
WhatsApp's new privacy policy reveals it will share data with Facebook for targeted user ads
The ever-popular messaging tool WhatsApp is to start sharing more user data with its parent company Facebook. The updated privacy policy means that WhatsApp will now share users' phone numbers with Facebook to "offer better friend suggestions and show you more relevant ads".
The updated policy also communicates the fact that end-to-end encryption has rolled out, but it is the privacy side of things that will be of greater interest to many people.

Why encrypting virtual machines is so challenging
Virtual Machines have been mainstream for some time, and many IT managers think they have good management processes in place; they know where their machines are, their status, and the function they are performing. But is that enough? Whilst virtual machines (VMs) allow an IT infrastructure to be extremely agile in Private, Public and/or Hybrid Cloud environments, they also create opportunities for weak points, where data can be compromised.
Encryption is one of those major weak points, where VMs can be deployed without an encryption policy being followed, subverting compliance, and leading to machines in a live environment that lack the required protection. More often than not, those VMs will contain sensitive data.

Google Compute Engine lets users create their own encryption keys
Until now, anyone using the Google cloud platform, Google Compute Engine, was forced to use encryption keys generated by Google. Clearly this spooked a lot of people, and there have long been calls for users to be granted greater control of security.
Now this is happening -- users are able to provide their own encryption keys. Customer-Supplied Encryption Key (CSEK) are used to provide a second layer of security, on top of the Google-generated keys that are used by default.

Privacy alert: Maxthon web browser sends private data about users to China
In the world of web browsers, there are four or five big names to choose from but no end of smaller alternatives. One such browser is Maxthon, and security researchers have just discovered that this Chinese-produced browser is transmitting a wealth of data about users back to China.
Researchers at Fidelis Cybersecurity and Exatel found that Maxthon frequently sends zip files to Beijing over HTTP and this contains a terrifying amount of data about users' browsing habits. The ueipdata.zip file incudes, among other things, details of the sites visited by users, the applications they have installed, and what searches have been performed.

CryptoDrop can stop ransomware early on in the encryption phase
New software, designed by scientists at the University of Florida (UF), just might be the answer to thwarting the ever-growing problem of ransomware.
Ransomware is a form of malware used by cybercriminals to exploit users into paying significant sums of money to retrieve their own files. When an infection happens, the files on a user’s system are encrypted by the virus and the only way to regain access to those files is by paying a ransom to the hackers behind the attack.

The Halvening means that bitcoin mining rewards just dropped by 50 percent
It just became significantly harder to mine Bitcoins. The halving event rolled around yesterday, July 9, and means that the reward for mining just dropped by 50 percent. The cryptocurrency is generated by machines around the world 'mining' for new bitcoins.
Rewards of bitcoins are handed out for giving over computing power to process bitcoin transactions. It's a very, very slow way to make money -- and it just got a whole lot slower. While there were previously 25 bitcoins (around $16,000) available globally to miners every 10 minutes, the figure is now just 12.5 bitcoins. But what does this mean for the digital currency?
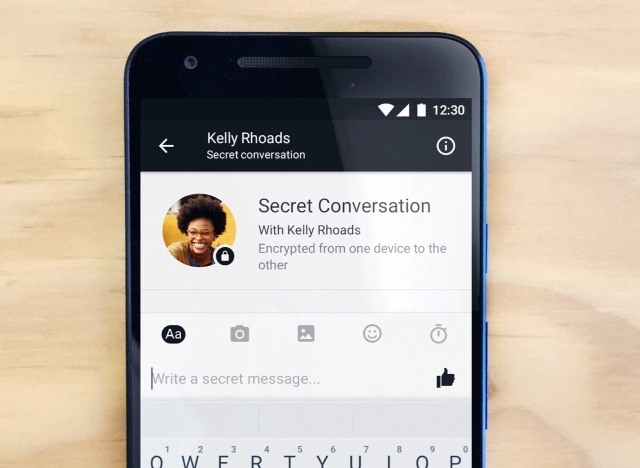
Facebook Messenger ups security with end-to-end encryption in 'secret conversations'
Continuing in its relentless drive to take over the world of messaging, Facebook Messenger is gaining end-to-end encryption. To start with, the security feature is only rolling out on a 'limited test basis' but if feedback is positive, it will get a wider airing.
Facebook says that the move comes in response to requests for additional security options to protect discussions about sensitive matters, saying that security and privacy experts have been involved in the implementation of the feature.

