
What you need to know about moving monoliths to microservices
There are many benefits to the "monolithic" application model -- especially at the beginning of a project -- but monoliths can become unwieldy over time, limiting companies’ ability to move quickly and flexibly in today’s dynamic business environment.
To overcome this and other issues, companies like Amazon, eBay and Netflix are leveraging microservice architectures. The microservices model has been defined by Martin Fowler, author, software developer and an early supporter of microservices as "an approach to developing a single application as a suite of small services, each running in its own process and communicating with lightweight mechanisms, often an HTTP resource API."

Clean and optimize your PC with Black Bird Cleaner
Black Bird Cleaner is a suite of PC cleanup and optimization tools, available in a cut-down free version and a $24.95 Pro build.
The program requires installation, but takes up minimal hard drive space -- barely 1MB -- and doesn’t install any system components.
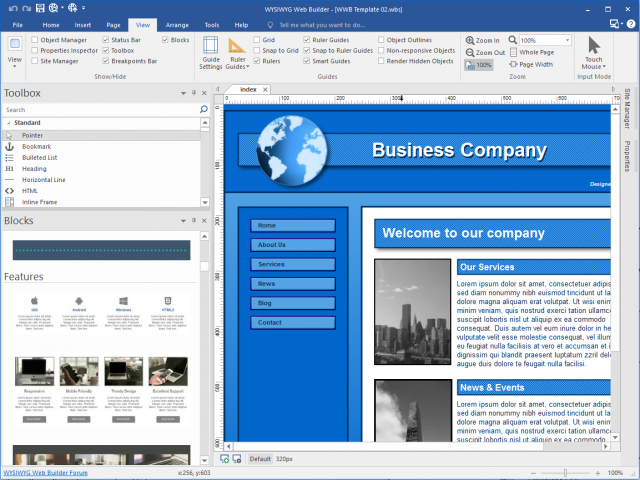
WYSIWYG Web Builder 12 makes building websites easier than ever with new Blocks feature
Pablo Software Solutions has released WYSIWYG Web Builder 12, a major new version of its DTP-style web building tool for Windows users.
Version 12 introduces over 125 new and improved features, with one brand new addition in the form of Blocks, a new option for quickly adding predefined blocks of objects to the workspace. Other highlights include a photo collage tool, CSS flexbox support and new Easy Mode feature.

New solution integrates software asset and security management
Keeping track of software licenses and ensuring that products are kept up to date with the latest patches can prove a chore for businesses.
Software management specialist Flexera Software is launching a new product that integrates asset and security management for better vendor, financial and risk management, as well as operational efficiency and optimization.

Citrix launches Receiver client for Samsung Galaxy S8 DeX
Citrix wants a part of that tasty Samsung Galaxy S8 DeX cake, and it just announced a new software client to make sure it gets it.
The newly announced Citrix Receiver is a free to download client which allows users fast access to XenDesktop and XenApp installations. The client allows users to access applications, desktops and data easily and securely, the company says.

Hide files or folders inside JPEGs with FileFriend
FileFriend is a tiny portable toolkit which can split, join, encrypt or hide your target files in a JPG.
The program organizes its simple interface into four tabs: Split, Join, Encrypt and "JPK" (pack a file or folder inside a JPEG).

Teradata delivers portable database licensing for the hybrid cloud
Whilst cloud and hybrid models offer undoubted flexibility, they can lead to problems when it comes to keeping track of software licenses.
Analytics solutions company Teradata is looking to cut through the confusion with the launch of a new simplified licensing model. This aims to deliver portability for deployment flexibility, subscription-based licenses and simplified tiers with bundled features.

Welcome to the 'post-app era'
How often do you use apps? You probably open a handful on a daily or even hourly basis. You probably ignore the rest.
You’re not alone. Gartner research shows that users from the US, UK and China used just six to 10 apps each month in 2016. This represents a six percent year-on-year decrease and has led Gartner to declare the "post-app era."

Outdated programs main cause for security incidents
Did you update Flash on your PC? How about Java? According to cybersecurity firm Avast, you probably didn't -- and that's the number one cause of cybersecurity incidents.
Avast just released a new report, entitled Avast PC Trends Report January 2017, which is based on insights from the company’s AVG TuneUp product, and says that more than half (52 percent) of the most popular PC applications have outdated installations on consumers' devices.

Bear 1.1 unveils loads of improvements, including improved tagging, export
Shiny Frog has released Bear 1.1, its Evernote-baiting, notetaking app for Mac and iOS. Mac users gain Touch Bar support and wider drag-and-drop support, while iOS users can now take "smart" web clippings using the app extension.
Although Bear operates a two-tier platform, with free and Pro licenses available, the update treats both equally, providing new features for both groups of users as it aims to stake a claim in the note organizing marketplace.

OnePlus announces early access program for official OxygenOS builds
OnePlus is among the few smartphone makers that let their fans test software updates before they're released to the public. Its beta program has two such "streams", or rings if you prefer, which give members access to closed or open betas. But now the company is adding one more.
OnePlus just announced the MP Early Access Program, a new stream to test builds that it deems ready for prime time before they're pushed to the official -- MP -- channel. Why? Simple: to catch any bugs that might have slipped through.

SAS: Open source software comes with hidden costs and problems
Open source technologies are great for organizations, but they're far from perfect. As a matter of fact, many of the open source technologies in use today come with hidden costs and problems. This is according to a new report by SAS, which was created on a poll of 300 executives across the UK and Ireland.
These costs and problems mostly revolve around training staff, as well as recruiting, or replacing employees with essential data science skills.

Kdenlive is a powerful video editor for… Windows?
Kdenlive has been a popular non-linear video editor in the Linux world for a very long time, but the developers have also recently released a first Windows port.
The build doesn't skimp on functions: there's a full multi-track timeline and an array of effects and transitions to explore.

Intel's first bug bounty program has $30,000 top reward
Security researchers can make a lot of money by reporting bugs to software and hardware vendors. Microsoft, for instance, pays up to $15,000 for vulnerabilities in Office Insider, while Intel, through its first bug bounty program, takes things up a notch with a top reward of $30,000.
Intel's first bug bounty program was announced on HackerOne, and targets firmware, software and hardware products. Hardware vulnerabilities have the highest top reward, followed by firmware and then software.
Decrease in patch rates points to broken software supply chain
Vulnerabilities in software are at the heart of many security problems, providing a foothold for hackers that they can use to gain access to systems.
The latest Vulnerability Review from the Secunia Research arm of Flexera Software maps the security threat presented to IT infrastructures and explores vulnerabilities in the 50 most popular applications on private PCs.