Employees put corporate networks at risk

Digital device practices among US employees are exposing their employers to increased security risks according to a new study.
Identity management company OneLogin along with Arlington Research surveyed 1022 respondents in the US and found that 13 percent let their colleagues use a device that can access their employer's network. In addition nine percent allow their partners to access such a device, and one percent even permit their children to use it.
Password sharing is widespread too, with 20 percent of employees sharing their work email password, and 12 percent sharing passwords to other work applications. Nearly half of all employees are unaware of company policies around the sharing of passwords. Mobile device security is also lax, one in five employees admit not having any security software on their work devices, beyond that shipped with the operating system.
"Security breaches are a near-daily occurrence in the news. Given that it takes only one compromised account to lead to a breach, these lax security practices are troubling, especially when you consider that they could take place at your bank, at your children’s school, or in your local government. A breach at one location can lead to others, especially with bad password habits like password reuse," says Alvaro Hoyos, chief information security officer at OneLogin. "Technical controls should be put in place to ensure only authorized workers are accessing data securely and these should be reinforced with security awareness efforts as well. For example, using single sign-on and identity management solutions to enforce role based access and step up authentication establishes a strong security foundation, and coupling that with periodic security awareness training or simple reminders, strengthens that foundation".
OneLogin suggests that these threats can be managed by ensuring that security policies are easy to understand and follow, making employees aware of policies, and employing technologies like two-factor authentication.
You can see a summary of the results in infographic form below.
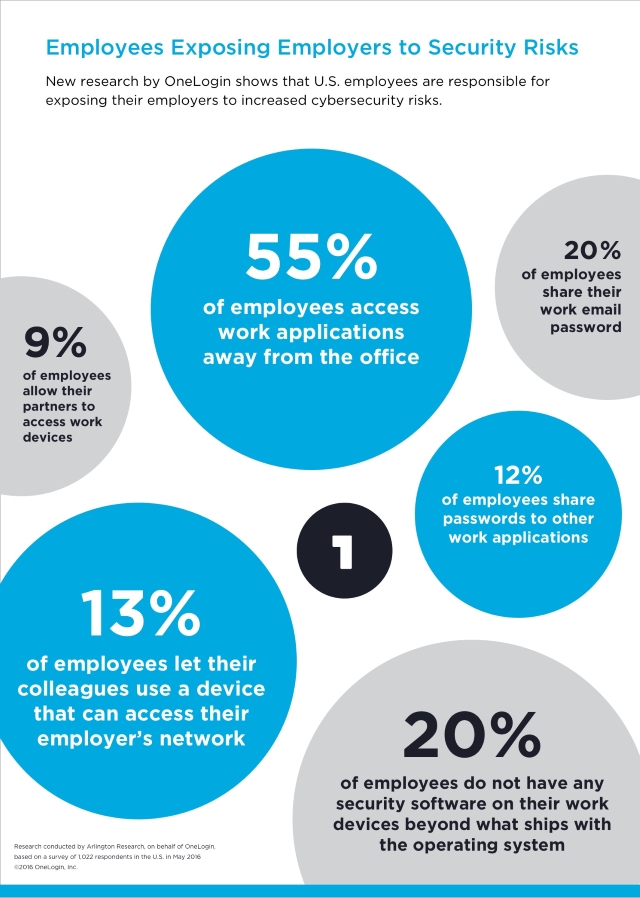
Image credit: Di Studio / Shutterstock