Court papers show Silent Circle's privacy-boosting Blackphone was an unmitigated sales disaster
With so much focus now placed on privacy and security, you would have thought that the Blackphone from Silent Circle would have been a roaring success. But documents from a court case with former partner Geeksphone reveal that there have been just a handful of sales, and revenue is hundreds of millions of dollars lower than expected.
Silent Circle found itself in court after Geeksphone complained that it had not received a $5 million payment agreed as part of a buyout. Geeksphone had helped to build the original Blackphone, and Silent Circle went on to buy the Spanish company's share before launching the Blackphone 2. But sales were much, much lower than expected, leading the company to describe its hardware business to "be a significant financial drain".

More than half of Android phones are vulnerable to encryption bypass
A newly revealed vulnerability on Android phones is able to bypass the full disk encryption on over half of devices.
The attack, demonstrated by Israeli security researcher Gal Beniamini, can allow an attacker to break through the levels of trust and privileges that are intended to ensure only legitimate code can access secret material, such as DRM keys or disk encryption keys.

Use of encryption in enterprises is at all time high
The use of encryption in global organizations is now at an all-time high, with 41 percent using it extensively today -- a seven percent rise over last year.
This is among the findings of a Global Encryption report from Thales e-Security and the Ponemon Institute which shows that businesses are taking action to guard their sensitive data.

Mozilla uses emoji game Codemoji to teach about encryption
The world of technology relies on encryption. Everything from private messages to online payments are secured in this way -- but how does it all work? Mozilla has come up with a way to teach people about encryption, combining gaming and emoji into a useful learning tool.
Codemoji is described as "a fun way to learn about ciphers", and while you might think that it's aimed solely at children, there's something here for all ages. The idea is very simple: letters and words are translated into emoji so they can only be read by those who understand the decryption technique.

Apple is leaving the iOS 10 kernel unencrypted... to increase security
Each new version of iOS is eagerly awaited, and at its Worldwide Developer Conference (WWDC) Apple unveiled a preview of iOS 10. Much has been made of the new features, but developers probing the operating system are making a surprising discovery. The kernel of iOS 10 is unencrypted.
In the current climate of security-awareness, this might seem like something of an unusual decision. But Apple says that the change has been made to improve performance, and it could even help to increase security.

Apple: Developers must use App Transport Security by 2017
Apple has announced that the deadline by which app developers must enable App Transport Security (ATS) in all apps is 1 January 2017. ATS is not a new feature of iOS 10, having been introduced in iOS 9 and it increases the security of data transferred over the web by apps.
With ATS enabled, apps are forced to use the far more secure HTTPS rather than HTTP, and this is something we've become accustomed to looking out for when browsing the web. At the moment, developers are able to disable ATS, but from the end of the year this will no longer be possible.

Encryption-focused Apple File System (APFS) replacing HFS+ on macOS, iOS, tvOS, watchOS
Apple was quite boisterous at WWDC today regarding its operating systems and services. Quite frankly, I was blown away at all the ways the company is looking to improve its customers' lives, but some folks were apparently underwhelmed. Oh well, you can't please everyone, I suppose.
For some reason, Apple was fairly quiet about one huge change -- it is replacing the HFS+ file system. Based on the more-than-30-year-old HFS, it is apparently time to move on. What is the upcoming file system called? The unimaginatively "Apple File System". The encryption-ready file system will be used on macOS, iOS, tvOS, and watchOS.

Decade-old 'forbidden attack' vulnerability affects HTTPS Visa sites
A number of supposedly secure HTTPS sites owned by Visa are vulnerable to what has been dubbed the 'forbidden attack'. The security flaw makes it possible for hackers to inject content and code into sites, as well as opening up the possibility of performing man-in-the-middle attacks.
A team of researchers have published a paper that shows how 70,000 HTTPS servers were vulnerable to the attack, and 184 were found to be particularly at risk. While many of the affected sites have since been patched, sites belonging to Visa and Polish banking associate Zwizek Banków Polskich remain insecure because of reusing a cryptographic nonce in contravention of the TLS protocol (hence the 'forbidden' tag).