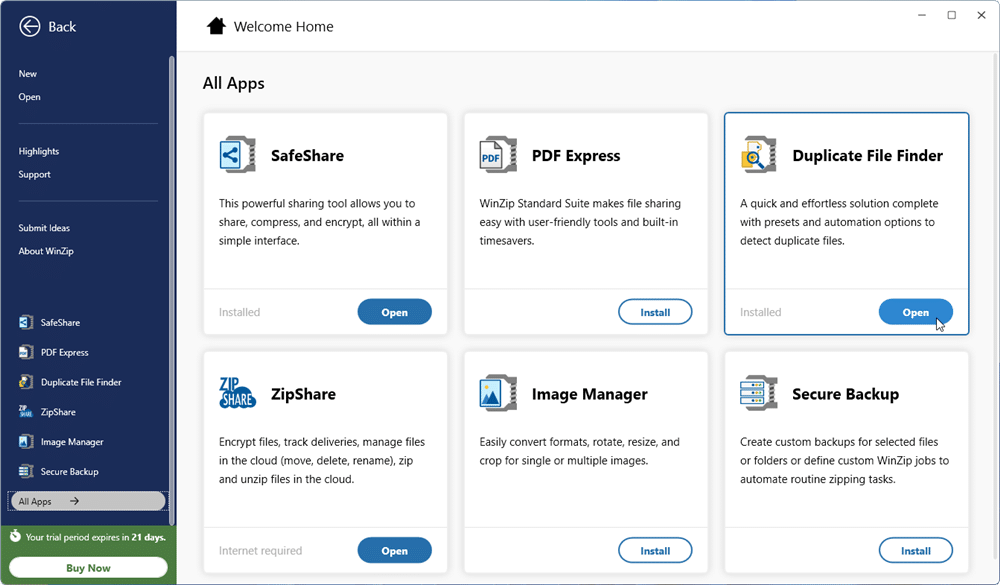
WinZip 28 unveils redesigned home screen, ability to scan archives for threats
Corel has unveiled WinZip 28, a major new release of its Windows compression tool. Two major features of note stand: a new malware scan tool for archives, and a redesigned home screen.
In addition, several existing tools -- including WinZip Courier and WinZip SafeShare -- gain new and improved features. The modern home screen -- available in all editions of WinZip -- serves several purposes, from one-click updates to accessing help and support. It’s also designed to make it easier to explore new productivity features and tools.

Making IT sustainability a part of the digital employee experience
Sustainable IT is no longer merely a good practice driven by customer demands; it has evolved into an imperative in response to shifting employee expectations and corporate responsibility around ecological consciousness. In today's digital workplace landscape, more than 80 percent of leaders are placing a heightened emphasis on environmental sustainability. Cloud providers, executives, software engineers, IT teams and even corporate boards of directors are increasingly thinking green because of the impact that adhering to environmental, social and governance (ESG) standards will have on our future and the next generation of leaders. And on top of that, the business landscape is incentivizing green behavior. A recent survey by CloudBolt found that two-thirds of IT leaders say cloud provider’ sustainability initiatives are a key factor in determining with whom they do business.
Companies who drive sustainability transformation also enhance corporate reputation and performance, appealing to environmentally conscious customers. Firms adopting sustainable practices, like energy optimization, realize significant cost reductions. Integrating Sustainable IT into the digital employee experience is also a pivotal element of this transition, fostering a gratifying workplace for employees.

90 percent of testing professionals are concerned about AI bias
A new survey of over 3,000 digital testing professionals reveals concerns about bias, copyright issues and privacy.
The study from testing specialist Applause shows that 90 percent of respondents expressed concern, with 25 percent 'very concerned' that bias may affect the accuracy, tone or relevance of the content produced by AI.

AI for one and SaaS for all
The rapid adoption and proliferation of SaaS apps has in many cases served to make the job of IT teams more complicated as they seek to manage threats and control costs.
SaaS management specialist Torii is launching a new SaaS Management Platform (SMP) that offers IT teams a one-stop-shop to automate time-consuming tasks, cut their SaaS spend, and obtain quicker, actionable insights.

Get '10 Machine Learning Blueprints You Should Know for Cybersecurity' (worth $39.99) for FREE
Machine learning in security is harder than other domains because of the changing nature and abilities of adversaries, high stakes, and a lack of ground-truth data.
This book will prepare machine learning practitioners to effectively handle tasks in the challenging yet exciting cybersecurity space. It begins by helping you understand how advanced ML algorithms work and shows you practical examples of how they can be applied to security-specific problems with Python -- by using open source datasets or instructing you to create your own.

Western Digital launches WD_BLACK SN770M M.2 2230 SSD for handheld PC gaming devices like Steam Deck and ASUS ROG Ally
Western Digital has rolled out a top-tier, high-functioning M.2 2230 SSD specifically tailored for handheld PC gaming devices under its WD_BLACK branding. Called “SN770M,” this NVMe SSD is very fast and offered in several capacities. Owners of Steam Deck, ASUS ROG Ally, and similar devices will want to check this drive out.
Designed in a compact M.2 2230 form-factor, the WD_BLACK SN770M NVMe SSD offers gamers an opportunity to increase their handheld gaming PC's internal storage, ensuring they carry their expansive game collection wherever they wander. The drive boasts a myriad of features, ranging from PCIe Gen 4.0, Western Digital's nCache 4.0 tech, to Microsoft's DirectStorage support, propelling game installations and level loads with an impressive speed of up to 5,150 MB/s.

The changing role of the CTO [Q&A]
Between the rise of competition, the changing regulatory landscape, the evolution of AI and the rise of new threat actors, the role of the CTO can be a challenging one.
What characteristics are needed for the role and how can incumbents ensure that it remains relevant? We spoke to Ajay Keni, CTO at OneSpan, to find out.